Email retention policies are all about decreasing the risk to your company. But for a truly successful policy, you need to strike the balance between a retention period which is too long and keeps useless mail around and one which is too short and loses mail that was important.
Your policy needs to take into account any applicable legal or industry regulations whilst not going overboard trying to store every email indefinitely. If your company does not yet have an email retention policy then it’s certainly worth drafting one, and here are five best tips to get you started.
How do I create an email retention policy?
1. Start with the regulatory minimums
Every business will be subject to different regulations, so the first thing you should do when creating your policy is to review the regulations your company is subject to and the relevant document retention requirements involved in each one. Some regulatory bodies you may need to consider include:
- The Data Retention Regulations 2009
- Freedom of Information Act
- Financial Services Act
- Sarbanes-Oxley Act (for US-related firms)
- The Data Protection Act 1998
If the retention period is unknown then six years is often the common safe denominator. This is because it’s possible to bring a “breach of contract” up to six years later. If your business is concerned about particular records then you should seek legal advice.
2. Segment your data by type of use
Once you have the regulatory minimums you will notice that the recommended periods vary widely. With this in mind, you may wish to segment emails by type, use or department to prevent having to store all content for the maximum retention period.
For specific documents like PAYE records, maternity pay or statutory pay it is up to employers to assess retention periods based on business needs. If an employment tribunal may require the document as evidence then a retention period of six years makes sense. If the document could be needed for HMRC reviews, then a minimum retention period of three years after the end of the tax year in which the payments were made would be necessary.
3. Draft a real policy
Creating a policy, and getting it approved by senior management and legal professionals, will give you the ability and authority to implement all the IT, security and process controls you need to enforces your email retention requirements. Your policy should include the following sections
- Purpose of the policy
- Retention time, including any segments you are using to define the retention periods. Durations are often listed as years or may be permanent
- Difference between paper and electronic documents – although ideally there should be none
- What constitutes destruction (e.g. shredding, deleting, overwriting, degaussing of media
You do not have to include specific technologies and processes, but it is a good idea to refer to capabilities and requirements (e.g. offsite archival). You should also omit areas you will not or can not support, such as the types of segmentation you are unable to determine or support. If you haven’t seen a full retention policy before there are plenty of examples online for you to reference.
4. Review the preferred solutions
Once you have the main points of your policy established, you can estimate your minimum requirements for a solution based on the number of users, the expected volume of email and the expected rate of growth. With this information, you may be able to loosely price out a solution, but you may also wish to obtain indicative quotes from suppliers. You should also prepare for any changes to the email retention policy which may affect your pricing e.g. the minimum retention period increases from 18 months to three years.
5. Involve legal in the policy process
If it is the IT department’s responsibility to draft the email retention policy, then it is important to involve legal. Whether that’s an internal legal team or an external law firm. The main reason for this is so they can review the viability of the policy and if it will meet your regulatory obligations.
Allowing legal to view the policy at this stage means you can present a unified front to the board. It also allows you to evaluate the options you have laid out, and remove any of the amendments legal have made that will drastically increase the price.
To conclude…
Given the number of different regulatory bodies and how they affect organisations, every business is likely to have an individual email retention policy. Following these best practice tips will help you to create a policy that is effective, sensible and which you can enforce.
Documents are a business asset. If an asset is lost, stolen or damaged, it becomes a risk. Both for the business and for their client.
This means having control systems in place to understand these risks is critical. And having the controls to counter them is equally as important.
It sounds simple. But after a decade of working with businesses, it’s clear that few of them have suitable controls in place. To address this, we’ve created 10 points to guide you through the process of creating your information classification policy.
1. Keeping it simple
When looking at security in any way, it’s important to keep it as simple as possible. This is particularly true when it’s something so regular as dealing with documents.
To make it simple, businesses need to invest in technology. In this case, there are three main technologies worth investing in:
- Document / Content management
- Data leak prevention
- Rights management solutions
A document getting into the wrong hands is going to cause your business, or a client’s business, damage. That is a fact. So aiming to implement all three is the best way to get a comprehensive solution.
2. Mapping your classifications
Before you get into classifying documents it’s important to ignore technology. Technology comes after you have decided the policies and processes you wish to follow.
What this means is that you need to map documents or types of documents into distinct groups. To do this, you should look at two key areas: the sensitivity of the document and their intended audience. This information will make up the foundation of your Information Classification Policy.
Many businesses already have classifications in place. But they’re often created, implemented and forgotten – quickly becoming unusable without weeks or months of additional work. You need to create an Information Classification Policy and not hide it away. It needs to be clear and easy for everyone to work with and conform to with little effort.
3. Building the Information Classification System
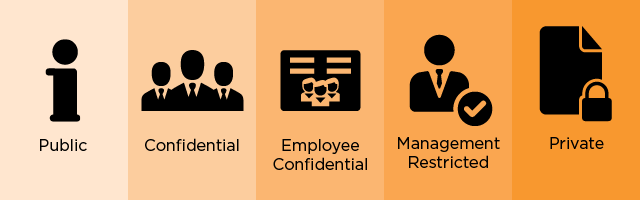
The foundation of any Information Classification Policy is categorising information. Here are a few example document classifications that will fit most business requirements:
- Public: Documents that are not sensitive and there is no issue with release to the general public i.e. on a website
- Confidential: Documents only to be viewed internally or with third parties that have signed a non-disclosure agreement
- Employee Confidential: Documents only to be viewed by employees at the company
- Management Restricted: Documents only to be viewed by the senior management at the company
- Private: Documents which contain personal information (useful for managing GDPR compliance)
In general, you don’t want to go over 10 classifications because classification should be as simple as possible. If you find that you have too many classifications, consider only looking at sensitivity or only looking at intended audience to begin with then filling in any gaps.
4. Assembling the Information Classification Team
A policy needs board-level support to ensure the business buys into and uses it. Once you have this, you should form a team which includes key departments in the business to enforce the policy.
This team may include people from technical, HR, legal and any other departments that are suitable for your industry. An appropriate team will be able to protect a business from security breaches whilst letting people access the information they need. And whilst it is important, the technical solution should be the last point to consider.
5. Designing the Information Classification Policy
Once you have your team assembled, you need to start going through your documents. In most organisations, it can be hard to know where to start.
To solve this, you should group documents at a high level. Looking at the impact that a data breach of that type could cause. Focus on the most sensitive document types first. And once that’s locked down, you can move through the less sensitive list.
When going through this process there are a few tips you can follow.
For company documents, it’s advisable to put your company name first. This helps them stand out from any other classification, i.e. from a client or a partner business.
It’s also useful to colour code classifications to help distinguish documents by eye. This helps you identify a sensitive document that’s left on a screen, printer or vacant desk. The beauty of colour classification is that it aids you in taking action internally or externally. It’s simple to prove that the defendant knew the information was restricted.
It’s important that you make it easy for staff to label and classify documents. If it takes more than three clicks to label a document, staff will find ways to circumvent the system. People naturally take the path of least resistance. So if your system is obtuse, employees will find ways to bypass it.
6. Enforcing control with automation
Once you’ve designed the Information Classification System, it’s finally time to look at the technology. Automation is very helpful to ensure enforcement. You shouldn’t rely on people alone as things will drop through the cracks.
It’s important that any technology links back into the core authentication system within a business. This will typically be Active Directory – the system you use to log in to your PC at the office.
Doing this simplifies things as you can use existing user groups to give access to certain classifications. There’s likely to already be an Active Directory group called “Board Members” for example, which you can use straight away.
Of course, grouping people doesn’t guarantee a user will know who they can and can’t send specific documents to. Nor will it prevent them from sending a document to a recipient by mistake.
This is why a business should be using a Rights Management system. Rights Management ensures that the systems know who has permission to access the document. So even if someone does send a restricted document, the recipient won’t be able to view it.
7. Educating employees
One of the largest reasons for data leakage is employees. Make sure to train them on how to use systems and refresh them periodically.
Also educate them on any security risks to the business – known, current or potential. They need to understand why following policies is important and how not following them can impact the business and therefore them.
8. Controlling leavers
So many organisations do not manage ex-employees. It’s important to disable their accounts once they leave the company. Even if they left on good terms, it’s best not to take a risk.
Loose accounts complicate the system at best and act as a open hole for attackers at worst. Hackers or insiders can hijack old accounts and make use of the access privileges. So you need to shut down accounts or strip them of all access rights to reduce the risk to your data.
9. Continually improving
It’s best if you adhere to common processes and document them somewhere accessible. To do this, you need robust information classification and risk policies that integrate with a wider standard. A good example to use as a framework is the ISO 27001 standard.
Doing this ensures that you assess and improve how you are controlling your risks within the business. Keeping you protected from an evolving threat landscape.
10. Widening the focus
It would be ridiculous to only focus on document security whilst ignoring the other risks to your business. So understanding all the risks your business faces and assigning suitable controls is something you must do.
Again, the ISO 27001 standard is a good framework to use for managing your information security on a wider basis. But this shouldn’t stop you going ahead and dealing with document security first. Getting this done will make things easier in the long term.
Summary
Businesses must control their risks, as failing to do so has catastrophic consequences. The key is to start simple and then improve. You don’t have to adopt everything at once.
A good starting point is to understand the sort of data you have and then classifying it. A good percentage of your business information could be used to extort or embarrass you. Or even worse, a client.
Once you’ve got your classifications, tie them into document templates. Then automate management and workflow automatically with technology. When done right, businesses can dramatically improve their security since it’s embedded onto the asset. Rights Management can then control who can edit, copy, paste, print, email, transfer or view it at a later date.
Once in place, this can be overlaid with network controls such as Data Leak Prevention. This watches documents flow in and out of the business and can isolate, sandbox or alert relevant people that a breach may occur.
To take it further, systems at the perimeter, such as gateway encryption solutions, can identify sensitive information. Encrypting it to ensure it won’t pass over the open Internet in clear text.
The list can go on but it’s important you start at the beginning by creating an Information Classification System. You need to understand what you have and what the risks and potential controls are first though.
Managed print and document solutions can bring a wealth of benefits, including increased employee productivity and efficiency, the ability to maximise billable hours, and greater document and data security. But in order to truly harness these benefits and enhance your operations, you need to choose the right print and document solutions partner.
Many companies will feel under pressure to simply pick the lowest cost option, or are blinded by a dazzling list of benefits which seem impressive on paper, but in reality, don’t quite deliver after installation. This why it’s critical to do your research, to ensure you’re choosing a solution that delivers a return on your investment, beyond simply the cost per print.
How to choose a solution that suits
The Installation Process
If planned and executed correctly, the impact of installation on day-to-day management and activity should be insignificant. If the print and document solution takes days to install and is difficult to integrate with your other applications, then it’s only going to have a negative impact. In the short-term, it’ll be costing your firm on the bottom line and will damage the end user’s perception of the solution. Inefficiencies will swallow up any potential returns in the long-run as users try to find a workaround for the solution.
How Does It Integrate?
If the platform will only integrate with a few pieces of third-party software then it’s going to be a struggle. Or it will become more of an expense in the long run. You want a solution that fits your needs and operations. Not one that you have to work around it, or which restricts future decisions. In order to truly integrate, you should be looking at firms who truly understand systems, and who can analyse your business and operations. You don’t want a provider who only looks at printer location and the cost per print. This is where so many traditional copier businesses fall down.
Flexibility
Your chosen print and document solution may integrate perfectly with your current infrastructure, but you don’t want it to affect software choices you make in the future. Otherwise, you could be left with an ineffective, cumbersome solution. Or have to pay out to start this whole costly process again. The right print and document solution should, as your IT infrastructure does, grow with you, allowing you to capitalise on new opportunities and changing markets.
Management & Long Term Planning
When most law firms receive a proposal from a print provider, the first things they will notice is a lower cost per click, due to standardisation, and a drop in paper consumption and waste. Whilst these are positives, there is only so much you can gain without further optimisation. You can achieve greater productivity and efficiency through scanning solutions, but this takes time, planning and ongoing management. Many print providers simply don’t have the knowledge to deliver this properly.
You need a provider who is in it for the long-haul, who will take the time to learn end-user trends and revisit the solution to see where they can change processes and automate staff functions. These are the areas which will make the solution completely bespoke and will enhance your margins. The provider needs to stage the solution, with every step optimised before progressing to the next. If a print company tries to deliver everything in one big project then something is probably not quite right.
Ask yourself, what do you want to achieve from this process? Do you just want to achieve quick wins? Or do you want to also optimise processes for ongoing operational and margin improvement? The answer to that question should give you an idea of what sort of providers you should be engaging with.
Remote access to internal IT systems is still a big enabler for any sized business. Business is no longer 9-5, and staff are no longer just sat in the office. The world has changed, so surely remote access has as well? Well, not as much as you’d think, but bandwidth has dramatically improved, as has its cost and ease of access. You can get a decent internet connection virtually anywhere in the world; this has made remote working productive and cost-effective.
What remote access technologies currently exist?
In reality, the technologies haven’t really changed much over the last 10 years. There’s a lot of hype surrounding numerous technologies, but at their root, they aren’t particularly new.
I’d say that we are generally seeing the decline of traditional client-VPN technologies (SSL and IPsec) to access files and folders, where you have an application loaded onto a PC/laptop/tablet and you connect to a corporate network. They are typically cumbersome and problematic to support. I would ass that this has changed a little with the rise of WAN accelerators and solutions such as Microsoft One Drive, but it still can be a little cumbersome to manage.
You will find that a large percentage of corporate applications have web-based front-ends these days. These are often more or less indistinguishable from applications installed on the desktop, feature-rich and simple to support. They typically lend themselves well to being published over the internet for roaming workers to access the internet. A typical example of this would be Microsoft’s Outlook Web Access.
A favourite technology for remote access and general working is thin client. There isn’t really much difference in the method of access to internal IT system cloud-based based ones.
Is it all about the cloud?
The cloud is generally remote computing, and thus remote working. However, corporations have been working to this model for decades, satellite offices accessing systems in remote headquarters on the other side of the world. Now because somebody put a shiny new cover on in, everything thinks cloud technology is all new. It’s not new, neither is cloud always the answer. If you have systems internally that you want to access remotely, it’s usually quite a straightforward exercise. That’s not to say that the cloud isn’t the answer to many business requirements, it’s just unlikely to be justified on remote working alone.
The risks of BYOD
We hear about BYOD (Bring Your Own Device) daily – accessing corporate systems with a user owned device. However, generally it will typically incur greater IT management, integration, administration and IT security costs – well it should do if implemented correctly (at this point in time) to remove any security risks: you aren’t going to accept significant risk within your business. If a business doesn’t own a device they can’t really control it. Then you can’t stop third parties from accessing the device, or from dangerous software being installed on it and circumventing corporate security, it’s as simple as that. Yes you can get encapsulation technologies that act like a secure operating environment on a device, but I’m still cautious. I’d still use these technologies, but with a corporate owned device.
I’m a bit more of a fan of CYOD or Choose Your Own Device. This is where an employee can select a device from a pre-authorised list, easing support overhead and ensuring productivity. Have you ever actually really tried to use an iPad productively? It just doesn’t compete with, say a laptop. However they are fine as additional devices for intermittent emailing and reading on the fly, etc. I also find that CYOD does help staff morale – it’s nice to have a choice, and computing devices bring up similar emotions to getting given a company car.
Also, I should note that it was only a few years ago that everyone was talking about increasing productivity within the workplace through IT. Can you really do that when everyone’s walking around with their own mobile devices hooked up to the internet with a 3G card? I understand there are always exceptions, but generally the money saving case will not stack up under scrutiny.