Since the UK announced a lockdown on Monday 23rd March 2020, more people have been working from home than ever before. According to the Office of National Statistics (ONS), in 2019 just 5% of the UK’s active workforce considering home their main place of work. Since the COVID-19 pandemic, however, an estimated 20 million people have relocated to a home office – an increase of more than 1000%.
It’s, of course, important to note that some industries, such as information and communication, professional services, and financial and insurance services, provide far greater remote working opportunities than others. Yet, even for employees in these industries, this is likely a new situation, with 70% of people saying they had zero experience of homeworking before social isolation measures.
There may have been some unusual conditions to manage during this time, such as childcare, home-schooling and enforced distancing from extended family, but it’s fair to say that remote working, overall, has been successful. Probably more successful than many businesses would have anticipated. Technology has allowed us to replicate the office environment; tools like Microsoft Teams, Slack and Zoom have made it easier to remain connected and productive; whilst the flexibility in working hours has allowed employees to tailor their day to when they work most productively and to deal with personal commitments.
Even though some parts of the world are beginning to slowly return to normal, remote working won’t be going anywhere. Plenty of businesses have now seen first-hand that they can still operate and that their teams can remain productive outside of a traditional office structure. Plus, employees will expect at least some level of flexibility now they have experienced the benefits and shown minimal impact on their role.
As the UK lockdown happened so quickly, many businesses weren’t fully prepared to roll out remote working on such a large scale. Therefore, if you want to continue to offer remote working and ensure that it delivers for your business, then you need to ensure you are set up and operating in optimal ways.
4 key areas to review for successful remote working
1. Embrace cloud technologies
Infrastructure
Mass remote working can put huge pressure on on-premise IT infrastructure. If the environment is unable to cope then employees may face a degraded IT experience, ranging from system slowdowns and insecure connections through to the risk of total failure, increasing frustration and hampering productivity.
Embracing cloud-based application and infrastructure resources can help ease this pressure, offering greater flexibility and scalability, with the capacity to cope with fluctuating demand. Employees can access their working environment from anywhere, at any time, on most devices – provided they have a stable internet connection.
However, choosing the right cloud computing model for your business processes is vital for long-term sustainability and profitability.
- Public – Offer massive scalability and cost-efficiency benefits. It’s ideal for any customer-facing applications such as eCommerce. However, there can be some security concerns as it uses a shared infrastructure.
- Private – Offers higher levels of security and direct control. It’s typically adopted by those in highly regulated industries or those who deal with highly sensitive information such as financial services, banking and medicine.
- Hybrid – Offers high levels of flexibility and is the default model for many businesses. It maintains some degree of control on-premise for sensitive data and applications but allows the massive scalability of the public cloud when required. Maintenance and complexity should be carefully considered to avoid security issues.
Cloud technologies are also making it easier than ever to remotely set up, secure and manage workspaces, no matter where users are based. Mobile Device Management (MDM) in Microsoft 365 helps you secure users’ mobile devices, with the option to create and manage device security policies, remotely wipe a device, roll out new applications and view detailed device reports.
Software
Making the switch to Software-as-Service (SaaS) applications – where applicable – is beneficial for remote working, offering several resource-related benefits.
The pay-as-you-go model offers enormous flexibility and scalability, making it easy to quickly increase capacity to match business requirements. Software upgrades, support and maintenance costs are typically factored in which not only ensures you are always on a supported version of the application, but direct vendor support is available without additional hidden costs.
Furthermore, subscribers can access the software easily from any location and supported device with an internet connection, negating any reliance on additional hardware and complex VPN connections. For example, applications included in Microsoft 365 can be accessed via a web browser, desktop app or mobile app (with iOS and Android options available).
Windows Virtual Desktop (WVD)
WVD is a comprehensive Microsoft Azure-based desktop and app virtualisation service, which allows businesses to create a virtual Windows 10 desktop environment and deliver remote apps to any device. This allows employees to access the same desktop environment remotely as they would in the office. It’s particularly beneficial for companies who have large groups of employees performing the same role and requiring access to the same environment.
2. Collaboration
With in-person meetings and daily huddles off the table, technology is vital for employee communication, fostering strong relationships and productive, efficient collaboration.
Microsoft Teams
Microsoft Teams reported massive growth in March 2020, with active daily users increasing 37% to 44 million, as employers encouraged their staff to work from home in line with lockdown measures. The cloud-based chat and collaboration platform aims to simplify and streamline communication between employees by offering a centralised place to connect and collaborate. Employees can send direct messages to individuals, set up hubs for group communication (ideal for departments), and organise video, audio or web conference all without leaving the platform.
Furthermore, it allows employees to collaborate in real-time by offering a centralised hub to access and share files. The core Office programs (Word, Excel, PowerPoint and OneNote) are all accessible in the platform, meaning files can be opened, edited and shared directly within Teams. Not only does this provide a better, more streamlined user experience, it also helps prevent things from getting lost or dropped – as often happens when documents are emailed back and forth for editing.
Microsoft is continuing to add more features to Teams, including background noise suppression in video calls, the ability to read and write messages without an internet connection, private chat channels, pop out chat and meeting windows, 3×3 video grids for meetings and more.
SharePoint
SharePoint is a web-based collaboration platform, which integrates tightly with Microsoft Office. As it is highly configurable, usage varies from organisation to organisation, but some of the most common use cases are:
Content and Document Management: Allows employees to store, archive, track, manage and report on documents and resources. They can easily access files wherever they’re working, ensuring they always have the most up-to-date version. SharePoint integrates tightly with numerous Microsoft 365 applications, such as Word and Excel, allowing multiple employees to share, access, edit and collaborate on files. Robust document versioning makes it easy to a history of changes and, if necessary, roll back to a previous edition. This feature is particularly valuable where you have groups collaborating on the same document. However, employees can also work independently by checking documents out. This is ideal where several edits need to be made and you need to prevent others from working on or reviewing the document until you’ve finished. Once the document is checked back in, others are free to access, edit and review.
Intranet and Social Network: A SharePoint intranet or intranet portal allows organisations to better engage employees by providing a centralised location to manage internal communication and information. You can share rich multimedia, personalised news and companywide, departmental or intra-departmental announcements. In some organisations, Yammer has superseded the social network functions of SharePoint as it offers many similar features with a familiar social media style layout. Alternatively, you can include a Yammer feed in a SharePoint site such as a highlight of the most recent conversations.
Collaboration: SharePoint contains features to support teamwork such as; project scheduling, shared mailboxes, social collaboration and document storage.
File Hosting: SharePoint Server hosts OneDrive for Business, which employees can use to store and synchronise personal documents, as well as publicly or privately share them with others when needed.
Custom Applications: SharePoint also contains an enterprise app store to further customise your platform.
There is also a two-way integration between Microsoft Teams and SharePoint. Every time a Team is created in Teams, a SharePoint modern team site is automatically created to support it. All documents uploaded to the Team are automatically stored in the SharePoint teams’ site.
3. Agile Working
Replace bulky desktops with laptops
The portability of laptops gives them the edge over desktops when it comes to remote working, allowing employees to easily change up their working location without needing to change device.
Fortunately for businesses, laptop costs have come down to match workstation costs when it comes to ‘the standard workhorse’. Many office-based workers will be used to working on multiple screens so may wish to replicate this setup at home, in which case you should also invest in a docking station that retains those critical USB/HDMI ports and wired connections associated with desktops.
The downside to working from laptops is bad ergonomics. Encourage your employees to build an optimal working space, with things like a supportive chair, using a riser so the laptop screen is at eye level, and angling the keyboard down. This is will help avoid things like back pain or muscle aches and strains.
4. Security
Cyber-security attacks and breaches are a risk that all businesses must face. They can be incredibly disruptive, with the potential to cause significant, lasting financial and reputational damage. Such an attack can be even more difficult to handle when employees are working remotely, therefore you need to ensure you have a secure set-up to reduce the risk as much as possible.
Security Training for Employees
Human error is one of the biggest threats to your security. It’s all too easy to respond to a phishing email, download malicious content or click on a dangerous link. Plus, with the security threat landscape in a rapid state of change, employees often aren’t fully aware of the risk their actions can pose. Ensure you provide regular training and updates to ensure your staff have as much knowledge as possible.
Endpoint Security
With remote workers, the physical assets (e.g. laptops, desktops, tablets) are not in the office so you must have the best security software installed and kept up to date. Ensure devices are protected with a robust anti-virus solution and are updated regularly. Patch management can help as it will automatically update all devices on the corporate network, including those not physically accessible. You should also consider updating your remote working policies to state that employees should not use their own devices to access companies files and data when remote working, as you don’t know what level of security software they have installed. Modern endpoint detection and response solutions (EDR) are designed to operate outside the corporate network, helping prevent malware, enabling rapid threat detection and allowing you to initiate immediate response actions.
Security Information and Event Management (SIEM) Solutions
With remote working increasing the risk profile, SIEM tools are a crucial part of the data security ecosystem: they aggregate security-related data from multiple systems, such as firewalls, server and PC event logs, antivirus applications, plus more. They analyse that data to catch abnormal behaviour or potential cyberattacks and then alert internal or outsourced security teams.
Typically a SIEM tool on its own is not enough and they are backed up by a Security Operations Centre (SOC) to ensure that security experts analyse any alerts generated by the systems. Generally, most mid-market businesses will outsource this capability so that their own internal IT teams just see the information that matters.
Multifactor Authentication (MFA)
Passwords are not enough to protect your devices and data. They’re often not as strong as people think and even if you follow best practice, they can still be breached. Once your password is leaked or on the dark web, then that’s it, your account is at risk of compromise – or multiple accounts if you reuse the same password. Multi-factor authentication involves an additional step to further protect your account. This may be a one-time code sent via email or text, an in-app push notification, a biometric method such as a facial scan or fingerprint, or a physical device like a USB.
Microsoft 365 subscriptions now automatically come with security defaults turned on, which means every user will have to set up MFA and install the authenticator application on their mobile device. Then the next time a user logs in, a code will be sent to their mobile phone via SMS or voice call.
There are also plenty of other 3rd party applications which support MFA using recognised security apps, such as DUO, Google Authenticator and Microsoft Authenticator.
Use a Virtual Private Network (VPN)
Using a VPN helps increase your online privacy by allowing you to have an encrypted connection over the internet, so is a good idea for those accessing business-critical systems or handling sensitive data. A business VPN will give employees the ability to remotely access private network resources, often necessary for completing work tasks. Accessing legacy systems can be difficult when using a VPN so an alternative may be to use SaaS instead.
Security Accreditations
A final thing, from a security standpoint, to consider is obtaining a security accreditation for your business. Preparing to undertake the accreditation process is a great opportunity for you to gain a clear picture of your current risk profile and identify and address gaps. There are a couple of options to consider:
- Cyber Essentials and Cyber Essentials Plus: Are great places to start if you want to ensure you have covered the basics and have a good foundation in place which you can build upon. It is a government-backed scheme, designed to help reduce the risk of cyber-attacks by implementing five basic controls. Cyber Essentials Plus is recommended for businesses with remote employees (e.g. home or client sites). It is also typically a minimum requirement if you wish to engage with government or MOD projects.
- ISO 27001: It is the best practice internationally recognised standard for an information security management system (ISMS). It helps businesses manage the security of assets, such as financial information, intellectual property, employee details or third-party information. Achieving this certification provides independent, expert verification that your company manages information security in line with international best practice.
Is there anything else you should consider?
It’s not only technical requirements you need to consider if you wish to roll out remote working as an option for all your employees. There are many cultural and social issues to consider as well, with isolation, loneliness and a lack of human connection all reported as common problems by remote workers. Whilst technology will go some way to help combat these, you need to ensure you have a well-rounded, strategic plan for long term remote workers.
In a modern business, communication and collaboration are becoming easier than ever. We can work remotely, we can access documents on our smartphones and check in with our colleagues whilst on the go.
While the increase in this type of working culture is positive. The rise of social media, instant messaging and email – along with the influx of portable devices and removable media into the office space means it’s easier than ever for data to leak out of your business.
Your data – be it financial, client, employees or intellectual property – is a valuable asset. So it’s only right that you protect it.
But with confidential data living on many devices (servers, databases, desktops, laptops, USB drives, mobiles), and moving through many channels, it’s difficult to know where to start. In this article we will outline some of the solutions available to help with the problem of data loss. And look at how you can begin your data leak prevention project.
What is data leak prevention (DLP)?
DLP is a strategy for making sure that sensitive information does not leave the corporate network. It describes any solution or process which identifies and tracks the journey of sensitive data. Or that enforces policies to prevent unauthorised or accidental disclosure.
Many businesses decide to undertake a DLP project to protect their IP or client data. But the task’s complexity and the resources required to complete and maintain it often results in the project never reaching completion.
But with the number of Internet-connected devices skyrocketing and remote or flexible working being so huge since the Covid-19 pandemic, managing and protecting your confidential information is vital. And you will only be able to do this with a DLP strategy in place.
How can a data leak occur?
There are three categories of data leakage:
- In Transit – Data is intercepted whilst travelling, e.g. via email, webchat, web traffic etc.
- At Rest – Data is captured from areas such as file shares, databases, desktops or laptops
- In Use – Data is captured from screenshots, clipboards, printers, USB drives and other removable storage.
As a business, you need to break down each category. Create a list of everywhere you store data and assign them to one of the three categories. Then classify the data in each location (e.g. level of sensitivity and risk) and write this down as well. Only when you understand what data you have and what risks you face, can you start to think about controls.
How can I keep my sensitive data secure?
1. Portable encryption
You should be encrypting any sensitive data which leaves your network. To do this, you need software systems in place since you cannot rely on employees alone. It only takes a lost USB stick, laptop or phone to deliver a severe blow to a business.
2. Endpoint protection
Data endpoints are the machines your employees use, e.g. desktops, laptops or mobiles. It’s on these devices that intellectual property and sensitive data resides or passes through.
Endpoint solutions allow administrators to control what devices are in use. They also let them see when they’ve been used, who by and the information which was accessed or downloaded.
Businesses should also have security policies in place governing the use of devices. Since employees store sensitive information like emails or documents on their smartphones and tablets. Your security policy must cover areas like password complexity, downloads and screen locks.
3. Email content control
As users often send confidential information and documents via email, it has a high potential for a data leak. Using content filtering allows deep content inspection technology to scan for potential threats. Email text, images and attachments can all be scanned this way to flag up potential leaks.
Content filtering can also alert administrators of insider threats. Informing them if users try to send restricted material outside the business.
4. Intelligent firewalls
Alongside email, IM and Internet use also present a risk to your data. Firewalls can protect individual computers and whole networks from security threats. But they can also take automatic action against potential data leaks, unauthorised access or malicious behaviour. This is achieved by notifying the administrator or by blocking the action.
5. Device control
It is now expected that employees will have a smartphone on them at work. For DLP, this means it’s much easier for employees to take away confidential data.
To limit this, you need to have security policies in place governing the use of devices. Your policy must cover things like password complexity, download and application guidelines, and screen timeouts. Without a policy like this, sensitive data will be at risk once it enters an employee’s device.
6. Assess security permissions
Many businesses give employees far more access than they need. Taking a Zero-Trust approach to access permissions helps address this. Zero trust means people only have access to what they will need on a day-to-day basis.
This approach allows you to limit the scale of leaks and prevents employees from accessing sensitive data. You should review your current security permissions and see who has access to what. Then create access policies that limit employees’ network privileges to only what they need for their job.
Your system should also issue alerts if employees act out of the ordinary. For instance, if they start accessing large numbers of documents. Or if a user tries to access restricted documents. These are often signs of a script running or a compromised account.
7. Control print
Multi-function printers (MFPs) are typically unmonitored and so have high data leak potential. Requiring users to sign in before use can reduce this, as they will only have access to certain functions. This also prevents leaving documents on the printer, since the document only prints once the user signs in.
8. Secure back-ups
Backing up important information is a fundamental part of business. But backups can be vulnerable too and are often troves of sensitive data.
As with the original files, your should encrypt your backups. It’s also important to ensure backup servers are not publicly visible such as through the Internet. This makes it harder for attackers to attempt to gain illicit access.
9. Image text analysis
It’s not only documents and text which you need to protect, images can be sensitive data as well. The prevalence of camera-enabled devices, like smartphones, in the workplace has made copying images simple. DLP solutions have the ability to analyse text within images, preventing data exposure.
10. Educate users
Businesses often assume their employees know what information is confidential and what can’t be shared. But data leaks aren’t always malicious and an employee may not even realise their behaviour is putting the company at risk.
It’s useful to educate your users on the dangers of data leakage. You should include it as part of your onboarding process at a minimum. And should carry out sessions on a regular basis to ensure everyone is aware of the dangers and up-to-date on company policy.
A good security policy will be well-defined and easy to understand. Without this, people won’t adopt it since accountability and employee’s roles will not be clear.
The GDPR and data protection
A further consideration is the EU General Data Protection Regulation (GDPR). Although the UK has voted to leave the EU, the new regulation may still apply to your company. So you should review your data protection policies and technology to ensure you are compliant.
The GDPR focuses more on what the data is about, not where the data lives. So even if you operate outside of the EU, the new regulations could still apply. GDPR rules that if your business offers services to the EU market or holds data about EU citizens. You will need to be compliant.
When it comes to data, your business should be proactive about its protection. Keep your security solutions up to date, and don’t be afraid to reach out to a consultant for advice.
The notion that a country’s military cyber-division has your business in their crosshairs for a cyber-attack feels ridiculous. Firstly, what could your business have possibly done to warrant such an attack and secondly, why would your business be a target?
Why do state-sponsored cyber-attacks target businesses?
A state-sponsored attack usually has one of three objectives: probing for and exploiting national infrastructure vulnerabilities, gathering intelligence or exploiting money from systems and people.
Directly attacking government or military systems to achieve any of these is hard. Comprehensive defences are in place and so the chance of success is low. But attacking businesses – where senior executives often baulk at the idea of spending money on the security basics – is far easier.
Businesses have become a favourite of state-sponsored attackers because they’re the least defended port into a country through which money or information can be extracted and disruption or unrest can be injected. Yet not all types of business are likely to be attacked.
What types of business should be concerned about state-sponsored attacks?
Let’s be real for a moment and acknowledge that most businesses don’t have to worry about state-sponsored cyber-attacks. Only if you fulfil one or more of the following criteria do state-sponsored cyber-attacks become a credible threat:
- You provide a service that would cause public disruption if it went offline (gas, electric, water, telecoms, Internet, medicine, transport, waste management or education etc.)
- You hold an active government contract
- You are a government or local council entity
- You are a highly profitable company
- You hold significant sensitive information (e.g. intellectual property or classified/secret information)
- You have a high financial sensitivity to IT downtime
- You have an office or operate in a potentially volatile region (Africa, Middle-East, Syria, Iran, Israel etc.)
Depending on which criteria you meet, the motives for an attack are different, but they generally fit into one of three categories: espionage, political or financial.
Espionage
Espionage is the most common motive and attacks of this type typically target companies who hold intellectual property or classified information and steal it to be used for blackmail, intelligence theft or counter-intelligence.
Political
Politically motivated attacks target companies whose service is important to public life and then hit their IT systems with a destructive attack to create unrest and disrupt the populace.
Financial
Financially motivated attacks target companies with a high likelihood of answering a ransom request such as those with a high sensitivity to downtime. The attack then uses ransomware or a distributed denial-of-service attack to disable their IT systems and pressure them to pay up to relieve the disruption. However, the ransom money isn’t the attacks’ goal because the real aim of such an attack is to manipulate stock prices or global markets to improve the attacking country’s position in the global ecosystem.
What threats do state-sponsored cyber-attacks pose to my business?
Existing threats
In the main, state-sponsored cyber-attackers use existing methods of attack but delivered from a military-scale operation. This means you’re now up against a cohesive team of well-educated computer engineers, using military-grade systems and an entire data centre or global bot network to deliver the attack.
There is an upside though and it’s that the principles of a strong cyber-defence still apply. If you’ve already made the effort to secure your operations, scaling up those defences and using more mature solutions provide a good deal of safety.
Unique threats
State-sponsored attackers also have several unique tricks up their sleeve which leverage their more advanced capabilities. Here are a few examples:
Surveillance
The most common type of attack is near undetectable man-in-the-middle intelligence-gathering operations. After infection, every email, file, and phone call is harvested, passed on to the attacker and analysed. GhostNet was a surveillance attack attributed to China (although they deny involvement) that infected high-value locations such as embassies in Germany, South Korea, India, Thailand, Pakistan, Iran and 97 other countries before being discovered.
Destruction
Infecting and overloading industrial systems to cause damage that will kill and injure employees whilst hurting economic output is another favourite tool of state-sponsored attackers. One such attack, attributed to Iran (although they deny it), occurred in 2018. Purpose-built malware was used to target a petrochemical plant with the intention to override safety controls, cause a build-up of pressure and trigger an explosion.
Crippling infrastructure
Other attacks are purely malicious. Russia is attributed (although they deny it) with the creation of the CyberSnake malware which provides attackers complete access to a network and the option to wipe all data from connected systems. The malware was used as a secondary channel of attack to cripple the Ukrainian power grid during Russia’s invasion into Ukraine in 2014. A number of countries also had strange power issues in 2019, although none were officially attributed to a cyber-attack.
Espionage
Finally, there are state-sponsored attacks that aren’t for the purposes of war, but for economic gain. In 2018, China allegedly conducted a multi-year cyber-espionage campaign that involved stealing intellectual property from several aviation engineering companies and using the stolen technology to design and build an entire aeroplane.
How can I protect my business against a state-sponsored cyber-attack?
Although state-sponsored attacks can be a genuine threat for certain businesses, there are several actionable steps you can take to increase your security.
1. Have the basics in place
Whilst the basics won’t protect you from state-sponsored attackers, they provide a fundamental level of cover, which is negligent to be without.
At a bare minimum, you need to be Cyber Essential certified – although if you wish to undertake government contracts, you’ll need the Plus certification. We have an entire article on how to achieve the security basics if you’re interested in learning more.
Alternatively, if you feel you have a secure environment but want validation, we also offer thorough security audits.
2. Integrate security into your culture
Whilst a check-list exercise like Cyber Essentials gets you started on security, to have any real chance against state-sponsored attackers, you need security integrated into the culture of your business. This can only be achieved by adopting and practising globally recognised security standards like ISO 27001 and adopting a continual improvement mindset.
A security culture is especially important if you plan on tendering for government work since standards such as ListX become easier to comply with if you’re already treating security sensibly.
Address things at the human level by simulating attacks and identifying which employees need extra training. Accountability of security with the board is also essential to ensure priorities are maintained.
3. Isolate critical IT systems/data stores
Separating your most important IT assets from the open Internet and general internal network multiplies the difficulty of stealing your intellectual property, taking down your IT systems or disrupting your operations by an order of magnitude.
But since most businesses are built around easy access to these resources, it’s not as easy as just cutting all connections to your critical IT assets. With some intricate networking and rights management configuration it is possible though and drastically improves your resilience.
If isolation isn’t a possibility at all, data loss prevention plus complete encryption for data both in transit and at rest should be made a priority instead. Our teams are well versed in this sort of project, so can help you undertake an effective implementation.
4. Clean up your technology supply chain
The banning of Huawei’s cellular networking products in critical infrastructure and government systems by the US and elsewhere may seem like paranoia, but it guarantees that if a backdoor does exist, you don’t have it.
If you’re in a government contract or planning to tender for one, you’ve probably already made steps to mitigate your use of risky hardware and software. However, if you’re still yet to map out what hardware or software you have in your infrastructure, undertaking an audit is imperative.
5. Engage in threat-sharing
Collaborating with the others in your industry to trade threat intelligence is an effective way to rapidly increase your resilience.
If the idea of sharing your security vulnerabilities and attacks you’ve had against your IT systems with your competitors sounds too risky, check if your IT support provider is already doing something similar.
A proactive support provider should already be taking lessons learnt from one client and applying them to all their other clients (for example, blocking a malicious IP for all clients after it was found targeting one). Having an IT support provider who specialises in your industry helps since it provides you with more relevant defensive updates.
6. Secure your communications
It’s imperative that you have at least one fully secure channel of communication (e.g. voice, data, text, video). Whilst apps like WhatsApp offer some security through end-to-end encryption, news stories such as the invasive WhatsApp exploit show that it’s far from business-grade software.
A secure communications solution is necessary for guaranteeing you have at least one channel of private communication – be it voice, video, text or email.
Securing your communications is especially important for companies with offices in volatile regions since state monitoring is more prevalent.
Conclusion
If you think you’re at risk of a state-sponsored attack, want to be secure enough to tender for government contracts or simply want to improve your defensive capabilities, we have experience in helping businesses in your situation.
What is warshipping?
Warshipping is a type of cyber-attack in which criminals use physical package shipping services to send malicious hardware to a victim or hide malicious hardware on the business premises. This hardware can be remotely controlled by the attackers and used as a staging post for further attacks.
How does the warshipping cyber-attack work?
Warshipping uses custom-built devices consisting of cheap, easily available components: a single board computer (£30), phone battery (£15) and IoT modem with 3G connectivity (£35). The resulting device, or ‘battle package’, can be smaller than the palm of your hand and, once configured, is easily concealed and shipped to a target.
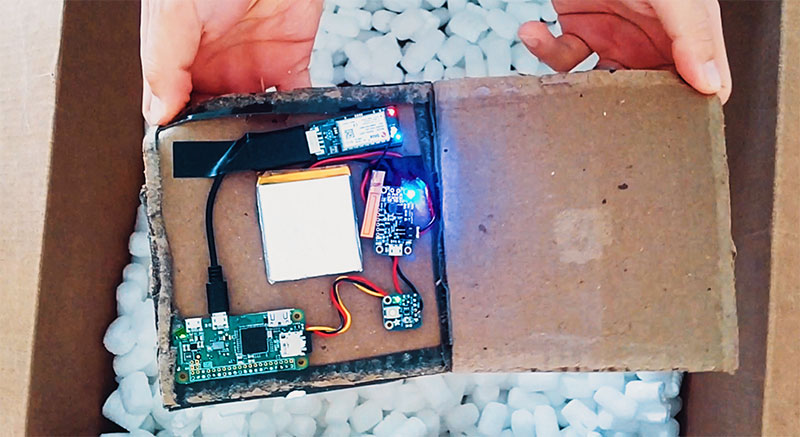
Whilst an attacker needs some technical knowledge to assemble the loose components into the battle package, it’s easy to imagine entrepreneurial criminals soon selling pre-built machines on underground forums. If this were to happen, the threat to businesses would dramatically increase as the attack becomes available to the masses.
Once a battle package is shipped, the modem regularly transmits GPS coordinates to the attacker’s command and control server. This allows the attacker to identify when the device has arrived and start full deployment. Of course, the device doesn’t have to come in the post – it could be planted into a toilet roof or hidden in a bush outside of reception.
Deployment involves one of two things:
- The device will imitate the existing Wi-Fi router, harvesting the login credentials of users who attempt to connect to the rogue access point.
- The device will intercept packets, looking for a handshake (the connection between a device and the Wi-Fi access point). The encoded handshake can then be sent back to the command and control server to be reverse-engineered and used to gain access to the network.
What threat does warshipping pose?
Once the attacker has access to the network, they can exploit vulnerabilities to gain deeper access. This allows for further attacks to be sent directly into the network – eventually creating a persistent backdoor for the attacker. From there, it’s possible for the attacker to gain full access to systems and information.
In business terms, a security breach like this is about as bad as it can get. Hackers would have complete control and access to your IT network and could do anything from deleting days of work with a wiper to a full-scale ransomware attack or even theft of intellectual property and client data. All of these cause massive financial damage to your business alongside making a permanent stain on your reputation.
Warshipping attacks companies from a completely new angle, which allows attackers to bypass nearly all perimeter defences. And with no ‘years proven’ method of mitigation known, the potential threat to businesses is significant.
How to prevent warshipping?
Warshipping bypasses nearly all common perimeter defences by physically intruding into the network. With no proven defences yet, the threat might seem insurmountable, but with some clever planning, it can be pre-emptively mitigated. Your focus should be on securing your wireless access points and effectively handling parcels. There are a few changes you can make now to work towards this:
Upgrade to secure Wi-Fi access points
Upgrading Wi-Fi access points to use Wi-Fi protected access (WPA) at a minimum or WPA2 (an upgraded version of the original standard) can make it difficult for criminals to intercept useful data from your company Wi-Fi due to the use of encrypted traffic.
Even WPA2 will not provide immunity to warshipping though since the standard contains flaws. What WPA2 will do though is require significantly more effort from an attacker – providing additional time to identify and destroy the device.
Prevent employees from delivering packages to the office
By creating a policy that prevents personal packages from being delivered to the office, any unexpected items will be immediately apparent. If preventing personal deliveries is impractical, scanning the contents of a package to identify hidden electronics can be used instead.
Monitor for rogue Wi-Fi devices
Constantly monitoring your company network for new and suspicious devices allows you to identify rogue access points. But technical defences alone are unlikely to remove this risk completely.
Educating employees about the dangers of connecting to lookalike Wi-Fi networks can go a long way in helping them understand what part they play in defending against warshipping.
Establish a quarantine zone for packages
In a company where it’s both infeasible to prevent employees from having packages delivered and to scan for metal or electronic devices in a package (i.e. where hardware is regularly delivered), another method of prevention is isolating the mailroom from the wider network.
Utilise multi-factor authentication
You should already be using multi-factor authentication since it’s a staple of security and something you’d need if you were to operate to a decent IT security framework such as ISO 27001.
Having a second factor means that even if the attacker manages to acquire the password to gain login details, without the second factor, they will still be locked out.
Where does the name ‘warshipping’ come from?
The name warshipping is nothing to do with warships. Instead, it’s derived from shipping (as in package shipping). The name draws from another attack known as wardriving where cyber-criminals will drive around an area, using a similar technique to break into insecure Wi-Fi networks.
What does warshipping tell us about the wider cyber-security landscape?
Warshipping shows us two things about the modern threat landscape. It shows that cyber-criminals are thinking outside the box when it comes to new channels of attack. And it shows a shift away from digital cyber-crime into real-world cyber-crime (a tremendously oxymoronic phrase by the way).
The idea of sending a package containing a hacking device to a company in order to break into the network sounds straight out of the plot of a heist movie. But the fact that we’re now dealing with this as a genuine threat shows the ingenuity of hackers.
If businesses are to keep pace with the new avenues of attack, they need to be dedicating resources to thinking about what the future holds for their cyber-security. If IT teams are already stretched thin, partnering with an IT security provider who will monitor and predict changes in the threat landscape is another option.
As for the shift towards real-world cyber-crime, it’s a trend that’s already been happening. Up to 99% of all cyber-attacks nowadays require human manipulation through social engineering rather than breaking into a network via pure computer skill.
While we’re currently in the era of spear-phishing (meaning spear-phishing is seeing the most widespread success, not necessarily that it’s the most common or newest), as employees become more sceptical of digital communications and wise up on attempts to trick them, criminals will have to transition to real-world approaches. Whether this will take the form of warshipping, USB drop attacks or even face-to-face social engineering, only time will tell.
Despite the constant stories of breaches and cyber-attacks, the tools do exist to counter almost every digital threat. In an environment that follows all security best practices (2FA, zero-trust, patch management, intrusion detection and prevention, e.t.c.) the risks can be controlled to a sensible standard. Most breaches are preventable if the business adheres to the security basics (such as what’s gained through obtaining the Cyber Essentials standard).
The reason we still see successful attacks (outside of companies’ inability to do their due diligence) is because attackers are exploiting humans. With attacks poised to move into the physical realm, not only will many of the digital defences become useless, but the human element will be more vulnerable than ever.
The story
At 27 minutes past 2 on a Monday afternoon, the phone on my desk rang. Picking it up I was greeted by Faye Langford (a name I was unfamiliar with) asking if she could speak to the company’s CEO, Robert Rutherford. She said she was calling from one of our suppliers (which has been left intentionally unnamed) about an earlier email regarding problems with a credit card.
As Rob was out of the office, I asked if there was anyone else who could help. I was informed that Rob was the only person on the account and so I told Faye that I would pass on the message. She wished me a good day and that was the end of our conversation.
I emailed Rob the details of the call and was content that the issue would be resolved now it was in the appropriate hands.
This all seemed quite ordinary but here are two things which change that:
- There are two people at this supplier who would normally call us regarding card information. Faye Langford is not one of them.
- There are over 15,000 employees who work at this supplier. Faye Langford is not one of them.
So, what had just happened?
The scam
What had happened was an attempt at voice phishing – also known as vishing. When you think of phishing, you probably think of emails but unfortunately, phishing can occur on any channel. Phone calls, SMS or social media are all platforms which scammers can use to fraudulently acquire your details.
But there are some things which make this attempt particularly alarming.
- They already knew Rob’s full name and that he was the company’s CEO
- They knew that we use this supplier and are familiar with the name
- They didn’t probe further when asked if there was anyone else at the company they regularly spoke to
While the information in point one is widely available – on LinkedIn and the company website – it serves as a reminder that scammers will use personal details to make their attacks more targeted and realistic. Had Faye asked to speak to “the CEO”, I would have delved much deeper into what the purpose of the call was. But since she was on first-name terms and was purportedly calling from a known supplier I was more inclined to trust her.
The second point is alarming because it’s narrowly accurate. Since the supplier is well known and works with many companies, this may have simply been a fluke. Alternatively, this may be an emerging worst-case scenario. It’s possible that the supplier has at some point suffered a data-breach and had client information leaked. This would explain how they knew we worked with that supplier and may have been the source of Rob’s details as well.
As it turns out, a few days preceding the call from Faye, the supplier had suffered a data breach. This breach included client’s names, job titles, and partial payment information including cardholder name and card type. This makes it hard to doubt the two events are unrelated.
The third and final point is the most alarming whilst also being seemingly insignificant. When Faye called, she wanted to speak with Rob and was clear that no one else could help when told he was unavailable. This indicates that the scam wasn’t just a scattergun approach but targeted at Rob specifically. Considering that cardholder name was part of the data leaked in the breach mentioned previously, this may be why.
How do vishing scams work?
Based on the articles covering the breach, the information given during the call and other attempts we’ve seen before, the scam would have likely gone like this:
The supplier’s data is breached and acquired by cyber-criminals. This may be sold on a dark-web marketplace to the scammer or the scammer might have been the one to directly take the data.
The scammer creates a fake email pretending to be from the supplier and sends it to the target company stating they need to resubmit card details due to ‘an issue’. This email may include a website link or telephone number to ‘update’ the card details – both of which will be fake.
(I should note that we never actually discovered an email. It’s possible that it was blocked by our email security system due to coming from a known malicious address or linking to a known malicious URL. Alternatively, the email may be entirely fabricated and only used to imply there’s ongoing communication and build trust in the call.)
The scammer now calls the organisation and requests to speak to the target regarding the email about card information. Once they reach the intended target they would likely say that there’s an issue with billing and until the card details are resubmitted, all orders will be frozen and no additional payments can be made.
If the target is worried by this and not suspicious of the request, they will likely be happy to hand over their card details to resolve the issue. The scammer would then check the details are real and maybe say something like “Excellent, I can see the payments are going through now.”, before hanging up.
How can you protect your business from vishing?
Undertake user training
You’ve probably heard this reiterated a hundred times before, but one thing often left unmentioned is that you must ensure your training program is grounded in the scope of the business.
The more abstract training is from employee’s day to day roles, the less engaged they will be and the less they’ll remember. A simulated vishing call against employees whilst in the workplace is not only realistic but will likely leave a lasting impression – making it incredibly valuable.
Don’t rely too heavily on caller ID
Caller ID allows you to put a name to a phone number and identify who’s calling. This sounds like a useful tool in preventing scammers masquerading as someone they’re not. But caller ID can be easily spoofed to show what the scammer wants to show.
There are many online services which offer caller ID spoofing – making it easy for scammers to take advantage of the trust a caller ID can give. This doesn’t mean caller ID is completely useless though as it can be helpful in filtering out nuisance calls, but you should not blindly trust the system.
Don’t respond to requests for details
It’s easy to say this, but if it were easy to do, vishing wouldn’t exist. To keep your details secure, you must get yourself and your employees into the mindset that unless the request is coming from an official channel which the caller can prove is genuine, don’t divulge company details.
Establishing and enforcing acceptable channels of communication for clients can make this much simpler. If you establish in company policy that certain details may never be communicated via certain channels (i.e. never disclose a mobile number over email), it’ll be far easier to stop scammers who are trying to siphon information out of the business.
Take the time to check
If there’s a suspicious call about an urgent bank transfer or new card details, get approval on whether it’s genuine off the phone and ideally face-to-face with who usually deals with the issue (e.g. the finance director). If the caller is genuine, they won’t mind you taking the time to check and if they aren’t, checking is a good way to avoid a disaster.
It’s worth building this approval process into policies so that people know who to go to for each request. Having the process in company policy also shows that asking about the authenticity of a suspicious request isn’t something for employees to be worried about doing.
Employ zero-trust
This policy sounds severe, but zero-trust simply means employees who don’t need to know something, aren’t told it. If you store credit card details in a secure digital wallet which everyone has access to, it only takes one successful vishing call for those details to be compromised.
If only the finance department has access to those details though, it’s much harder for a scammer to get lucky off an unaware employee who was trying to be helpful.
Establish and communicate a list of acceptable requesters
Like with establishing acceptable channels, you should ideally have a list of names for which it is acceptable to give details to. If you’re employing zero-trust, this list only needs to be known amongst those who have access to the details; otherwise, you’ll need to communicate it to the entire company.
… To summarise
Before this experience with vishing, I had only experienced it once before and it had been a rather poor attempt (a very robotic voice asking about the ‘accident’ I had been involved in). I had been fairly certain that this was the way vishing would stay – easy to spot, scattergun and done by text-to-speech. But this latest call has unfortunately proved me wrong.
Not only was it done by an actual real human, but it was pointed at a very specific individual. This is a trend which mirrors the evolution of other cyber-attacks and the increased weight cyber-criminals are placing on social engineering in their toolset. Whilst this threat is old and not uncommon in high-end security breaches, it seems it’s now also coming to the masses.
If you’re uncertain about whether phishing, vishing or any other type of cyber-crime is happening on the scope and scale it’s reported at, I hope this experience opens your eyes to the reality of what’s happening. It certainly did for me.
Lurking deep beneath your surface IT infrastructure is a malignant force. Its creeping tendrils extend into every department of the business and like a rot it spreads.
Whilst it started out innocent, as it grew more prevalent it’s evil nature emerged. Twisting roots buried deeper into the IT environment, corrupting business processes. Tendrils probed out, undermining defences whilst creating unseen vulnerabilities. And a maw guzzled and swallowed all the data it was fed.
But the worst part of all about this malevolent infestation is this. It wasn’t an attacker who planted this thing in your network, no. It was you.
And you continue to let it grow, feeding it and adding to it, all whilst unaware of the peril you have created…
Okay, whilst that description was a little dramatic, shadow IT poses an undeniable risk to your business. Gartner predicted that 1 in 3 security breaches will be the result of shadow IT applications by 2020. And Research from Cisco indicated CIOs underestimate the amount of shadow application running on the network by a factor of 14. That is to say, the CIO thought the business was running 51 cloud services when in reality it was using 730!
These stats highlight how many businesses still don’t have a grasp on the extent of their shadow IT. The risks and controls have been around for years, yet many businesses wait until they get burned to take action.
What is shadow IT?
Shadow IT is hardware or software (often cloud-based) used by staff without knowledge or approval from the IT team.
Shadow IT can present itself in many ways, a few examples being:
- Staff sharing files between themselves, suppliers and customers. Often with a cloud file store such as OneDrive, Dropbox or Google Drive.
- A member of the sales team using an online CRM solution to work on a campaign.
- An account manager using a personal Skype account to conference with clients.
- An employee using an online tool from their previous job, instead of the software their current employer uses.
In each example, it’s obvious that these systems will be outside of the control of the IT department. This is a concern because it increases the business’ attack surface and adds many fun and exciting ways in which your sensitive data could leak.
Shadow IT plays on the idea of “if you can’t see it, you can’t control it”. As a result, it creates a lot of invisible risks and security gaps which the IT team is unable to address.
Of course, shadow IT may be bringing in benefits to a business. If an employee is more comfortable with their tools, they’ll work more effectively. But allowing it to run wild introduces gaping security holes and puts you at higher risk.
Why does shadow IT occur?
Shadow IT arose with the boom in cloud-based technologies and applications. This application explosion allowed employees to gain access to IT solutions through a web interface. And with so much variety, employees could buy an entire suite of tools with little no involvement from the IT department.
The popularity of having sudden access to a plethora of applications was compounded by the fact that in the past, IT projects would have to stop or grind their way through the IT department before becoming usable. Whilst this wasn’t done with malice, the delay it caused frustrated power users who wanted rapid solutions to their issues.
In short, the demand for change was louder and faster than the IT team’s resources, and even their awareness. Technology had come to the masses and they wanted to use that technology. Now.
But blaming everything on the IT department isn’t fair and nor is it accurate. Another fundamental cause of shadow IT is misalignment within the business. Something which involves many departments and generally the board.
A lack of control on the IT estate tends to make identifying a single reason for shadow IT impossible. This means the cause for shadow IT can vary from business to business.
How can I manage shadow IT?
Whilst the idea of prohibiting the use of any applications outside of an acceptable list seems like it would work fantastically, it doesn’t.
Not only will it annoy employees and disrupt their workflows, but people will likely find a way around the filtering or will pester the IT team to add certain applications to the whitelist. Circumventing the point of the system in the first place and only resulting in a net negative.
Instead, the business needs to address the root cause of its shadow IT by installing policy controls and technical controls to reign it in. Here are 7 simple steps to give you an idea of where to start.
1. Review what’s going on
The first step is to use your internal monitoring and control solutions to analyse who is going where and doing what. It’s also worth auditing laptops and desktops if you allow users to install applications on their own devices (not advisable!).
2. Evaluate and prioritise risk
Go through your reports and work out which shadow IT elements pose the greatest risk. Staff sharing sensitive information or accessing the dark web through .tor browsers should both be big red flags.
Whilst doing this, you may also find out you are breaking regulatory obligations without evening knowing it. For instance, by storing files in regions that are unacceptable.
3. Lockdown
Shut down anything that is dangerous or breaking regulation immediately. If it’s illegal or breaks company policy then block it and take appropriate action at a management or HR level.
4. Give an amnesty
Once you’ve dealt with the immediate dangers and know what’s going on give everyone the chance to stop using the unapproved shadow IT applications.
Give them a week or two to alert you why certain applications are necessary and you can then manage the exceptions. After the week is up shut everything unapproved down.
5. Manage relationships
As you work through this process, take care to manage the external perception of the board and IT. People often use shadow IT to better fulfil their roles. So you should be trying to understand why they are using it and how you can fulfil their needs.
You may even find that some shadow applications are of benefit elsewhere in the business and adopting them could be a net positive. You don’t want to turn the business against the IT team as everyone then suffers.
6. Create policies
It’s unlikely that regular employees are aware of the danger of shadow IT and why they shouldn’t use it. Clear policies with training and regular reminders should help minimise risks.
7. Continually manage
You should always be monitoring and evaluating what’s going on in your network. People forget what they’re told, and the odd employee does go rogue. The technologies are out there and are nothing new. So there’s no excuse for not monitoring and blocking employees from doing things that could harm your business.
On the ‘business’ side you have the long term business strategy and plans or business requirements. On the other side lies the IT function.
This visible gap is where misalignment begins, but it’s often compounded by the negative preconceptions each side holds of the other.
| What business executives think of the IT department | What IT departments think of business executives |
| The IT department takes a long time to get anything done | The business constantly changes its mind about what they want/need |
| The IT department takes up too much budget and doesn’t deliver results | The business chooses non-optimal IT solutions without our input |
| IT is a ‘necessary evil’ | The business doesn’t understand the purpose of IT |
| The IT department doesn’t understand our needs | The business dictates to us without giving us any say |
Why does disconnect matter?
IT is an essential component of every business operation today. It is critical to the success of the business and so a lack of alignment between business and IT strategies can deal a heavy blow to the bottom line.
All too often, IT strategy is an afterthought – something bolted onto the wider business plan. This can result in overly complex infrastructures or systems that are difficult to change – making it a struggle to maintain and enhance business operations later on.
However, and perhaps more critically, misalignment can leave the business vulnerable.
The way IT interconnects with almost every business operation naturally results in an increased risk profile. Previously when talking about IT, we simply meant hardware and networks – things for providing a means to process, backup and safely store data. Now our expectations are much greater. We demand more information, more complex analytical reporting, greater integration, and increased data storage capabilities. Then on top of that, we demand that everything is kept easily accessible and highly secure.
What problems does disconnect cause?
The evolving dependence of the business on IT means IT events – data loss, corruption, security breaches and infrastructure failures – can no longer be confined to the department in which they occurred. When one of these IT events occurs now, the whole organisation’s productivity, reputation and ability to achieve strategic goals are hampered.
Yet despite this, many business leaders still aren’t considering aligning IT risk management with strategic business initiatives. Instead, they choose to rely on a traditional approach combining a cost-based analysis of ‘what may go wrong’ with metrics based on historic KPIs.
Such an approach can be unreliable as it’s too narrow to effectively identify and manage risk. Risks that fall outside the conventional realm – like fires, floods and power failures – can be easily overlooked. Furthermore, it fails to demonstrate how risks can affect the likelihood of achieving strategic objectives because it does not establish links between them. This contravenes ISO 31000 which emphasises risk management as a strategic function to enable businesses to make risk-adjusted decisions, rather than a compliance-orientated one.
Now, this isn’t to say that the act of quantifying and qualifying factors is not useful, as it most certainly is. Instead, the key takeaway is that to effectively identify the risk of IT, the use of a broader view is required. One which goes beyond traditional standards and aligns IT use with the strategic aims of the business.
How can I counter disconnect?
Instead of only looking at the financial impact of physical and natural threats to IT service delivery, you must broaden the spectrum and consider the impact or contribution each one will have to the achievement of strategic goals.
The positives of this approach are numerous. Firstly, by aligning risk techniques to strategic business initiatives, organisations can better document key performance indicators (KPIs) and key risk indicators (KRIs). These metrics are vital to continually monitor risk, providing an early warning system for a potential risk before it occurs.
Secondly, with a greater understanding of the business’ tolerance to risk, it is easier to implement a more realistic and balanced strategy and distribute clear communication plans. This helps protect your brand and shield against potential reputational/financial damage which can arise from IT events – for example, a poorly planned cloud migration resulting in significant disruption to customers.
This approach also delivers a significant competitive advantage by helping businesses to make calculated responses to risk that others in their industry may lack the insight to make. However, this does rely on KRIs being implemented and used properly. These indicators must provide an alert of emerging risk in good time, so the business has time to react and make appropriate decisions. Thereby reducing the potential negative impact on achieving strategic goals.
Another task you will need to undertake is addressing the original cause of disconnect on an employee level by cutting out the stereotypes executives and the IT department have of one another. Ensuring that each group sees value in each other is often a task that falls onto the shoulders of the CIO who acts as a bridge between the IT and business aspects of your organisation. But the responsibility also lies with every individual to ensure that they are working towards a common goal in the business.
IT risk will always exist in some form, but by improving alignment this can be continually monitored and communicated meaningfully to stakeholders. A proactive risk approach will enable the business to operate more cost-effectively, become more agile and respond to change with more informed, measured decisions.
Patches are the name for software changes which are designed to update, fix or improve that software’s functionality. Patches are deployed for various reasons including fixing security vulnerabilities and bugs, improving the user experience or increasing performance.
What is patch management?
Patch management is an automatic update process for every node on the corporate network. This includes endpoints in physically inaccessible locations such as remote laptops and mobile devices.
Deploying patch management means that staff will not need to manually check for and deploy software patches, which will typically be an exhaustive, time-consuming task – except for the very smallest of businesses.
How does patch management work?
There are different methods of patch deployment and they vary depending on the infrastructure design for each company information system.
Most companies with large infrastructures implement automated patch management systems which reduce the manpower requirements of manual implementation. Other companies will outsource this function to a trusted third party. Often, if your IT support is fully outsourced, patch management will be included as part of this service.
An automated patch management system requires the installation of a client agent. This enables network administrators to manage patch distribution from a centralised interface. They can configure the settings for patch distribution, generate reports on the status of patches and set distribution at different levels to cover different applications and devices.
Why is patch management important?
New vulnerabilities are discovered every day and unpatched systems are one of the easier attack vectors for cyber-criminals to take advantage of. Companies continually release new patches as vulnerabilities are uncovered by researchers and hackers and if your business does not apply these updates then cyber-criminals have an easy entry point into your network.
Furthermore, patch management also ensures that your enterprise technology continues to function as it should. Software bugs, even minor ones, can cause headaches and impact employee productivity so automatic patching ensures that these problems can be resolved as soon as possible.
What are the benefits of patch management?
Patch management ensures that all pieces of software – even those which are rarely used – remain up to date, ensuring that they don’t introduce major security holes within your business.
Automatically deploying updates also frees up a vast amount of time, allowing staff to focus on more productive areas of the business. Rather than checking through update lists, they can work on getting the most business benefit from the IT systems or looking into ways to further modernise the systems through digital transformation. Furthermore, if you have staff working remotely or from mobile devices, patch management ensures that these devices remain up to date regardless of location.
What are the consequences of not deploying patch management?
An average of 50 new major vulnerabilities are discovered each day, the majority of which are addressed in patches. While patch management is not a cast-iron guarantee against every potential vulnerability out there (or which may arise in the future), it is a preventative measure to protect the integrity and security of your network infrastructure and information systems.
However, it’s clear that many are still not implementing security patches. This can be seen by the fact that one of the most popular vulnerabilities to exploit is a remote code execution in the Windows common controls, known as CVE-2010-2568. An exploit which was patched in 2012.
If a vulnerability does arise, having a solid patch management system in place means that the network is being constantly monitored. This especially important when it comes to preventing a “Zero-Day Attack”, which is an exploit which can occur while a patch is in the process of being produced to repair it.
How can you ensure your patch management is effective?
While automatic updates are beneficial, the best patch management strategy is one which balances automatic and manual updates.
Automatic updates are not a cure-all and can sometimes cause problems without proper vetting. Microsoft, in particular, has a track record of having to roll out patches to fix the bugs introduced in their patches.
The most effective way to manage patches will vary between each organisation, but there are a few key factors which apply to all:
- Critical security fixes should be applied as soon as possible.
- For all other patches, consider how often the software is used and how business-critical it is to decide how urgent the patching is.
- Where possible, ensure that patches are installed outside of working hours to minimise disruption to business workflows.
The key concern for most businesses is the number of patches and the manpower required to deal with them, however, with patch management and new technologies, patches can be managed much more effectively.
You may dread hearing “infrastructure refresh” or “systems update”, but if you want to remain competitive then you need to invest in your IT systems.
As your business grows, your needs and priorities will change. An increased headcount, technical advancements or market pressures could put pressure on systems that may have been perfect when starting out, but are now starting to restrict the business and hamper operations, agility and growth.
If you aren’t running a rolling IT upgrade program within the business then you will be building up technical debt that will often cost you more in the long run. You may think it’s okay to sweat an asset for another year, but often it brings with it a number of issues:
- Increases the risk profile as aged systems are more prone to failure.
- You miss out on technological advances that deliver greater value and returns versus the legacy asset.
- Greater disruption when a delayed change happens versus a steady and rolling investment and upgrade cycle.
If you’re holding back on investing in your IT systems, then you could be missing out on increased efficiency, productivity and often a competitive advantage. In today’s blog, we’ll show you the benefits you will achieve if you regularly invest in your IT systems.
What are the benefits of investing in your IT systems?
1. Competitive advantage
IT is now the beating heart of most businesses, both in terms of driving internal efficiencies and enhancing productivity, right through to improving customer and supplier engagements on the front-end of the business.
The pace of change is so significant that gains are always there for the taking. Of course, that doesn’t mean to say you upgrade every year. But too many businesses are sat on dated systems that are holding back business growth. It’s clear to see and proven in most sectors that those at the top are those who invest wisely in IT. Not those who sweat their IT assets, specifically in terms of their business systems, i.e. ERP, CRM, case management systems and the like.
It’s also important to note that technology and systems is a key differentiator and certainly an area which potential customers look at when choosing between companies. It could be as simple as one business has a better web portal than another.
2. Business agility
The ability to respond to changing business needs in an ever-complex world is key to success, and technology plays a key role in this. It goes hand in hand with collaboration, which leads to streamlined processes and more efficient projects. From unified communications through to CRM systems, technology must be a key part of your strategy, if you want an agile business. Other areas to consider are IT platforms built around mobility, cloud, big data, artificial intelligence, block-chain and social networking which can play a transformational role in a growing business.
3. Employee morale
The level of technology within a business certainly affects morale. It’s crude, yet true that staff include the IT environment when evaluating their position within a business. The IT environment is where the majority of office-based workers spend their days. If the equipment or systems are dated then when comparing their role to their peers. it does play a factor, in terms of morale. It’s as simple as one employee in one business drives a new company car whilst another sits in a 5-year-old, high mileage one. It matters to people.
4. Greater efficiency and productivity
New technology, where there is a clear business case along with the right technology, delivers efficiency and productivity. It’s what IT and computing, in general, was created to do – automate and improve manual processes and operations. Businesses should regularly measure where they are and what a new system could deliver compared to sitting still. You don’t always have to change – but first you should understand if there is an advantage to be gained.
5. Security
You wouldn’t leave your office unlocked, so why would you leave your IT environment open to security violations? It’s important that you regularly undertake a risk analysis to identify new issues and continually invest to mitigate them. The security landscape is changing rapidly now, the threat landscape from one quarter to the next can be dramatically different.
It could be as simple as the need for multi-factor authentication. Passwords alone are really not secure enough, but requiring staff to use a key fob when logging in or accessing certain areas is an easy way to add an extra layer of security. Depending on your business, you may also need to look at secure communications to protect your voice, video, email and text conversations. The rise of GDPR obviously brings in other areas to address, particularly around encryption and control. Failure to invest can cost a business on many fronts.
Conclusion
If you actively invest in your IT systems, it will help increase productivity, enhance data security and expand storage capacity. All of these elements will naturally contribute to higher revenue and profits as your business becomes more efficient and streamlined.
However, remember the key is making the right investments. Technology trends come and go, so do seek out the advice of an experienced technology consultant when considering an investment.
Whilst most would assume the majority of cyber security breaches are the result of external weaknesses, your weakest security link is actually inside your business, sitting at your desk right now.
All too often cyber criminals are able to gain access to companies’ systems due to employee negligence, error or ignorance. According to a survey by Experian, more than half of organisations attribute a breach or security incident to a malicious of a negligent employee.
Protecting your company begins with employee education and training. If users are not aware of the risks out there and how their actions could potentially impact the business then the danger will continue to exist. Although businesses should already have security solutions in place, there are a few simple tips employees should follow which will help bolster that protection.
1. Always update apps and software
Although updates can be annoying they are necessary to maintain the maximum protection against potential threats. It is good practice to turn on automatic updates for all devices you work across (including any personal ones) if you haven’t done so already.
2. Avoid unsecured Wi-Fi networks
With office hours no longer strictly 9am-5pm, many employees now work remotely or on the go. Whether you’re working in a café, hotel or anywhere else outside the office you should always try to avoid connecting to unsecured public Wi-Fi hotspots, where it’s relatively easy for others to capture sensitive information such as emails, passwords and unencrypted instant messages. In the instance where there is no other option but to connect to a less secure network, it is recommended that you use a good quality virtual private network (VPN) when connecting to your business. Even if a hacker were to position themselves in between you and the Wi-Fi hotspot that data would be strongly encrypted.
3. Don’t reuse personal passwords for work
Thanks to the advice which stated that passwords should contain uppercase, lowercase, characters and numbers, many of us are suffering from password fatigue. It can be difficult enough to remember one complex password, let alone a whole string of them for the various applications we use inside and outside of work, so many people have resulted to using the same password across multiple accounts or just changing one minor detail, e.g. Password123! to Password234! Once one account is compromised, every account that uses the same password will be at risk.
This was demonstrated by the Dropbox breach back in 2012, which was the result of a stolen employee password. The employee used the same password for LinkedIn and to access Dropbox’s corporate network. After the LinkedIn data breach hackers were then able to use the password to access Dropbox’s corporate network and steal more than 60 million user credentials.
One stolen password has the potential to cause widespread damage, so it is really important to use a different one for each account. Luckily, the advice regarding passwords has now changed. Now it’s recommended to use a string of words to create a memorable passphrase, such as “footballapplegolf”. Not only is this more memorable but it is also much harder for a computer to crack. If remembering multiple passphrases is an issue then it may be worth looking into a password manager.
4. Know how to spot a phishing scam
Emails are one of the most popular attack methods and it only takes one click for a virus to infect your systems. You should always be cautious when it comes to emails. Never reply to, follow links or open attachments from any unexpected or suspicious emails, even if the sender looks familiar.
When in doubt you should check the source first (one easy way is to check the full email address next to the sender’s name) and make sure the request is genuine. If you receive an urgent email, supposedly from the Finance Manager, requesting a bank transfer verify the request in person or by phone. Hackers now take the time to craft a message which seems genuine, so it is always best to exercise caution.