Our Head of Security, and CISO Service lead, David is recognised as one of the Top 10 influencers by Thompson Reuters, and a Top 50 global expert by Kingston Technology. He is also one of the Top 30 most influential thought-leaders and thinkers on social media in risk management, compliance, and regtech in the UK.
In his role as Head of Security at QuoStar, David leads the CISO Service. The CISO service provides businesses with the cyber-security skills and experience necessary to manage the multitude of threats and rapidly changing risk landscape of today, on a flexible and cost-efficient basis. David take’s a moment to share his views on it all.
1.How did you get started in the security field and ultimately become a CISO?
David: I was around when some of the first Viruses went mainstream. Back then I worked for one of the only companies that made Multi Factor Authentication systems in the 90’s. It was “leading edge” at the time.
I built and ran one of the largest commercial remote access platforms using Multi Factor Authentication. Then I ran Infosec for some FTSE 100 companies, one of which was the largest private trading network in the world – trading 3.5 trillion dollars a day. Another was managing Global Security Services Operations Centres (24/7) across 4 continents, where most of the customers were FTSE 250.
2. What do you enjoy most about working as a CISO Service resource/consultant?
David: Meeting challenges of audit, due diligence, and breach management.
Audit is getting more involved and complex and due diligence is often 300-400 questions and an “interview” with the compliance department of potential customers.
Breaches is about managing with around 10% knowledge of the situation and making decisions in a very short time for the best outcomes – while ensuring buy in from the board. They always seem to happen on Friday evening!
3. As Head of Security, what challenges or issues do you regularly see in small and mid-market businesses? Why do you think the same issues keep occurring?
David: 1. Robust management of access and privilege management. 2. Managing risk consistently. 3. Not aligning Cyber Security with Data protection requirements – as they overlap at a core level.
If you have control of the information assets servers and cloud, information security is much easier to manage. It enables savings in resource and effort if this happens and can demonstrate to the business control and improvement.
4. How do you think the security landscape has changed in the last five to ten years?
David: As a CISO Service lead, I believe it is manging the hybrid of internal servers and cloud – and managing the challenge of access control. The company boundary is very fluid, especially where ‘what’s company and what’s personal’ is concerned.
One of the best frameworks is ISO27001. It is good for demonstrating accountability and decision making. It also aligns with SOC2 and parts of HIPAA quite well.
5. What do you think will be the emerging risks businesses need to consider in the next 1-2 years?
David: It used to be technology first, then followed by making technology safe and compliant. Now technology needs to be safe and compliant first, and performance orientated second – along the lines of what has happened in the automotive, aerospace, building and food industries.
The risks potentially surround the technology itself not having enough security management capability, or that if it does it can be resource intensive. There’s also the globalisation of threat actors and the capability of managing multiple global data protection regulations.
More recently the US Biden government issued a memo to US Businesses in summary June 2, Stating the 5 best practices – one being Multi Factor Authentication. Other important aspects are multi-pronged backup Updates, Incident Response, external testing and network segmentation.
6. Has the Covid pandemic exacerbated security concerns or introduced new ones for businesses to deal with?
David: Probably, due to homeworking and fast transformations of moving office servers to the cloud, as well as an increase in Ransomware attacks, an increase in Data Protection legislation globally and the increase in corporate security concerns due diligence.
It has been an increasing challenge for a Head of Security. We have seen an increase in demand from due diligence enquiries, especially for more detailed homeworking policies and guidelines. So, the lines have blurred as to what is home device or a work device. The “physical office” is now the home office, and mandating rules now have to be guidelines that are appropriate – as well as using more layers of defence to protect staff and corporate assets.
7. Do you think businesses focus too much on the technical/technology element of security (e.g. AI solutions)? What other areas do they need to consider?
David: Potentially yes, without an end-to-end strategy, it makes security technology “tactics” unlikely to see a ROI, Return on Investment.
As Head of Security, I see the human element of security is also overlooked quite often. Especially when you consider that almost half of all security breaches are caused by human error. This is even more disconcerting when you consider that only 60% of employees will report a security breach too.
We are actually hosting a free webinar on that subject on 29th July 2021 at 1pm, so if you’d like to know more register for free.
8. How important is cyber-security education? What are the challenges for a Head of Security conveying the risk/educating business? Who in the business needs to receive education/training and how often?
Education is very important, as is having the appropriate training for each role ideally aligned to the companies risks – so that maximum benefits can be realised e.g. developers would require different training from HR staff, as the risk they are managing are different.
Of course, there will always be a need for baseline cyber and data protection training. You can find out more about what Security Awareness Training there is available for employers and employees in our article here.
9. Do you feel there is a security skills/talent shortage? What advice would you give to businesses to combat this?
David: I’m not entirely sure. If there is a shortage, there is definitely a misunderstanding of what skills are required.
Personally, I would align the risks and the strategy, then decide what skills are required to make it happen. It may be that companies would benefit from outside help – to formulate the strategy, and always have access to a range of skill levels onboard to achieve skills resilience.
The other issues that many companies seem to come up against are 24/7 and global, so having just one capable Security resource will not be enough to cover these time periods.
10. As Head of Security, what advice would you give to businesses who want to reduce risk and increase their security posture?
David: Manage Risk regularly with key stakeholders.
Ideally do not remove a risk or lower a risk without evidence, from at least the following e.g. a Policy, Procedure, Penetration test, Internal Audit, External Audit or risk committee approval. This will demonstrate accountability and assist in managing data protection, to enable a defensible position in the security posture.
Ensure a multi-layer approach to security. Utilise things like Access control, least privilege, Approved applications, strong email defences, layered endpoint security, centralised control of endpoints and access, plus multiple point backups.
11. If there was one security investment you could recommend to businesses what would it be and why?
David:
One piece of tech most companies aren’t using
To keep companies ahead, Secure Access Service Edge will help with Cyber security and Data Protection. The ROI is great! It releases staff time, and the payback can be in months.
One Framework
You can manage risk and accountability using ISO27001 framework. If you are not going to be certified, ISO27001 also helps align with NIST, SOC-2 and can help align some components of Data protection. It can clearly demonstrate accountability.
Training that is focused to the role in the business is most appropriate, using the “Incident” metrics to tailor training and technology requirements.
One practice
Have a data/Cyber champion in every business function so you’re able to manage threats, risk and increase incident reporting capability to enable “real-time” issue management.
We hope you found David’s current take on Cyber-Security insightful. During his career David has worked across multiple sectors, including financial services, government, utilities and FinTech, working with a variety of clients – from start-up level and SME up to FTSE 100. He previously held the role of Global Head of IT Security at BT and Radianz (formally Reuters). He’s also been responsible for managing the security infrastructure and delivery of ISO 27001 for multi-billion/trillion-dollar environments. He is also an active CISO consultant on our CISO service offering.
Challenges for IT Managers
While this change in perspective is positive, it does mean the scope of an IT Manager’s role has increased considerably and, with this, come new challenges to address.
1. Big data
Businesses are generating more data than ever. Unfortunately, most of this is unstructured so it can’t really add any value. Transforming this data into measurable and actionable insights is one of the largest challenges facing IT pros but get it right and it has the power to completely transform a business, giving greater insight into operations, customers and the wider marketplace.
2. Asset and data management
The ever-increasing number of devices in the workplace means more monitoring and maintenance. To effectively and safely deal with this, it’s crucial that the IT strategy includes appropriate information governance programs and mobile device management policies.
As well as managing the known hardware, IT Managers must also be aware of the threat of the unknown. Shadow IT, hardware and software used by staff without the IT department’s approval or knowledge, is an increasing problem in mid-market businesses. In fact, it’s estimated that the number of software programs in use is 14 times higher than thought. This can include things like using cloud file stores like DropBox or Google Drive to share files, personal instant messaging apps or online CRM solutions.
3. Data protection
Forward-thinking mid-market businesses will have already taken a ‘privacy by design’ approach, but meeting regulatory and compliance standards around data protection is a continuing concern. Customers demand – and expect – their data to be private and secure, and any potential threat can easily drive them to a competitor.
4. New technologies
While keeping up with new technology is a challenge, a greater one is working out what’s the best fit for the business and communicating the reasons why to senior leadership.
This can be a particular problem for IT Managers who don’t have a seat on the board. It’s all too easy to get swept up by the wave of new, shiny tech and become concerned that your business is missing out because others appear to be investing. Yet this is exactly the type of spend that puts the business at risk and, in turn, creates ‘bad feeling’ towards IT. It’s crucial that IT Managers advocate for ‘a seat at the table’ to address the challenge of new technology and use their experience and expertise to guide the business towards effective investment.
Equally important is proactively investing in your IT systems to ensure the business benefits from up-to-date technology that improves operations and sustains competitive advantage
5. Evolving cybersecurity threats
Cyber-security is a huge challenge, with attacks constantly growing in size, sophistication, and frequency. This rise coupled with rapidly deployed remote working solutions during COVID has led to new risks being introduced to IT environments that quickly need evaluating and controlling.
Businesses cannot take this threat lightly, as it presents a financial, reputational and operational risk. However, it’s also the area with one of the largest skills gaps – there simply aren’t enough IT security professionals worldwide to meet demand. In Europe alone, the cyber-security skills gap doubled in 2019 and two-thirds of organisations have reported a shortage of skilled or experienced security personnel.
As cyber-security is such a vast and rapidly developing area, it can be difficult for IT Managers in mid-size companies to keep up with all the latest threats whilst also managing day-to-day activity, projects and continual improvement. To address this challenge, IT Managers should consider deploying advanced technologies and services, such as SIEM and MDR, and explore co-sourcing to obtain specialist cyber-security knowledge and experience.
6. Mobile device management
BYOD is nothing new, but the introduction of multiple corporate and personal devices into the workplace during the pandemic continues to cause issues for IT Managers. The threat landscape and companies risk profiles have grown significantly and controls and so has the need to control it. Keeping users productive and engaged whilst working fulltime is going to need some focus and strategy in the medium and long-term.
7. Skills gap
IT Managers not only have to contend with a cyber-security skills shortage but, overall, there is a general gap when it comes to tech and IT skills. This has been partly driven by the breadth and pace of innovation, but also because businesses are beginning to recognise the notable role technology plays in attaining their strategic objectives and require a different skillset from their IT pros.
Businesses attribute skills gaps to lower staff productivity, fewer sales, a lack of innovation and new product development and increased operating costs. Yet, despite recognising the harm it causes, few have the processes in place to address skills gaps and do not offer formal training to technical employees to upskill.
These gaps will only continue to grow and cause further harm unless action is taken. IT Managers must convey to senior management the value of continual and strategic training for technical employees and secure budget to ensure this can happen.
However, even with training, it’s unlikely that one or two IT professionals will be able to meet all the technical and strategic skill requirements of a mid-sized business unless you’re solely focused on ‘keeping the lights on’. It can be prohibitively expensive to build out a large internal IT team and retain individuals for the long term, which is why IT managers often turn to co-sourced IT support as a way to gain the specific skills they need, often at a fraction of the cost.
8. Cloud computing
The fallout from the pandemic is only expected to further accelerate the move to the cloud and between cloud platforms, such as a shift to hybrid public and private environments. The flexibility, scalability and potential of different cloud platforms are just too greater opportunities to ignore. However, it’s important that IT Managers oversee the selection process to prevent rash decision making and budget wastage.
For those exploring new cloud-based services, it’s essential to consider security across multiple platforms. Traditionally, multiple clouds meant also managing multiple inconsistent and incompatible security systems. Now, a better option would be a cross-cloud, cloud-agnostic security platform which ensures complete enterprise-wide security, regardless of asset location.
9. Digital transformation
Digital transformation is complex, and it can be difficult to achieve success. Yet in order to prevent savvy competitors from overtaking them, businesses really need to focus their efforts in this area.
Projects or initiatives often fall on IT Managers because they’re seen as ‘tech’, but in order to achieve a successful digital transformation, the entire senior leadership needs to be engaged, establishing a clear reason for transformation and fostering a sense of urgency for making changes. The challenge for IT Managers lies in driving forward this behavioural change so digital transformation is seen as a much wider piece.
10. Hiring and retaining talent
The high demand for specific skills and a lack of suitable candidates results in fierce competition, which can make it difficult for mid-sized businesses to retain their technical talent. It’s not just a higher salary which can tempt IT pros away. Greater flexibility, upskilling opportunities, more manageable workloads and a chance to specialise – rather than the expectation to manage everything ‘IT’ – are all often cited reasons for a move.
While businesses should review their hiring and employee retention processes to identify areas for improvement, on the technical side they should also consider what skills they really need to have in-house. For example, cyber-security skills are essential, but can your business really offer the work, environment and – to be frank – the salary required to retain an expert with a niche skillset? Rather than engaging a specialist recruitment agency to find that talent, would it be more beneficial to consider other ways your business could gain access to those skills at the level you need.
11. Instilling trust
While recent events have moved IT into the heart of the business, IT Managers will need to work strategically to retain this position.
IT was hailed as a hero for helping mid-market businesses quickly make the full transition to remote working, keeping everyone running and productive. However, with people coming back into the office, IT risks becoming the villain by simply seeking to address some of the bad habits staff may have picked up during lockdown – i.e. restricting personal apps, preventing home-working until stronger security measures are in place, slow responses as the helpdesk becomes overloaded.
12. Increasing workloads
It’s positive that senior management is beginning to recognise the contribution of IT on a strategic as well as operational level, but this comes at a price for IT Managers. Not only are they typically responsible for day-to-day monitoring, maintenance and issue resolution, they also need to undertake improvement projects, create the IT strategy, investigate opportunities and generally help drive the business forward. It’s a vast set of responsibilities and often it may feel like there are not enough hours in the day to do it all.
13. Outsourcing
The combination of hiring challenges, skills gaps, trouble retaining talent and increasing workloads will lead many businesses to consider outsourcing or co-sourcing.
While this is usually necessary to meet the growing requirements of mid-market businesses, it often raises concerns around reliability, accountability and security. IT Managers can typically be responsible for assessing the suitability of third-party partners, vendors and suppliers so it’s vital they have a strict assessment process in place so they can feel confident in the engagement.
An IT Manager’s role is continually evolving and therefore becoming more challenging. As the scope of responsibilities and accountability becomes wider, new challenges for IT Managers will crop up alongside those which have held fast for some time.
A number of these challenges can be addressed by IT retaining a central position in the business and having a voice at the decision-making table. IT Managers cannot address these challenges solely by themselves, they need the support of the entire senior leadership team
What is warshipping?
Warshipping is a type of cyber-attack in which criminals use physical package shipping services to send malicious hardware to a victim or hide malicious hardware on the business premises. This hardware can be remotely controlled by the attackers and used as a staging post for further attacks.
How does the warshipping cyber-attack work?
Warshipping uses custom-built devices consisting of cheap, easily available components: a single board computer (£30), phone battery (£15) and IoT modem with 3G connectivity (£35). The resulting device, or ‘battle package’, can be smaller than the palm of your hand and, once configured, is easily concealed and shipped to a target.
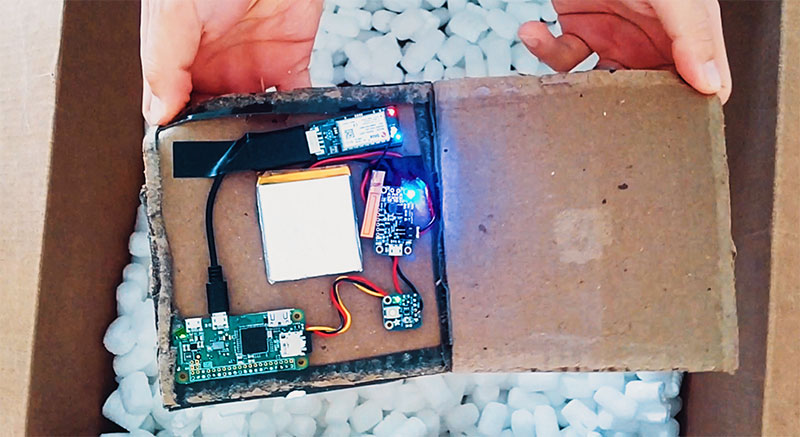
Whilst an attacker needs some technical knowledge to assemble the loose components into the battle package, it’s easy to imagine entrepreneurial criminals soon selling pre-built machines on underground forums. If this were to happen, the threat to businesses would dramatically increase as the attack becomes available to the masses.
Once a battle package is shipped, the modem regularly transmits GPS coordinates to the attacker’s command and control server. This allows the attacker to identify when the device has arrived and start full deployment. Of course, the device doesn’t have to come in the post – it could be planted into a toilet roof or hidden in a bush outside of reception.
Deployment involves one of two things:
- The device will imitate the existing Wi-Fi router, harvesting the login credentials of users who attempt to connect to the rogue access point.
- The device will intercept packets, looking for a handshake (the connection between a device and the Wi-Fi access point). The encoded handshake can then be sent back to the command and control server to be reverse-engineered and used to gain access to the network.
What threat does warshipping pose?
Once the attacker has access to the network, they can exploit vulnerabilities to gain deeper access. This allows for further attacks to be sent directly into the network – eventually creating a persistent backdoor for the attacker. From there, it’s possible for the attacker to gain full access to systems and information.
In business terms, a security breach like this is about as bad as it can get. Hackers would have complete control and access to your IT network and could do anything from deleting days of work with a wiper to a full-scale ransomware attack or even theft of intellectual property and client data. All of these cause massive financial damage to your business alongside making a permanent stain on your reputation.
Warshipping attacks companies from a completely new angle, which allows attackers to bypass nearly all perimeter defences. And with no ‘years proven’ method of mitigation known, the potential threat to businesses is significant.
How to prevent warshipping?
Warshipping bypasses nearly all common perimeter defences by physically intruding into the network. With no proven defences yet, the threat might seem insurmountable, but with some clever planning, it can be pre-emptively mitigated. Your focus should be on securing your wireless access points and effectively handling parcels. There are a few changes you can make now to work towards this:
Upgrade to secure Wi-Fi access points
Upgrading Wi-Fi access points to use Wi-Fi protected access (WPA) at a minimum or WPA2 (an upgraded version of the original standard) can make it difficult for criminals to intercept useful data from your company Wi-Fi due to the use of encrypted traffic.
Even WPA2 will not provide immunity to warshipping though since the standard contains flaws. What WPA2 will do though is require significantly more effort from an attacker – providing additional time to identify and destroy the device.
Prevent employees from delivering packages to the office
By creating a policy that prevents personal packages from being delivered to the office, any unexpected items will be immediately apparent. If preventing personal deliveries is impractical, scanning the contents of a package to identify hidden electronics can be used instead.
Monitor for rogue Wi-Fi devices
Constantly monitoring your company network for new and suspicious devices allows you to identify rogue access points. But technical defences alone are unlikely to remove this risk completely.
Educating employees about the dangers of connecting to lookalike Wi-Fi networks can go a long way in helping them understand what part they play in defending against warshipping.
Establish a quarantine zone for packages
In a company where it’s both infeasible to prevent employees from having packages delivered and to scan for metal or electronic devices in a package (i.e. where hardware is regularly delivered), another method of prevention is isolating the mailroom from the wider network.
Utilise multi-factor authentication
You should already be using multi-factor authentication since it’s a staple of security and something you’d need if you were to operate to a decent IT security framework such as ISO 27001.
Having a second factor means that even if the attacker manages to acquire the password to gain login details, without the second factor, they will still be locked out.
Where does the name ‘warshipping’ come from?
The name warshipping is nothing to do with warships. Instead, it’s derived from shipping (as in package shipping). The name draws from another attack known as wardriving where cyber-criminals will drive around an area, using a similar technique to break into insecure Wi-Fi networks.
What does warshipping tell us about the wider cyber-security landscape?
Warshipping shows us two things about the modern threat landscape. It shows that cyber-criminals are thinking outside the box when it comes to new channels of attack. And it shows a shift away from digital cyber-crime into real-world cyber-crime (a tremendously oxymoronic phrase by the way).
The idea of sending a package containing a hacking device to a company in order to break into the network sounds straight out of the plot of a heist movie. But the fact that we’re now dealing with this as a genuine threat shows the ingenuity of hackers.
If businesses are to keep pace with the new avenues of attack, they need to be dedicating resources to thinking about what the future holds for their cyber-security. If IT teams are already stretched thin, partnering with an IT security provider who will monitor and predict changes in the threat landscape is another option.
As for the shift towards real-world cyber-crime, it’s a trend that’s already been happening. Up to 99% of all cyber-attacks nowadays require human manipulation through social engineering rather than breaking into a network via pure computer skill.
While we’re currently in the era of spear-phishing (meaning spear-phishing is seeing the most widespread success, not necessarily that it’s the most common or newest), as employees become more sceptical of digital communications and wise up on attempts to trick them, criminals will have to transition to real-world approaches. Whether this will take the form of warshipping, USB drop attacks or even face-to-face social engineering, only time will tell.
Despite the constant stories of breaches and cyber-attacks, the tools do exist to counter almost every digital threat. In an environment that follows all security best practices (2FA, zero-trust, patch management, intrusion detection and prevention, e.t.c.) the risks can be controlled to a sensible standard. Most breaches are preventable if the business adheres to the security basics (such as what’s gained through obtaining the Cyber Essentials standard).
The reason we still see successful attacks (outside of companies’ inability to do their due diligence) is because attackers are exploiting humans. With attacks poised to move into the physical realm, not only will many of the digital defences become useless, but the human element will be more vulnerable than ever.