Endpoint security has evolved significantly over the last 2 years.
The old signature-based antivirus and basic firewalls are simply not enough to protect businesses from an endpoint breach, be it a laptop, desktop or a mobile device. The threat landscape has increased massively through COVID, endpoints are outside of the protection of the corporate network en masse. How the endpoint is protected is going to vary by the workload and application sets used within an organisation.
Endpoint Security for SaaS platforms and legacy applications
There are two main camps. Those who are predominately web based, say using Office365 and a couple of line of business applications that run on a SaaS (Software as a Service) platform. And those who run a mix of legacy applications, probably with Office 365 and perhaps Citrix or Windows remote desktop. There are of course those who use technologies, such as AVD (Azure Virtual Desktop) but for simplicity we’ll bundle them into the latter camp. In reality, the risks to both are similar and need to be assessed.
Layering is key
The key to protecting all endpoints and ultimately all organisations is to have numerous layers of defence. You can’t simply rely on a single control – because if that fails, or has a security vulnerability, then it’s probably going to be breached. The cybercrime industry is simply enormous, global, relentless and moves at lightning speed.
The more controls and the more checks and balances you have, the more chance you have of another control picking up and stopping exploits. This isn’t about doubling up, it’s about using a number of controls that protect against primary risks but may have some overlap. It’s not just about technology, so organisations really need to work on their risk registers to understand how they are controlling against certain risks and where they are thin.
Information Security Management System
Ideally organisations should be looking at implementing some form of ISMS (Information Security Management System). Something such as ISO27001 or IASME to continually evaluate, test and improve their IT security.
It’s now critical to have a framework to manage endpoint security as things are moving so fast. A business can’t simply rely on IT support and security teams to be responsible for data security. It’s the boards responsibility to make the decisions on how they are going to protect against particular risks, divert budgets, etc. It’s not the IT team that regulatory bodies, such as the ICO, FCA or SRA will punish if there is a breach. Neither will clients or the media be fobbed off that it’s an IT issue, especially if there is no ISMS in place.
Simplify IT environments
As a general rule, all organisations need to be focused on simplifying their IT environments. Over the years there has been too much bloat, in terms of too many applications, servers and data. This bloat has led to complexities.
The more complex an IT environment the more difficult it is to secure. This has to be a primary focus in this new world, simplifying the environment. Needs dependant, generally you can simplify and ultimately secure the endpoint by not having any data or applications running on it, except the bare minimum. The larger the attack surface the bigger the danger of an exploit.
This isn’t always going to be possible of course, but where it is, technologies such as Azure Virtual Desktop, Remote Desktop Services and the like do have their place.
Endpoint Security of BYOD (Bring Your Own Device)
More and more organisations are again talking about BYOD (Bring Your Own Device) coming out of the pandemic. In certain instances/circumstances BYOD can be extremely beneficial for a business if, for example, it’s giving access to a web based portal to a 3rd party contractor, obviously with some security measures, such as multi-factor authentication. However, as a general business practice, for all staff, BYOD not a good idea because in the main it’s difficult for an IT team to really lock down someone’s own device properly.
There are various container type solutions that isolate data and applications from the underlying operating system that can be used, but depending on what information that employee is dealing with you might want greater control and monitoring of the device. You can’t really do that on an employee’s personal device without impinging on their privacy.
Can CYOD help solve Endpoint Security issues?
One good solution can be a CYOD (Choose your own Device) initiative as a sensible middle-ground. That way people get the tech they prefer but the business can overlay whatever security solutions they like. In particular SIEM solutions and intelligent advanced endpoint security protections solutions are more and more critical.
What risks does an endpoint face?
The bulk of the risks that face the endpoint come over the network, as a direct attack against an interface, listening and man-in-the-middle attacks or delivered through an application, such as a web browser or email client. Once the endpoint is breached any follow-on breach to the main corporate network is going to also come from this device.
This is why it’s essential to get some control of the connections to and from the endpoint with technologies, such as SASE, CASB and VPNs. It should be noted that generally traditional VPNs are cumbersome and still problematic, and not ideal in a hybrid world.
Next Steps
If you’d like a free initial review of your security controls – without any obligation please fill in your details here and one of our team will get back to you.
Our Head of Security, and CISO Service lead, David is recognised as one of the Top 10 influencers by Thompson Reuters, and a Top 50 global expert by Kingston Technology. He is also one of the Top 30 most influential thought-leaders and thinkers on social media in risk management, compliance, and regtech in the UK.
In his role as Head of Security at QuoStar, David leads the CISO Service. The CISO service provides businesses with the cyber-security skills and experience necessary to manage the multitude of threats and rapidly changing risk landscape of today, on a flexible and cost-efficient basis. David take’s a moment to share his views on it all.
1.How did you get started in the security field and ultimately become a CISO?
David: I was around when some of the first Viruses went mainstream. Back then I worked for one of the only companies that made Multi Factor Authentication systems in the 90’s. It was “leading edge” at the time.
I built and ran one of the largest commercial remote access platforms using Multi Factor Authentication. Then I ran Infosec for some FTSE 100 companies, one of which was the largest private trading network in the world – trading 3.5 trillion dollars a day. Another was managing Global Security Services Operations Centres (24/7) across 4 continents, where most of the customers were FTSE 250.
2. What do you enjoy most about working as a CISO Service resource/consultant?
David: Meeting challenges of audit, due diligence, and breach management.
Audit is getting more involved and complex and due diligence is often 300-400 questions and an “interview” with the compliance department of potential customers.
Breaches is about managing with around 10% knowledge of the situation and making decisions in a very short time for the best outcomes – while ensuring buy in from the board. They always seem to happen on Friday evening!
3. As Head of Security, what challenges or issues do you regularly see in small and mid-market businesses? Why do you think the same issues keep occurring?
David: 1. Robust management of access and privilege management. 2. Managing risk consistently. 3. Not aligning Cyber Security with Data protection requirements – as they overlap at a core level.
If you have control of the information assets servers and cloud, information security is much easier to manage. It enables savings in resource and effort if this happens and can demonstrate to the business control and improvement.
4. How do you think the security landscape has changed in the last five to ten years?
David: As a CISO Service lead, I believe it is manging the hybrid of internal servers and cloud – and managing the challenge of access control. The company boundary is very fluid, especially where ‘what’s company and what’s personal’ is concerned.
One of the best frameworks is ISO27001. It is good for demonstrating accountability and decision making. It also aligns with SOC2 and parts of HIPAA quite well.
5. What do you think will be the emerging risks businesses need to consider in the next 1-2 years?
David: It used to be technology first, then followed by making technology safe and compliant. Now technology needs to be safe and compliant first, and performance orientated second – along the lines of what has happened in the automotive, aerospace, building and food industries.
The risks potentially surround the technology itself not having enough security management capability, or that if it does it can be resource intensive. There’s also the globalisation of threat actors and the capability of managing multiple global data protection regulations.
More recently the US Biden government issued a memo to US Businesses in summary June 2, Stating the 5 best practices – one being Multi Factor Authentication. Other important aspects are multi-pronged backup Updates, Incident Response, external testing and network segmentation.
6. Has the Covid pandemic exacerbated security concerns or introduced new ones for businesses to deal with?
David: Probably, due to homeworking and fast transformations of moving office servers to the cloud, as well as an increase in Ransomware attacks, an increase in Data Protection legislation globally and the increase in corporate security concerns due diligence.
It has been an increasing challenge for a Head of Security. We have seen an increase in demand from due diligence enquiries, especially for more detailed homeworking policies and guidelines. So, the lines have blurred as to what is home device or a work device. The “physical office” is now the home office, and mandating rules now have to be guidelines that are appropriate – as well as using more layers of defence to protect staff and corporate assets.
7. Do you think businesses focus too much on the technical/technology element of security (e.g. AI solutions)? What other areas do they need to consider?
David: Potentially yes, without an end-to-end strategy, it makes security technology “tactics” unlikely to see a ROI, Return on Investment.
As Head of Security, I see the human element of security is also overlooked quite often. Especially when you consider that almost half of all security breaches are caused by human error. This is even more disconcerting when you consider that only 60% of employees will report a security breach too.
We are actually hosting a free webinar on that subject on 29th July 2021 at 1pm, so if you’d like to know more register for free.
8. How important is cyber-security education? What are the challenges for a Head of Security conveying the risk/educating business? Who in the business needs to receive education/training and how often?
Education is very important, as is having the appropriate training for each role ideally aligned to the companies risks – so that maximum benefits can be realised e.g. developers would require different training from HR staff, as the risk they are managing are different.
Of course, there will always be a need for baseline cyber and data protection training. You can find out more about what Security Awareness Training there is available for employers and employees in our article here.
9. Do you feel there is a security skills/talent shortage? What advice would you give to businesses to combat this?
David: I’m not entirely sure. If there is a shortage, there is definitely a misunderstanding of what skills are required.
Personally, I would align the risks and the strategy, then decide what skills are required to make it happen. It may be that companies would benefit from outside help – to formulate the strategy, and always have access to a range of skill levels onboard to achieve skills resilience.
The other issues that many companies seem to come up against are 24/7 and global, so having just one capable Security resource will not be enough to cover these time periods.
10. As Head of Security, what advice would you give to businesses who want to reduce risk and increase their security posture?
David: Manage Risk regularly with key stakeholders.
Ideally do not remove a risk or lower a risk without evidence, from at least the following e.g. a Policy, Procedure, Penetration test, Internal Audit, External Audit or risk committee approval. This will demonstrate accountability and assist in managing data protection, to enable a defensible position in the security posture.
Ensure a multi-layer approach to security. Utilise things like Access control, least privilege, Approved applications, strong email defences, layered endpoint security, centralised control of endpoints and access, plus multiple point backups.
11. If there was one security investment you could recommend to businesses what would it be and why?
David:
One piece of tech most companies aren’t using
To keep companies ahead, Secure Access Service Edge will help with Cyber security and Data Protection. The ROI is great! It releases staff time, and the payback can be in months.
One Framework
You can manage risk and accountability using ISO27001 framework. If you are not going to be certified, ISO27001 also helps align with NIST, SOC-2 and can help align some components of Data protection. It can clearly demonstrate accountability.
Training that is focused to the role in the business is most appropriate, using the “Incident” metrics to tailor training and technology requirements.
One practice
Have a data/Cyber champion in every business function so you’re able to manage threats, risk and increase incident reporting capability to enable “real-time” issue management.
We hope you found David’s current take on Cyber-Security insightful. During his career David has worked across multiple sectors, including financial services, government, utilities and FinTech, working with a variety of clients – from start-up level and SME up to FTSE 100. He previously held the role of Global Head of IT Security at BT and Radianz (formally Reuters). He’s also been responsible for managing the security infrastructure and delivery of ISO 27001 for multi-billion/trillion-dollar environments. He is also an active CISO consultant on our CISO service offering.
In 2021, experts estimate there will be a cyber-attack incident every 11 seconds.
That’s twice what it was in 2019.
And four times the rate five years ago.
These shocking statistics probably aren’t even that shocking. Every Director knows that security is a pressing issue. It’s a topic of conversation in every board room and a significant budget has been allocated to invest in various security measures and solutions.
However, there’s a weak link in the business which is often overlooked. Your employees. While they might not mean to put the business at risk, their actions can do just that.
From clicking on links in phishing emails and actioning fraudulent bank transfer requests, through to connecting to insecure Wi-Fi networks and sharing personal data incorrectly. All these actions can result in a breach or successful attack, causing financial and reputational damage.
Most employees are not malicious, they simply are not aware of the risks. They don’t understand that they are a target, and they don’t know how to spot the danger signs. Many don’t understand that security is their personal responsibility and even fewer understand sensitive data privacy best practices. Thankfully, this can be easily addressed with effective security awareness training. In this article, we will cover the benefits and types of security awareness training, as well as best practice tips to follow for an effective program.
What is security awareness training?
Security awareness training is designed to educate employees about the important role they play in helping prevent information breaches. It provides formal education about the type of risks facing the businesses, how employees might interact with them or be targeted by them, and how their actions can have a positive or negative affect.
‘Real-life’ scenarios – for example, demonstrating how their response to a phishing email could cost the business thousands of pounds – are often included to drive the message home and show the employee what a breach would feel like.
Quizzes, questionnaires, and games can also be used to test employees’ knowledge post-training and identify any weak spots. There are also various online systems that train and test employees in an automated manner, flagging those users who need additional focus and training.
Why is security awareness training important?
Security awareness training ensures everyone in the business is aware of the threats and how they might present themselves. It helps build a security-aware culture and encourages everyone to follow best practice. For example, instead of the accounts department immediately actioning a bank transfer due to an email from the Financial Director, they know to double-check the request with another method (e.g., a call, a Teams message).
A more security-aware culture will significantly reduce the chance of a successful attack against your business. Research found that security awareness training could reduce the threat of socially engineered cyber threats by up to 70%
Training is also a requirement for compliance purposes in certain industries. The Financial Conduct Authority (FCA) states:
“Firms of all sizes need to develop a ‘security culture’, from the board down to every employee. Firms should be able to identify and prioritise their information assets – hardware, software, and people. They should protect these assets, detect breaches, respond to and recover from incidents, and constantly evolve to meet new threats.”
Types of security awareness training
- Phishing – Trains employees on how to recognise potential phishing messages by demonstrating what could happen if they respond to one.
- Passwords – Promotes password best practice, ensuring strong passwords are created and are not used across multiple accounts or shared with others.
- Privacy PII – Shows employees how to protect personal information in the business, including clients, prospects, colleagues, and partners.
- PCI Compliance – This training is required to comply with the PCI DSS (Requirement 12.6). Educates staff on the requirements, roles and processes and demonstrates the severe financial and reputational damage of a payment card data breach. Reinforces best practice to help staff actively keep card data safe and reduce the likelihood of a breach.
- Ransomware – Demonstrate to employees just how easy it is to be attacked and the destructive consequences.
- CEO/Wire Fraud – Fraudulent emails designed to trick the employee to think they are responding to the CEO (or another senior executive), which shows them how easy it is to be conned. Helps employees to recognise the first signs of risk and encourages the practice of double-checking when unsure how genuine a request is.
- Data in Motion – Teaches employees data security best practices to ensure vulnerable data is not put at risk. Highlights the dangers of behaviours such as sending company attachments to home email accounts, copying company data to personal cloud storage, plugging ‘found’ USB drives into company devices
- Office Hygiene – Educate employees on the importance of physical security, demonstrating the risk of unsecured paper, unlocked screens, open buildings and more.
- GDPR – Ensure all employees are aware and understand data privacy rights – and the severe penalties for breach or non-compliance.
- Social Engineering – Train employees on the various methods and guises hackers may use to gain illegal access to their computer, including phone, email, mail or direct contact.
How often should train employees?
Ideally, every four to six months. There are various software solutions that test and train users more frequently than this, perhaps weekly, however they do not cover all areas of cyber-security.
Research found that after four months, employees were easily able to spot phishing emails but after six, they began to forget the learning. Although this research was specifically about identifying phishing emails, it can be applied to all types of security awareness training.
However, it is up to you to determine the right cadence. Use this timeframe as a starting point. In the beginning, you may need to test employees more frequently.
The key is to strike the right balance. Employees need to be informed and educated, but you want them to be proactively engaged. Training that occurs too frequently risks becoming a chore and treated as a tick box exercise. Employees rush to get it done, rather than engage with the learning, as they know they will have to do it again in a few weeks.
How expensive is security awareness training?
The cost of security awareness training will largely depend on the provider, the type of training and the number of employees. Some providers often tiered pricing with different training methods at each tier. As an example, some of the automated training and testing systems for training users, particularly around phishing and ransomware can be in the region of £12 a year per user.
However, with the average cost of a data breach $3.86 million, the cost of your training program will unlikely ever come close to the cost of a successful data breach. In fact, research shows that employees with less than 1,000 employees will see an ROI of 69% from a security training program.
Best practice tips for an effective training program
Effective training needs to deliver the right information, at the right level, at the right time.
1. Repeat, repeat, repeat
Staff will only recall approximately 90% of training after a month. So, a programme of sustained and repeated training is the best way to ensure knowledge retention.
Plus, the cyber-security landscape is rapidly and constantly developing. New threats occur all the time and you need to equip your staff to deal with them.
2. Gamify your training
Mandatory training can seem dull, leading employees to switch off and become disengaged. You need to ensure these important messages are hitting home. Experiential learning through game-like approaches can help some staff members remember things more effectively.
Studies show that using humour and entertainment in the training process boosts engagement. Nearly 60% of employees prefer training which mixes serious and entertaining content.
3. Break training down into manageable chunks
Hours of back-to-back training is unlikely to engage anyone. In fact, your employees will probably just see it as another ‘tick box’ chore – not ideal for building a security-aware culture. Instead, break your training into bite-size chunks, spread out across the year.
4. Try different methods
Employees all have different methods of learning. What suits one may not suit another, so it’s important to switch up training delivery. Posters, books, quizzes, games, interactive demos and small group training are just some of the ways to educate employees. Unfortunately, you can’t just buy an online training and testing package and believe that’s your training box ticked.
5. Cover a range of topics
While phishing is a top attack vector, it’s important that your training does not focus solely on one area. You need to educate your employees on a wide variety of topics, including those which they might not connect directly with the workplace. For example:
- Not to overshare information on social media
- Dangers of public Wi-Fi and how to use it safely
- Not to plug unknown USB devices into corporate devices
- How to manage passwords
We all know that IT brings a wealth of benefits to any business. From allowing employees to work more effectively and supporting better collaboration and communication, through to enhancing service delivering and increasing customer satisfaction. Technology is now involved, in some part, in almost every area of operations and critical process – regardless of the sector or size.
However, the more entwined IT is with the business, the greater the potential exposure to IT risk. These types of risks can have a catastrophic impact, so it is vital that businesses identify IT risks, take steps to control them, and develop a robust response plan in the event of an IT-related crisis
What is IT risk management?
IT risk management is the policies, procedures, and technologies a company uses to protect their business from threats and mitigate their impact. It is essentially focused on reducing technology vulnerabilities which can affect the availability, confidentiality, and integrity of systems and data.
By identifying and evaluating potential IT risks, businesses can be better prepared for potential threats, minimise the impact of an incident and recover faster should something happen. Managing IT risk also helps guide further strategic planning by ensuring risks which may impact the business achieving its goals and objectives are identified and controlled effectively.
What are some examples of IT risk?
Threats to your IT environment can occur internally or externally, and they can be unintentional or deliberate. The potential risks are numerous, but can typically be broken down into the following categories
- Physical Threats: As a result of physical access or damage to IT resources. This could include theft, fire or flood damage, natural disasters, extreme weather, or unauthorised access to confidential data – either internally or externally.
- Security Threats: Where cyber-criminals or other malicious actors attempt to compromise your business. This could include computer viruses, malware, ransomware, phishing/vishing, business email compromise (BEC), and or other targeted attacks. Or it could involve the business, or an employee, falling victim to a fraudulent website or email.
- Technical Failures: Such as software bugs, unpatched software, system weaknesses, computer crashes or complete failure of a core piece of infrastructure. Technical failures can be catastrophic, for example, if a hard drive was corrupted and there was no way to retrieve the data. This could also include legacy technology which is difficult and expensive to maintain.
- IT Management Failures: Where a company fails to embrace new technologies or methods of working, which result in lost opportunities and reduced productivity and efficiencies. It could also include failing to deploy new software releases or updates, leaving the company open to bugs or security flaws which could be exploited by cyber-criminals.
- Infrastructure Failures: This could include things like the loss of your internet or telephone connection.
- Human Error: Such as an employee accidentally deleting important data, failing to follow security procedures properly, or losing a corporate device.
- Supply Chain Error: The disruption of critical IT processes outsourced to IT service providers and vendors.
- Operational Risk: The risk of technological failures disrupting core business processes.
- Compliance Failure: The failure to comply with industry or geographical regulations (e.g. GDPR) or regulatory bodies (e.g. the FCA, ICO)

Why does the board of directors need to be involved with IT risk management?
It’s understandable why businesses may think that IT risk management is the sole responsibility of the IT department. It is risks related to the use of technology. Technology typically falls under the IT department, therefore, that’s where IT risk management also lies.
Yet, technology isn’t the whole story.
A simple technical failure, such as the email system going down, can affect multiple teams across the business as well as clients and prospective clients. Depending on the length of downtime, this can result in lost productivity, lost revenue, and reputational damage. All of which will be reflected in the bottom line.
IT risk affects the whole business. Not just BAU operations, but the long-term goals and objectives. This risk must be considered and evaluated when determining the strategic direction of the business, which is why it is essential that the board of directors take ultimate accountability for it.
The IT department should certainly be involved in the process, as they will have a wealth of knowledge and understanding of the technical risks and the changing landscape, but it’s essential that the board understand the commercial impact as well. They need to know what the IT risks are, what the potential impact is, and the likelihood of that risk occurring, in the context of the business environment.
Only with this information can effective planning and resource allocation take place. Personnel may need to be allocated to undertake projects to address certain risks. The budget may need to be redistributed, allocated, or increased to take mitigating actions. It all depends on the board’s appetite for risk, but again, this tolerance level can only be determined with a complete and clear understanding of all the risks.
Of course, this is not to say that board members need to involve themselves in the minutiae of day-to-day monitoring. Everyone within a business has a role to play when it comes to successful IT risk management. Once the risks have been identified, categorised, and catalogued, responsibility can then be cascaded to senior personnel. They would then hold responsibility for identifying plans to mitigate that risk, and regular monitoring.
However, IT risk management should be a standing item on the board agenda. This is not an item which can be ticked off the to-do list. It is an item which needs to be reviewed and re-evaluated periodically. The rapid pace of change in the technology and business landscape means not only do the identified risks change, but there are new ones to review. There will be new technology to consider, which comes with its own complex risks. The context in which you evaluate these risks will also change as your business develops. What was once a high risk may become lower, or vice versa. As businesses are required to be more agile in practice and operation, so must they be too when it comes to IT risk management.
Taking accountability for risk
IT risk management is a business investment. One which will help companies safeguard their ability to achieve their long-term goals. It requires commitment at board level and continual review. The pace of change in the IT landscape is so rapid that not only are their new risks developing all the time, but there is the risk that the business will be disrupted if it does not take advantage of opportunities.
The process requires a blend of strong IT and commercial expertise, as the board will need to strike a delicate balance when it comes to risk appetite. An extremely high tolerance could put the business in harm’s way with unnecessary risk from being on the ‘bleeding edge’. On the other hand, extreme risk aversion can stifle innovation and development, leaving the business lagging in the market and missing out on opportunities.
Boards should not be afraid to seek external counsel from a CIO-level Consultant to manage this process. Even where a business has an internal IT resource, a CIO can provide additional expertise. For example, translating the technical risk identified by IT into commercial terms for the board and assessing the impact on business strategy.
What are the essential cyber-security measures every business needs?
In today’s digital era, advancements in technology are happening very rapidly. Therefore our defence systems against very real cyber-security threats must keep pace. If the correct measures aren’t taken, your business might be more at risk than you think. Here are 9 essential cyber-security measures your business can take.
Are you relying on the same security basics you were a few years ago?
It’s easy for time to pass unnoticed while all these advancements happen around us. Before you know it, you’re relying on the same old security basics to protect your business as you were a few years ago – firewalls, antivirus and intrusion detection software. Most people update their mobile phone software more frequently than that. So here are our 9 recommendations on how to keep your company more secure.
Why is it so important?
The truth is, we all feel impervious to cyber-crime and security breaches. It’s just something that happens to other people – until one day it’s not. Even if a direct financial attack is not a concern for a business because that’s locked down, many people are unaware of the intrinsic value of the data their business holds in today’s world.
Hackers aren’t just after your bank accounts.
Cyber-crime is now an industry that produces over £1 trillion in revenue for cyber-criminals. Ransomware can be used to encrypt a company’s files and hold them for ransom. Network penetration can enable mass data theft and crypto-jacking to harvest crypto-currencies by stealing your machine’s processing power. Money can even be gained by using social engineering to persuade employees to transfer cash to a fake bank account.
9 steps to combatting cyber-threats
- A Unified Threat Management (UTM) system
A UTM system is a combination of security appliances and acts as your gateway to the internet. - A SPAM filter
A Spam Filter tops potentially malicious files from entering your network via email. - Antivirus/anti-malware software
Antivirus and Anti-malware are applications that protect your servers, laptops and other devices from malware. - A patch management system
A Patch Management System manages the installation of software updates to close security holes. - 2-Factor authentication
2-Factor Authentication gives you a second level of security, preventing unauthorised sign-ins. - Device encryption
Device Encryption makes any data stored on the machine useless to criminals and keeps your data secret. - A regular data backup
Regular data backups. You should keep a copy of your business data at a secure off-site location in case the original is lost. - Content filtering
Content filtering prevents access to dangerous or illegal websites which reduces the risk of infection. - A disaster recovery plan
A Disaster Recovery Plan sets out how you will recover from an unplanned event such as a fire or cyber-attack.
Regulatory fines and costly lawsuits sting victims of cyber-crime too.
Keeping businesses cyber-secure is even more important since the implementation of the General Data Protection Regulation (GDPR – tailored by the Data Protection Act 2018). Businesses are responsible for their data leaks or breaches if the correct security protections/protocols have not been put in place. Hefty regulatory fines can be levied, and costly lawsuits can follow for the victims of a cyber-attack or security breach.
All businesses should ideally be looking into taking more than just the bare minimum steps to keeping the company cyber-secure, but it’s at least these 9 steps that start the journey in the right direction. The next step beyond the basics is to become Cyber Essential certified.
Cyber Essentials is a Government-backed Accreditation
Cyber Essentials is a government-backed accreditation that acts as a way to understand where your security succeeds and where it needs improvement. It’s similar to a cyber-security audit and allows you to see what your next steps in improving security will be.
Cyber Essentials still covers fairly basic security concepts, such as having the ability to remotely wipe devices, application whitelisting, daily virus scans and the disabling of OS utilities. All of which are simple things that you should already have in place. But it’s well worth going through the accreditation process if you haven’t already – it can improve your company’s image as well as open you up to working with more cyber-conscious clients.
While WhatsApp is a consumer-grade application, many people are using it for business purposes. It’s free and it’s easy to use – most people are probably already using it – so it seems like the ideal communication tool, particularly now many employees are working remotely.
But is WhatsApp really suitable for business communication?
Privacy Policy Updates
WhatsApp was acquired by Facebook in 2014. At the time, CEO Jan Koum stressed how deeply he valued the ‘principle of private communication’. However, just two years later, in 2016, both apps announced they would be ‘coordinating more’– but did give users the option to opt-out of sharing their personal data with Facebook.
This time around, there is no opt-out.
Users who want to continue using WhatsApp after May 15th 2021, have to agree to the updates made to its terms and privacy policy. This means being prepared to share their personal information such as names, profile pictures, status updates, phone numbers, contacts lists, and IP addresses, as well as data about their mobile device, with Facebook and its wider companies. Users who don’t accept the new terms will be blocked from using the app. The new policy, which applies to all users outside of Facebook’s European Region (including the UK), also means that simply deleting the app from the device will not prevent WhatsApp from retaining a users’ private data.
Since the privacy policy changes were announced, WhatsApp has now said that it will not be sharing personal data from people who previously opted out of sharing their information with Facebook. According to The Register, this setting will be apparently be honoured going forward next month, even if you agree to the new policy. For all other users though, there is no opt-out.
A WhatsApp spokesperson also said this update ‘primarily centres around sending messages to businesses to get answers and support’, claiming there will be no change in data-sharing for non-business chats and account information. However, there has been much criticism and concern about the update online.
Update: 12th May 2021
Originally, WhatsApp planned to roll out its privacy policy update on February 8th 2021. However, due to huge public backlash and confusion, they opted to delay until mid-May. Through a series of updates, WhatsApp attempted to clarify its position, reiterating that the update is mainly meant for businesses using its messaging platform. But nonetheless, WhatsApp stated that the change would not impact “how people communicate with friends or family” on the platform. The company also specified in a blog post that it would continue to provide end-to-end encryption for private messages, and it didn’t keep logs of its users’ messaging and calling.
However, despite the clarification around data sharing, there are still plenty of reasons why businesses should stop using WhatsApp for business-related communication
GDPR Compliance and Liability
WhatsApp makes it abundantly clear that the app is designed for personal use in their Terms of Service.
“Legal And Acceptable Use. You must access and use our Services only for legal, authorized, and acceptable purposes. You will not use (or assist others in using) our Services in ways that: … or (f) involve any non-personal use of our Services unless otherwise authorized by us.”
After installing WhatsApp on your device, you’ll receive a pop-up asking for your permission for the app to access your contact. It requests that you ‘Upload your contacts to WhatsApp’s servers to help you quickly get in touch with your friends and help us provide a better experience”. Agreeing to this means that all your phone contacts are accessible in the app. The problem is, it doesn’t distinguish between personal contacts and business ones. Your contacts haven’t given permission for a third party to access their personal data, which could be a potential breach of GDPR.
WhatsApp has been clear that is for personal use. Users must agree to these terms and conditions before they can access the service and WhatsApp can access the users’ contacts. Therefore, the responsibility for GDPR lies with the user, not the app.
Individuals who use WhatsApp for any business communications are in breach of the terms of service. This limits WhatsApp liability for GDPR because they have given the user all the responsibility for seeking the permission of their contacts.
Security Risks of WhatsApp
Using WhatsApp for business communications is fraught with security risks too. While the app famously boasts security due to its end-to-end encryption, there have been plenty of reported hacks and flaws.
Just last October, security researchers revealed that links to thousands of WhatsApp chats were accessible online. Although there was a quiet change to stop the links from being indexed by Google, the information was still readily available on other search engines. The group’s title, image, description and owner’s phone number were all readily accessible, you didn’t even need to actively join the group.
WhatsApp communications are also notoriously difficult for companies to monitor. It may be possible if they are taking place on a corporate-owned device, but even then, there are multiple hoops to jump through. Companies could require the employee to surrender the device, but to access the content itself, there would need to be an IT policy that states WhatsApp as an acceptable communication channel for business purposes. Although, this policy would be in breach of WhatsApp’s acceptable usage policy. The IT policy should be crystal clear about the firm’s right to access and for what purposes (ensuring these are proportionate), so the employee has no expectation of privacy.
Things get even more complex if the employee owns the device and WhatsApp has been installed outside of a mobile device management (MDM) container installed as part of a BYOD policy. The same policy that applies to the corporate-owned device could be extended to employee-owned ones as well. However, given the device is owned by the employee and used predominantly for personal use, it is doubtful whether a forced surrender and access could be seen a legally proportionate.
If there’s no BYOD policy in place? Access is near impossible. As a personal device, the employee would have much higher expectations of privacy and there would need to be an extremely compelling reason, akin to a criminal offence, for an employer to try and obtain access.
What should you use instead of WhatsApp?
While you could write WhatsApp into your IT policies as an acceptable communication channel for business communications, you would knowingly be in breach of the app’s acceptable usage policy.
Plus, even with that in place, there is still a myriad of security, privacy, monitoring and accessibility concerns linked to the app’s business usages. That’s before you even begin to factor in cultural problems potentially caused by the informal nature of the app. Employees could post personal messages to work chats by mistake, accidentally share their live location, or information could get lost between multiple group chats.
Instead, it’s much better to opt for a business-grade secure communication solution. Many of these solutions function in the same way as consumer-grade apps, giving users a familiar interface so they can get started immediately, but with much stronger security. Solutions are available across multiple devices and will protect your voice, video and text data in transit and at rest, preventing accidental leakage or malicious attack.
That’s no simple task with the increasingly complex IT environments and constantly evolving cyber-security landscape. With new threats appearing every day, IT Managers need to build an effective stack of cyber-security tools to help them keep their infrastructure as secure as possible. In this article, we will explore the role of SIEM solutions within that toolset.
What is SIEM?
A Security Information and Event Management (SIEM) solution aggregates and analyses activity from existing resources across your IT infrastructure. It collects security data from devices on your network and applies analytics to discover trends, detect threats, and enable your organisation to investigate any alerts.
A SIEM solution is put in place to protect your IT estate from external attacks. It can be configured to automatically isolate and deal with many detected threats, but it also needs to be closely monitored by skilled engineers to handle more sophisticated attacks and ensure nothing is missed.
HOW SECURE IS YOUR SENSITIVE DATA? FIND OUT TODAY WITH A FREE DARK WEB SCAN
Why SIEM solutions are essential for professional service businesses
Gartner first coined the term SIEM in 2005 when Mark Nicolett and Amrit Williams proposed combining Security Information Management (SIM) and Security Event Management (SEM) to create a new, all-encompassing, security information system.
Since then, the technology has been steadily evolving and improving and has become ever more important as cyber-attacks have increased across the world. A UK government report from earlier this year found that 46% of all businesses suffered cyber-security breaches or attacks in the previous 12 months. And this figure rose to 68% for medium-sized businesses.
A 2020 global IBM security report found that the average cost of a data breach, including lost business due to increased customer turnover, lost revenue due to system downtime, increased cost of acquiring new business due to diminished reputation, and remedial work to resolve the data breach was £2.87 million. This is in no small part down to an average time of 280 days to identify and contain a breach. The report also found that businesses with fully deployed security automation in the form of a SIEM solution saved an average of £2.6 million when dealing with a data breach compared to those with no security automation.
Prevention is always better than cure for any part of your IT infrastructure, and when there is such potential to incur significant costs, it makes sense to invest upfront in protecting your business.
What are the main benefits of a SIEM solution?
1. Data aggregation and normalisation
The larger and more complex your IT infrastructure becomes, the more difficult it is to keep track of every single link between devices and applications across your network. This can lead to opportunities for hackers to exploit and access your systems unbeknownst to you until they choose to launch their attack. SIEM solutions gather security event information from the entire network at a central point, uncovering any potential vulnerabilities or malicious activities. This data is then normalised or reformatted as required by your organisation so that it can be easily understood by your staff and dealt with swiftly and efficiently.
2. Threat detecting and security alerting
SIEM solutions can connect your security team to multiple threat intelligence feeds so that they are always up to date on the latest threats to businesses like yours. Coupled with the aggregation and normalisation of the data across your network, SIEM solutions perform real-time analysis of potential threats then log alerts for your incident management team to investigate and resolve as quickly as possible.
3. Regulation compliance
Virtually every business in every industry requires the fulfilment of at least some regulatory mandates such as GDPR and ISO 27001. This is even more true for professional services businesses and failing to meet these can result in loss of sales or expensive lawsuits.
Many SIEM solutions provide out-of-the-box report templates for most compliance mandates and often much of this information can be collated automatically to save your security team time and resources.
4. Increased efficiency
Incident handling is streamlined by the data across your network being collated in one place, allowing security threats to be dealt with as quickly as possible. As well as having a direct impact on your security team, this can lead to a wider reduction in incidents across your IT department as potential attacks are identified and dealt with before they can create incidents for other teams to deal with.
5. Customer attraction and retention
By showing customers and prospects that you have a fully functioning SIEM solution, you can give them confidence that their data will be safe with your organisation, and the service you provide them will not be threatened by a cyber-attack. Conversely, if your business is the victim of a cyber-attack and is unable to deal with it efficiently and effectively, it may take years for your reputation to recover to previous levels. In the short term, this can result in the loss of existing customers and, in the long term, a significant increase in the cost of acquiring new business
How to choose the right SIEM solution for your business
Defining your requirements
As with any IT project, you can’t do anything until you are 100% clear on your requirements. For SIEM solutions, these fall into two distinct categories:
1. Collection, storage and compliance:
- What data sources do you need to log, and do you need to collect all data or a subset?
- How long do you need to store the data for?
- What compliance regulations do you need to meet?
2. Analysis, reporting and personnel:
- How will you use your data once collected?
- What sort of reports do you need, and do you need the ability to customise them?
- Do you have existing expert staff in-house who can manage the solution, or will you need external assistance?
Assessing available solutions
SIEM solutions can be purchased as an appliance or an application. And they can be implemented and managed entirely by your own team or purchased as a service from an outsourcing provider who can do the implementation for you and provide ongoing management if required. Once you have defined your requirements, you can identify the products which best match and request demonstrations. At QuoStar we have a team of security experts who can assist you in identifying the most suitable SIEM features for your organisation and arrange a live demonstration to help you make the best choice.
Deployment
You need to understand how the solution will be deployed within your organisation before you make your final decision. It’s critical that you are confident in the provider as, even if you are doing the implementation yourself, you will require their expertise for the more technical aspects. If you decide to engage a partner to deploy the solution for you, you need to be comfortable that they have a full understanding of your network and requirements, as well as the SIEM product itself.
Ongoing SIEM management
Any SIEM solution is only as good as its administrators. You need to have a plan in place from the start in terms of who will manage it on a day to day basis. Both in terms of the administration of the solution and the management of incidents created by the SIEM tools.
What else do you need to know about SIEM solutions?
The most important thing to understand is that the successful implementation of a suitable SIEM solution is not the end of the journey. It is only the beginning. The landscape is constantly evolving – both within your network and externally in terms of the cyber-threats you face. If you are not regularly reviewing your SIEM tools and features, you run the risk of being compromised by a new form of attack.
At QuoStar, our security experts are constantly reviewing the latest trends and assessing these against our clients’ existing setups to ensure everyone is fully protected.
We can provide a fully outsourced Security Operations Centre (SOC) incorporating SIEM and any other tools which are critical to the security of your IT network, allowing you to focus on other key projects safe in the knowledge your infrastructure will not be compromised by any malicious external threats.
The COVID-19 has had a huge impact on the way businesses deliver IT services to end-users. The lockdown and subsequent restrictions left businesses scrambling to deal with an unprecedented situation where their entire workforce needed to work from home. Most simply weren’t set up for permanent, widescale remote working but had no option but to embrace it to remain operational.
Technology like online meeting and collaboration tools, hosted telephony, VPNs and virtual desktop infrastructure (VDI) saw a surge in adoption as businesses looked for ways to keep their employees connected, productive and secure. Of course, VDI solutions are nothing new. Businesses have been using it for over a decade to deliver desktops and applications to end-users. However, it is seeing a resurgence, both due to current challenges arising from COVID-19 and the maturation of Windows Virtual Desktop. This was highlighted in the recent Spiceworks Ziff Davies 2021 State of IT Report which found 46% of businesses were using or planning to use VDI by mid-2022. Furthermore, 26% of businesses planned to increase VDI deployment specifically because of the new challenges that have surfaced due to the pandemic.
How can VDI solutions help internal IT Teams?
1. Reduced Costs
Delivering desktops through VDI helps reduce the time it takes to provision new desktops. Easy and quick to set up, VDI not only reduces the time required by the IT team and the support costs, but it also provides more immediate value to the business.
VDI can also help IT Managers optimise and reduce their IT spend. Purchasing and upgrading hardware for remote employees is a significant cost, but as a virtual desktop can be accessed from almost any device it can really help slash spend in this area.
2. Simplified Licencing
Software licencing is one of the most common issues for IT managers with remote employees. If an end-user uses a personal device for remote working and needs a particular app to do their job, it’s ITs responsibility to licence this. Not only do multiple licences increase IT costs, but it also complicates licence tracking and compliance. The IT team needs to be able to prove that apps on personal devices are properly licenced and differentiate between corporate-owned software and personally owned software. VDI solutions eliminate this challenge for IT teams by keeping the licenced software within the business’s own data centre and removes the need to track remotely installed apps.
3. Improved Security
Security is a constant concern, even more so with the new threats emerging as a result of the pandemic. It’s a particular issue for IT teams where end users are using personal devices to access company data or systems. There are no guarantees that the device adheres to the company security policy, it may be infected, compromised or running an outdated operating system. However, with VDI, device-level security becomes less important as the user remotely connects a corporate desktop which IT configures to exact security requirements. The personal PC essentially becomes a thin client as all activity takes place in the data centre, with all of the corporate security systems and controls in place.
IS CONFIDENTIAL DATA LEAKING OUT OF YOUR BUSINESS? FIND OUT TODAY WITH A COMPLIMENTARY DARK WEB SCAN
4. Reduced Technical Support Time
IT Managers’ workloads are higher than ever now they need to manage a fully remote workforce on top of their existing responsibilities. VDI solutions make it easier for IT teams to support remote end-users because it puts them in a standardised environment, with the device itself less significant. It also reduces major technical issues and speeds up resolution time because IT teams already have all the information about the user’s virtual desktop systems to hand. Of course, technical issues can still occur with virtual desktop users, but these are usually related to connectivity and performance and are simpler to identify and resolve.
5. Centralised Management
With everything centrally stored, managed and secured, desktop virtualisation streamlines the management of software assets. This makes it easier for the IT team to set up and provide end-users with desktops and applications, no matter where they are located. Administrators can also deploy, patch, upgrade and troubleshoot from a central, singular location, rather than updating end-users’ environments individually.
Are VDI solutions the right choice for every business?
Desktop virtualisation has continually developed over the last decade, but today the main two categories are VDI and DaaS (Desktop as a Service). VDI is suited to businesses who want to host and manage the virtual desktops themselves, on their own servers. DaaS is very similar but removes the need for infrastructure management by delivering it as a cloud service.
Both VDI and DaaS are well placed to deal with the most common challenges of traditional desktop and laptop systems, such as software licencing inventory, ensuring compliance and expensive procurement. Outside of these legacy challenges, both solutions also help businesses deal with IT process concerns, such as keeping up with the rapid pace of change and the time IT staff have to dedicate to routine tasks (e.g. troubleshooting, helpdesk requests).
DaaS has a slight potential edge on VDI due to the shared responsibility of a cloud model. It largely removes the need to manage the physical infrastructure, enabling IT teams to focus on the entire digital workspace and user experience.
The prominent solution that overlaps both categories is Windows Virtual Desktop (WVD). Previous virtualisation options gave businesses limited options over the type of virtual machines they could use to deliver desktops. They had to either compromise on user experience and deploy Windows Server Desktop experiences to achieve the cost benefits of a multi-session. Or, they had to sacrifice on cost and deploy single sessions in Windows 10.
This dilemma, plus the opportunities presented by Azure as a platform, ultimately led to the development of Windows Virtual Desktop (WDS). It’s the only virtual desktop infrastructure that offers simplified management, multi-session Windows 10, optimisations for Office 365 Pro Plus and support for RDS environments. An additional plus, just for IT teams, is the relatively short time to go live. A 100 person business with 4-5 servers could be looking at less than a week to set up from scratch.
Are there any issues with VDI solutions?
However, like any technology option, VDI is not a one–size–fits–all solution. Businesses still need to fully evaluate its suitability for their employees and their ways of operating. For example, while VDI is a good option for remote workers and contractors who need to securely access Office applications, it’s not the best for employees who travel frequently due to latency and VPN issues.
Certain applications also still don’t perform as well in VDI style solutions. Microsoft Teams and Zoom are two of the most widely used conferencing platforms, yet they both have performance issues and limitations in VDI environments. For example, with Microsoft Teams some advanced features may not be available in a virtualised environment, and video resolution can differ. Call and meeting functionality is also only supported on a limited number of platforms. As there are multiple market providers, it’s recommended that you seek consultancy advice or speak to your virtualisation solution provider to confirm you meet the minimum requirements.
VDI is just one element of the technology stack. Don’t forget you’ll need other complementary technologies to address gaps and round out the experience for the end-user if you’re looking to build a fully functioning digital workplace.
The Question
“Our teams have been working from home since March and while overall it seems to be working well, I think some employees aren’t really working as they should be. Should I be using monitoring software to track their productivity?“
The QuoStar Answer
Well, this is a relatively common question and one I’m sure many managers have contemplated in the previous six months. Since lockdown, demand for monitoring software has soared. Searches for ‘employee surveillance software’ are up more than 80% and some providers have seen a threefold increase in demand for their tech.
However, employee monitoring is nothing new. In 2019, over 50% of large organisations were already using ‘non-traditional methods’ to monitor their employees, such as analysing email text, logging computer usage or tracking employee movements. Even employees themselves are beginning to expect a certain level of monitoring and believe it will increase in the future.
Advantages and disadvantages of employee monitoring
The benefits of employee monitoring are probably widely known. Many studies have shown that when people know they are being monitored, they behave in the way they think is expected. In other words, they become more productive.
The real–time data collected by tools can, if utilised correctly, help uncover problems and identify bottlenecks. You can allocate resources more effectively and rework processes to prevent employees from having to spend more time than necessary on certain tasks. It will also allow you to identify employee strengths and weakness, giving opportunity for both praise and further training
A welcome side effect, particularly in the current climate, is enhanced data security. As an example, some tools can alert you to suspicious activity or block certain actions from happening altogether, such as the opening of certain applications.
However, all these potential benefits can be instantly wiped out by a poorly handled rollout. Attempts to be covert or any dishonesty about the true purpose of monitoring will likely be viewed extremely negatively. Your employees may feel that their privacy has been devalued or violated, and like the company no longer trusts them. It may result in diminished morale and elevated stress, harming your ability to retain staff in the long run.
Legal implications of monitoring employees at work
While employers are well within their rights to monitor activity on ‘business-owned’ devices, it’s a fine line to tread. You need to find a balance between employees’ legitimate expectation to privacy and the company’s interests, and there must also be a legitimate purpose for the monitoring.
The Information Commissioner’s Office (ICO) states that employees should be made aware before monitoring begins, told the reasons for its use and how the information collected will be used. Government guidance also states that employers must clearly explain the amount of monitoring in the staff handbook or contract. This includes telling workers if they’re being monitoring, what counts as a reasonable amount of personal emails and phone calls, and if personal emails and calls are not allowed.
You will need to carry out a formal ‘impact assessment’ to justify the use of monitoring tools before any go live. This identifies the purpose of the monitoring and the likely benefits and adverse impact. As part of the assessment, you’ll need to look at alternative ways the purpose might be achieved; look at the obligations that will arise from monitoring; and whether the decision is justifiable (compared to the effects the employee might experience).
If you’re planning to use the information collected as the basis of disciplinary procedures (e.g. an employee being consistently unproductive) then I would also advise seeking legal advice to determine whether you need to amend your employment contracts to reflect this.
Monitoring software raises the age-old issue of data security and privacy as well. The more that is recorded, the more data there is to secure and protect. Just last month, H&M was fined for collecting extensive details about their employees’ private lives, which was accessible to 50 other managers. So, it’s crucial that you understand exactly how your monitoring tool will collect and store information, particularly if this happening on a third-party system. If the data is stored in a different country to where you’re located, you may need to comply with additional regulations.
What technology is available to monitor employees?
If you feel employee monitoring is both necessary and justifiable, then the good news is there are plenty of tools available. I won’t list specific products or providers, but some features you might look out for include:
- Screen Monitoring – Captures real-time screenshots of a computer’s desktop or active window at set intervals, allowing you to see work in progress at any given point.
- User Activity Tracking – Tracks and collects real-time user actions and behaviour data on company networks and connected and monitored devices. Also known as User Behaviour Analytics (UBA), not only can these tools track productivity, they’re important for security as well. This proactive form of monitoring can help you spot suspicious activity and prevent access privileges from being abused. Some tools will also alert when actions you have marked as ‘suspicious’ happens. For example, if an employee tries to download unauthorised software to a work device, the administrator will be notified immediately.
- Internet Monitoring – Automatically monitors employees’ application and web usage during working hours. Reports break down what was accessed and for how long, allowing you to spot if someone’s spending too much time on certain sites. Most tools can also block, deter or limit employees from accessing unproductive sites during working hours. Usually, companies use these tools to block social media, online gaming portals, and entertainment or streaming sites.
- Time Tracking – Records time spent on projects or tasks. These apps are ideal for companies who bill by the hour, allowing for more accurate invoices, but it can also help with resource allocation. Records can help you identify bottlenecks and investigate whether you should amend processes or provide greater support for employees.
- Keylogging – Keyloggers run in the background to track, capture and record all keyboard activity and mouse clicks. They can track activity across a variety of platforms, including email, instant messengers, web browsers and apps. The data collected can provide insight into daily activity, attitude, professionalism and productivity.
- Call Recording – For industries, like recruitment, where communication is necessary for successful outcomes, your telephony system should be able to give you the insights here. Some hosted telephony and VoIP tools offer in-depth metrics including time on the phone, time to answer, who answered which call, and calls made/received/missed.
- Constant Presence Tools – Utilise the webcam to take photos of employees at regular intervals, to check they’re at their desk. With some products, you can see photos all on one screen and click on them to start instant video chat.
- GPS – This may an option if you have employees working at multiple locations or at client sites, as they can allow you to record individual’s hours and locations in one place.
Most software products will offer multiple productivity tracking features, so you don’t necessarily need a purchase a separate product for each one.
Final Considerations
Employee monitoring is a very difficult line to tread. It can never be a simple, blanket yes or no. Every business will need to evaluate the pros and cons in line with their specific processes, operations and culture.
Bear in mind, the current situation is an extreme one. It may be overly simplistic to solely blame ‘remote working’ for impacts on productivity. Employees may have legitimate worries or problems in their personal lives as a result of the pandemic. They might be trying to balance childcare with work, caring for sheltering or vulnerable relatives or their mental health might be suffering. You will need to mindful of the wider circumstances when discussing productivity with individuals, as some may need greater support to achieve their usual ‘office-based’ output.
If this is the first-time employees have ever worked remotely, this is not necessarily an accurate representation of how they would perform in ‘usual’ times. Yes, remote working is not for everyone. Some people much prefer to be in the office, surrounded by their colleagues. Some will always see it as an opportunity to shirk their duties, as there’s no one around to check-in. But I wouldn’t necessarily rush to write off remote working as a complete no-go for your entire business.
If you do decide to go the software route, then ensure you’re transparent about it and be aware of how it might affect your company culture, as well as the legal obligations you’ll need to fulfil.
Just remember that X hours in front of the screen does not equal X hours of productive work. Yes, these shiny new tools that take photos of employees at their laptop and track their GPS location, are great but they alone cannot paint a true picture. Arguably, working hours aren’t the most important thing, it’s the output of those hours. You need to identify meaningful KPIs and regularly track these to really assess an employee’s contribution to the business. A slightly extended lunch or an extra short coffee break in the afternoon might not be the end of the world if the work is still being done.
It’s all about balance at the end of the day.
Many people believe that email scams are easy to spot, but even email scams that target businesses?
They’re poorly written, full of spelling and grammatical mistakes and usually contain an offer which is too good to be true… right?
Things have changed a lot since those days. Email scams are now alarmingly sophisticated, personalised and as a result, much more dangerous. Hackers now take the time to craft messages tailored to a single recipient, meaning that even experienced users can be fooled.
We’ve listed some of the most common email scams below which you should be aware of. Remember, if you receive a suspicious email, don’t respond until you can confirm the request is 100% genuine.
1. SPAM
Not necessarily all of it is malicious, but it is illegal in many countries. SPAM is repetitive, unsolicited bulk emails which the recipient hasn’t requested to receive. Most commonly these are commercial in nature, but they can also include things like chain emails.
There are two origins of SPAM emails. SPAM which comes from spammers themselves who are selling products or attempting to commit fraud. And SPAM which originates from computers infected with a virus or worm that are sending out bulk emails. This is the type which tends to more often be malicious.
2. Phishing
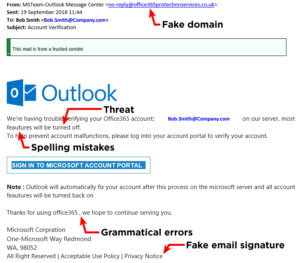
This is a type of scam intended to trick you into entering personal information like usernames or passwords. The best way to identify a phishing email is to look at the from address and verify that it’s real. This can be difficult when the domain (the bit after the @) is similar to the legitimate version. But a quick message to the genuine sender (don’t reply directly to the suspicious email!) can verify if it’s legitimate rather quickly.
Phishing emails usually try to scare or tempt you into submitting your details. After all, if ‘[email protected]’ said you were the lucky winner of a £500 voucher, who wouldn’t want to claim that by entering their account details. Or if ‘[email protected]’ told you that they had detected suspicious activity in your bank account and needed you to sign in to reactivate your credit and debit cards, why wouldn’t you.
These may seem like obvious fakes, but this kind of stuff works on the best of us. All it takes is one click when we’re rushed and panicking or when we’re not paying full attention at the end of a long day.
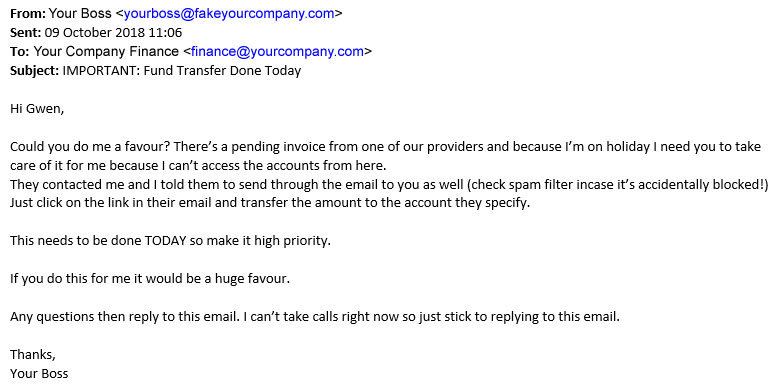
3. CEO fraud / Business email compromise (BEC)
This type of scam is where someone pretends to be the CEO of your company. It usually involves a request to the finance department for a money transfer.
A real looking email address can be set up using information easily harvested from social networks. Scammers can now easily address your finance department on first name terms, using an account with your CEO’s real name and real picture. Or alternatively, gain access to the real account through a phishing campaign, letting them send emails from there.
A sophisticated scammer might also be stalking your CEO’s social accounts. Learning exactly when they’re out of the office or on holiday and only sending their email then, requesting emergency funds for an important client deal that’s come to them whilst they’re away.
Of course, the account they ask you to send the money to isn’t really related to your business or any clients and is owned by the scammer.
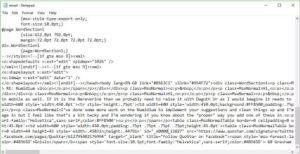
4. Spoofing
Spoofing involves forging email headers so that emails appear to originate from a genuinely legitimate source. Not to be confused with setting up a similar address. Spoofing is where a scammer tricks the email server into genuinely thinking that an email came from who the scammer says it did.
Spoofing is a common technique used by hackers and can occur in many forms. But the most common is to try and use the authority of their disguise to trick users into visiting a malicious website or downloading a malicious file.
The biggest issue with spoofing is that there is no way for an average user to find out that the email is illegitimate. Both the sender name and sender address will appear as legitimate (not slight alterations or misspellings). And if the sender is a known contact of the recipient their email program will ‘handily’ populate the email with their profile picture, custom footers and other information associated with the sender as it would with a legitimate email. This results in very convincing looking emails which are difficult to detect as fake.
The way to detect the true sender is to look at the internet headers by viewing the source of the email Unfortunately this is very difficult to navigate.
Bonus point: Social engineering
Phishing, spoofing and CEO fraud emails are all part of a type of hacking called social engineering which is where scammers use tricks or tactics to gain information from legitimate users of a system. Then they use this information to either perpetrate more scams or sell it on the dark web.
Don’t think that social engineering is exclusive to email though. It can come through any channel of interaction such as social media, phone calls or impersonating trusted parties, like delivery drivers.
Conclusion
While products like SPAM filters remain crucial in the fight against email attacks. You can protect your business with user training – a prime way to protect detect these tactics. Employees are often the weak link when it comes to security, so you should invest in security training. This will help them understand the risks and how to avoid them.