The Question
“Our teams have been working from home since March and while overall it seems to be working well, I think some employees aren’t really working as they should be. Should I be using monitoring software to track their productivity?“
The QuoStar Answer
Well, this is a relatively common question and one I’m sure many managers have contemplated in the previous six months. Since lockdown, demand for monitoring software has soared. Searches for ‘employee surveillance software’ are up more than 80% and some providers have seen a threefold increase in demand for their tech.
However, employee monitoring is nothing new. In 2019, over 50% of large organisations were already using ‘non-traditional methods’ to monitor their employees, such as analysing email text, logging computer usage or tracking employee movements. Even employees themselves are beginning to expect a certain level of monitoring and believe it will increase in the future.
Advantages and disadvantages of employee monitoring
The benefits of employee monitoring are probably widely known. Many studies have shown that when people know they are being monitored, they behave in the way they think is expected. In other words, they become more productive.
The real–time data collected by tools can, if utilised correctly, help uncover problems and identify bottlenecks. You can allocate resources more effectively and rework processes to prevent employees from having to spend more time than necessary on certain tasks. It will also allow you to identify employee strengths and weakness, giving opportunity for both praise and further training
A welcome side effect, particularly in the current climate, is enhanced data security. As an example, some tools can alert you to suspicious activity or block certain actions from happening altogether, such as the opening of certain applications.
However, all these potential benefits can be instantly wiped out by a poorly handled rollout. Attempts to be covert or any dishonesty about the true purpose of monitoring will likely be viewed extremely negatively. Your employees may feel that their privacy has been devalued or violated, and like the company no longer trusts them. It may result in diminished morale and elevated stress, harming your ability to retain staff in the long run.
Legal implications of monitoring employees at work
While employers are well within their rights to monitor activity on ‘business-owned’ devices, it’s a fine line to tread. You need to find a balance between employees’ legitimate expectation to privacy and the company’s interests, and there must also be a legitimate purpose for the monitoring.
The Information Commissioner’s Office (ICO) states that employees should be made aware before monitoring begins, told the reasons for its use and how the information collected will be used. Government guidance also states that employers must clearly explain the amount of monitoring in the staff handbook or contract. This includes telling workers if they’re being monitoring, what counts as a reasonable amount of personal emails and phone calls, and if personal emails and calls are not allowed.
You will need to carry out a formal ‘impact assessment’ to justify the use of monitoring tools before any go live. This identifies the purpose of the monitoring and the likely benefits and adverse impact. As part of the assessment, you’ll need to look at alternative ways the purpose might be achieved; look at the obligations that will arise from monitoring; and whether the decision is justifiable (compared to the effects the employee might experience).
If you’re planning to use the information collected as the basis of disciplinary procedures (e.g. an employee being consistently unproductive) then I would also advise seeking legal advice to determine whether you need to amend your employment contracts to reflect this.
Monitoring software raises the age-old issue of data security and privacy as well. The more that is recorded, the more data there is to secure and protect. Just last month, H&M was fined for collecting extensive details about their employees’ private lives, which was accessible to 50 other managers. So, it’s crucial that you understand exactly how your monitoring tool will collect and store information, particularly if this happening on a third-party system. If the data is stored in a different country to where you’re located, you may need to comply with additional regulations.
What technology is available to monitor employees?
If you feel employee monitoring is both necessary and justifiable, then the good news is there are plenty of tools available. I won’t list specific products or providers, but some features you might look out for include:
- Screen Monitoring – Captures real-time screenshots of a computer’s desktop or active window at set intervals, allowing you to see work in progress at any given point.
- User Activity Tracking – Tracks and collects real-time user actions and behaviour data on company networks and connected and monitored devices. Also known as User Behaviour Analytics (UBA), not only can these tools track productivity, they’re important for security as well. This proactive form of monitoring can help you spot suspicious activity and prevent access privileges from being abused. Some tools will also alert when actions you have marked as ‘suspicious’ happens. For example, if an employee tries to download unauthorised software to a work device, the administrator will be notified immediately.
- Internet Monitoring – Automatically monitors employees’ application and web usage during working hours. Reports break down what was accessed and for how long, allowing you to spot if someone’s spending too much time on certain sites. Most tools can also block, deter or limit employees from accessing unproductive sites during working hours. Usually, companies use these tools to block social media, online gaming portals, and entertainment or streaming sites.
- Time Tracking – Records time spent on projects or tasks. These apps are ideal for companies who bill by the hour, allowing for more accurate invoices, but it can also help with resource allocation. Records can help you identify bottlenecks and investigate whether you should amend processes or provide greater support for employees.
- Keylogging – Keyloggers run in the background to track, capture and record all keyboard activity and mouse clicks. They can track activity across a variety of platforms, including email, instant messengers, web browsers and apps. The data collected can provide insight into daily activity, attitude, professionalism and productivity.
- Call Recording – For industries, like recruitment, where communication is necessary for successful outcomes, your telephony system should be able to give you the insights here. Some hosted telephony and VoIP tools offer in-depth metrics including time on the phone, time to answer, who answered which call, and calls made/received/missed.
- Constant Presence Tools – Utilise the webcam to take photos of employees at regular intervals, to check they’re at their desk. With some products, you can see photos all on one screen and click on them to start instant video chat.
- GPS – This may an option if you have employees working at multiple locations or at client sites, as they can allow you to record individual’s hours and locations in one place.
Most software products will offer multiple productivity tracking features, so you don’t necessarily need a purchase a separate product for each one.
Final Considerations
Employee monitoring is a very difficult line to tread. It can never be a simple, blanket yes or no. Every business will need to evaluate the pros and cons in line with their specific processes, operations and culture.
Bear in mind, the current situation is an extreme one. It may be overly simplistic to solely blame ‘remote working’ for impacts on productivity. Employees may have legitimate worries or problems in their personal lives as a result of the pandemic. They might be trying to balance childcare with work, caring for sheltering or vulnerable relatives or their mental health might be suffering. You will need to mindful of the wider circumstances when discussing productivity with individuals, as some may need greater support to achieve their usual ‘office-based’ output.
If this is the first-time employees have ever worked remotely, this is not necessarily an accurate representation of how they would perform in ‘usual’ times. Yes, remote working is not for everyone. Some people much prefer to be in the office, surrounded by their colleagues. Some will always see it as an opportunity to shirk their duties, as there’s no one around to check-in. But I wouldn’t necessarily rush to write off remote working as a complete no-go for your entire business.
If you do decide to go the software route, then ensure you’re transparent about it and be aware of how it might affect your company culture, as well as the legal obligations you’ll need to fulfil.
Just remember that X hours in front of the screen does not equal X hours of productive work. Yes, these shiny new tools that take photos of employees at their laptop and track their GPS location, are great but they alone cannot paint a true picture. Arguably, working hours aren’t the most important thing, it’s the output of those hours. You need to identify meaningful KPIs and regularly track these to really assess an employee’s contribution to the business. A slightly extended lunch or an extra short coffee break in the afternoon might not be the end of the world if the work is still being done.
It’s all about balance at the end of the day.
Many people believe that email scams are easy to spot, but even email scams that target businesses?
They’re poorly written, full of spelling and grammatical mistakes and usually contain an offer which is too good to be true… right?
Things have changed a lot since those days. Email scams are now alarmingly sophisticated, personalised and as a result, much more dangerous. Hackers now take the time to craft messages tailored to a single recipient, meaning that even experienced users can be fooled.
We’ve listed some of the most common email scams below which you should be aware of. Remember, if you receive a suspicious email, don’t respond until you can confirm the request is 100% genuine.
1. SPAM
Not necessarily all of it is malicious, but it is illegal in many countries. SPAM is repetitive, unsolicited bulk emails which the recipient hasn’t requested to receive. Most commonly these are commercial in nature, but they can also include things like chain emails.
There are two origins of SPAM emails. SPAM which comes from spammers themselves who are selling products or attempting to commit fraud. And SPAM which originates from computers infected with a virus or worm that are sending out bulk emails. This is the type which tends to more often be malicious.
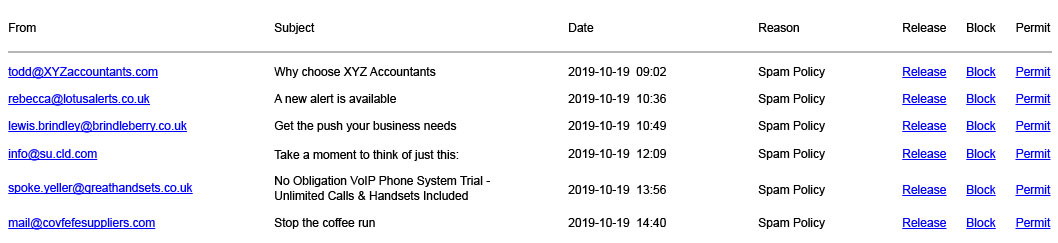
2. Phishing
This is a type of scam intended to trick you into entering personal information like usernames or passwords. The best way to identify a phishing email is to look at the from address and verify that it’s real. This can be difficult when the domain (the bit after the @) is similar to the legitimate version. But a quick message to the genuine sender (don’t reply directly to the suspicious email!) can verify if it’s legitimate rather quickly.
Phishing emails usually try to scare or tempt you into submitting your details. After all, if ‘[email protected]’ said you were the lucky winner of a £500 voucher, who wouldn’t want to claim that by entering their account details. Or if ‘[email protected]’ told you that they had detected suspicious activity in your bank account and needed you to sign in to reactivate your credit and debit cards, why wouldn’t you.
These may seem like obvious fakes, but this kind of stuff works on the best of us. All it takes is one click when we’re rushed and panicking or when we’re not paying full attention at the end of a long day.
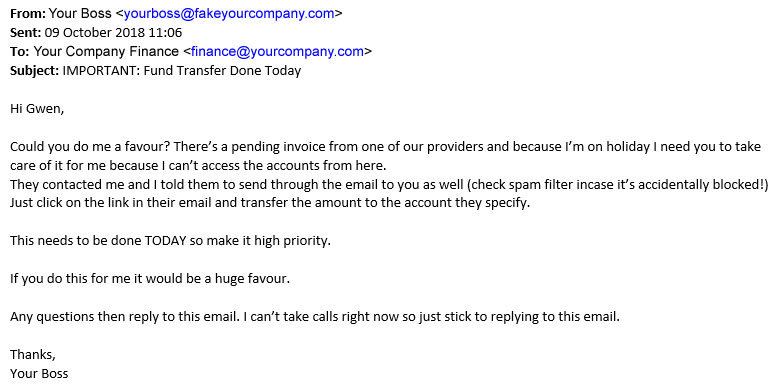
3. CEO fraud / Business email compromise (BEC)
This type of scam is where someone pretends to be the CEO of your company. It usually involves a request to the finance department for a money transfer.
A real looking email address can be set up using information easily harvested from social networks. Scammers can now easily address your finance department on first name terms, using an account with your CEO’s real name and real picture. Or alternatively, gain access to the real account through a phishing campaign, letting them send emails from there.
A sophisticated scammer might also be stalking your CEO’s social accounts. Learning exactly when they’re out of the office or on holiday and only sending their email then, requesting emergency funds for an important client deal that’s come to them whilst they’re away.
Of course, the account they ask you to send the money to isn’t really related to your business or any clients and is owned by the scammer.
4. Spoofing
Spoofing involves forging email headers so that emails appear to originate from a genuinely legitimate source. Not to be confused with setting up a similar address. Spoofing is where a scammer tricks the email server into genuinely thinking that an email came from who the scammer says it did.
Spoofing is a common technique used by hackers and can occur in many forms. But the most common is to try and use the authority of their disguise to trick users into visiting a malicious website or downloading a malicious file.
The biggest issue with spoofing is that there is no way for an average user to find out that the email is illegitimate. Both the sender name and sender address will appear as legitimate (not slight alterations or misspellings). And if the sender is a known contact of the recipient their email program will ‘handily’ populate the email with their profile picture, custom footers and other information associated with the sender as it would with a legitimate email. This results in very convincing looking emails which are difficult to detect as fake.
The way to detect the true sender is to look at the internet headers by viewing the source of the email Unfortunately this is very difficult to navigate.
Bonus point: Social engineering
Phishing, spoofing and CEO fraud emails are all part of a type of hacking called social engineering which is where scammers use tricks or tactics to gain information from legitimate users of a system. Then they use this information to either perpetrate more scams or sell it on the dark web.
Don’t think that social engineering is exclusive to email though. It can come through any channel of interaction such as social media, phone calls or impersonating trusted parties, like delivery drivers.
Conclusion
While products like SPAM filters remain crucial in the fight against email attacks. You can protect your business with user training – a prime way to protect detect these tactics. Employees are often the weak link when it comes to security, so you should invest in security training. This will help them understand the risks and how to avoid them.
The story
At 27 minutes past 2 on a Monday afternoon, the phone on my desk rang. Picking it up I was greeted by Faye Langford (a name I was unfamiliar with) asking if she could speak to the company’s CEO, Robert Rutherford. She said she was calling from one of our suppliers (which has been left intentionally unnamed) about an earlier email regarding problems with a credit card.
As Rob was out of the office, I asked if there was anyone else who could help. I was informed that Rob was the only person on the account and so I told Faye that I would pass on the message. She wished me a good day and that was the end of our conversation.
I emailed Rob the details of the call and was content that the issue would be resolved now it was in the appropriate hands.
This all seemed quite ordinary but here are two things which change that:
- There are two people at this supplier who would normally call us regarding card information. Faye Langford is not one of them.
- There are over 15,000 employees who work at this supplier. Faye Langford is not one of them.
So, what had just happened?
The scam
What had happened was an attempt at voice phishing – also known as vishing. When you think of phishing, you probably think of emails but unfortunately, phishing can occur on any channel. Phone calls, SMS or social media are all platforms which scammers can use to fraudulently acquire your details.
But there are some things which make this attempt particularly alarming.
- They already knew Rob’s full name and that he was the company’s CEO
- They knew that we use this supplier and are familiar with the name
- They didn’t probe further when asked if there was anyone else at the company they regularly spoke to
While the information in point one is widely available – on LinkedIn and the company website – it serves as a reminder that scammers will use personal details to make their attacks more targeted and realistic. Had Faye asked to speak to “the CEO”, I would have delved much deeper into what the purpose of the call was. But since she was on first-name terms and was purportedly calling from a known supplier I was more inclined to trust her.
The second point is alarming because it’s narrowly accurate. Since the supplier is well known and works with many companies, this may have simply been a fluke. Alternatively, this may be an emerging worst-case scenario. It’s possible that the supplier has at some point suffered a data-breach and had client information leaked. This would explain how they knew we worked with that supplier and may have been the source of Rob’s details as well.
As it turns out, a few days preceding the call from Faye, the supplier had suffered a data breach. This breach included client’s names, job titles, and partial payment information including cardholder name and card type. This makes it hard to doubt the two events are unrelated.
The third and final point is the most alarming whilst also being seemingly insignificant. When Faye called, she wanted to speak with Rob and was clear that no one else could help when told he was unavailable. This indicates that the scam wasn’t just a scattergun approach but targeted at Rob specifically. Considering that cardholder name was part of the data leaked in the breach mentioned previously, this may be why.
How do vishing scams work?
Based on the articles covering the breach, the information given during the call and other attempts we’ve seen before, the scam would have likely gone like this:
The supplier’s data is breached and acquired by cyber-criminals. This may be sold on a dark-web marketplace to the scammer or the scammer might have been the one to directly take the data.
The scammer creates a fake email pretending to be from the supplier and sends it to the target company stating they need to resubmit card details due to ‘an issue’. This email may include a website link or telephone number to ‘update’ the card details – both of which will be fake.
(I should note that we never actually discovered an email. It’s possible that it was blocked by our email security system due to coming from a known malicious address or linking to a known malicious URL. Alternatively, the email may be entirely fabricated and only used to imply there’s ongoing communication and build trust in the call.)
The scammer now calls the organisation and requests to speak to the target regarding the email about card information. Once they reach the intended target they would likely say that there’s an issue with billing and until the card details are resubmitted, all orders will be frozen and no additional payments can be made.
If the target is worried by this and not suspicious of the request, they will likely be happy to hand over their card details to resolve the issue. The scammer would then check the details are real and maybe say something like “Excellent, I can see the payments are going through now.”, before hanging up.
How can you protect your business from vishing?
Undertake user training
You’ve probably heard this reiterated a hundred times before, but one thing often left unmentioned is that you must ensure your training program is grounded in the scope of the business.
The more abstract training is from employee’s day to day roles, the less engaged they will be and the less they’ll remember. A simulated vishing call against employees whilst in the workplace is not only realistic but will likely leave a lasting impression – making it incredibly valuable.
Don’t rely too heavily on caller ID
Caller ID allows you to put a name to a phone number and identify who’s calling. This sounds like a useful tool in preventing scammers masquerading as someone they’re not. But caller ID can be easily spoofed to show what the scammer wants to show.
There are many online services which offer caller ID spoofing – making it easy for scammers to take advantage of the trust a caller ID can give. This doesn’t mean caller ID is completely useless though as it can be helpful in filtering out nuisance calls, but you should not blindly trust the system.
Don’t respond to requests for details
It’s easy to say this, but if it were easy to do, vishing wouldn’t exist. To keep your details secure, you must get yourself and your employees into the mindset that unless the request is coming from an official channel which the caller can prove is genuine, don’t divulge company details.
Establishing and enforcing acceptable channels of communication for clients can make this much simpler. If you establish in company policy that certain details may never be communicated via certain channels (i.e. never disclose a mobile number over email), it’ll be far easier to stop scammers who are trying to siphon information out of the business.
Take the time to check
If there’s a suspicious call about an urgent bank transfer or new card details, get approval on whether it’s genuine off the phone and ideally face-to-face with who usually deals with the issue (e.g. the finance director). If the caller is genuine, they won’t mind you taking the time to check and if they aren’t, checking is a good way to avoid a disaster.
It’s worth building this approval process into policies so that people know who to go to for each request. Having the process in company policy also shows that asking about the authenticity of a suspicious request isn’t something for employees to be worried about doing.
Employ zero-trust
This policy sounds severe, but zero-trust simply means employees who don’t need to know something, aren’t told it. If you store credit card details in a secure digital wallet which everyone has access to, it only takes one successful vishing call for those details to be compromised.
If only the finance department has access to those details though, it’s much harder for a scammer to get lucky off an unaware employee who was trying to be helpful.
Establish and communicate a list of acceptable requesters
Like with establishing acceptable channels, you should ideally have a list of names for which it is acceptable to give details to. If you’re employing zero-trust, this list only needs to be known amongst those who have access to the details; otherwise, you’ll need to communicate it to the entire company.
… To summarise
Before this experience with vishing, I had only experienced it once before and it had been a rather poor attempt (a very robotic voice asking about the ‘accident’ I had been involved in). I had been fairly certain that this was the way vishing would stay – easy to spot, scattergun and done by text-to-speech. But this latest call has unfortunately proved me wrong.
Not only was it done by an actual real human, but it was pointed at a very specific individual. This is a trend which mirrors the evolution of other cyber-attacks and the increased weight cyber-criminals are placing on social engineering in their toolset. Whilst this threat is old and not uncommon in high-end security breaches, it seems it’s now also coming to the masses.
If you’re uncertain about whether phishing, vishing or any other type of cyber-crime is happening on the scope and scale it’s reported at, I hope this experience opens your eyes to the reality of what’s happening. It certainly did for me.
We receive around 121 emails a day, on average, so it’s a wonder how we manage to keep up the constant communication!
Email can quickly become a drain on time if not managed correctly. The average worker now spends 28% of their time managing email. This means if you work Monday-Friday, 9am-5pm, over one whole workday is dedicated to your inbox.
There are many suggestions out there on how we can better manage our inbox and email communications, but some of them aren’t that practical for the majority of people to use.
Luckily by using a few of the inbuilt tools in your inbox and some time management skills, you can organise your email inbox, read and process incoming mail more effectively and become more productive.
1. Unsubscribe, unsubscribe, unsubscribe
Set aside time to blitz your inbox and unsubscribe from any irrelevant newsletters and communications. Fear of missing out (FOMO) on the latest news can make us reluctant to hit unsubscribe but think how often you actually read those emails? There’s a chance that you open many of them to mark as “read” because they don’t deliver any real value.
Of course, if there’s a weekly newsletter you love seeing in your inbox and enjoy reading as soon as it arrives then keep on subscribing, but if you keep receiving weekly “offers” from that stationery supply company you placed an order with once, then hit unsubscribe. Don’t forget there’s nothing to stop you from re-subscribing if you find yourself missing a newsletter.
2. Make use of rules and folders
Quickly scan your emails and create a list of “big” categories. Depending on which department you are in you may have categories like Vendors, Customer Service, Receipts, Recruitment etc. If you want you can also create subfolders within each category to further divide your emails, but don’t worry about being too specific. You just want recognisable categories which make it easier to manage your inbox.
Don’t forget you can use Microsoft Outlook’s search function if you need to find a particular email, so there’s no need to create sub-folders by sender name, date, subject etc.
Another feature you might want to take advantage of is “Rules”, which automatically file messages away into their correct folders as they arrive. You can choose whether you want these messages to be displayed in the New Alert window (ideal for high priority messages) or to play a selected sound.
There’s also a whole host of Advanced Options to choose from such as mark as important, mark as read, delete or send an automatic reply so you can ensure you prioritise important communications.
3. Don’t check email so often
Checking email has become synonymous with work, but often it just distracts us from more important tasks. How often have you been in the middle of something only to be distracted by an email notification?
We immediately feel the need to check our inbox but it’s rarely urgent, and then it’s difficult to get refocused. Even if each new email only distracts you for 30 seconds, if you receive 100 emails a day that’s 50 minutes you’ve wasted on checking your inbox.
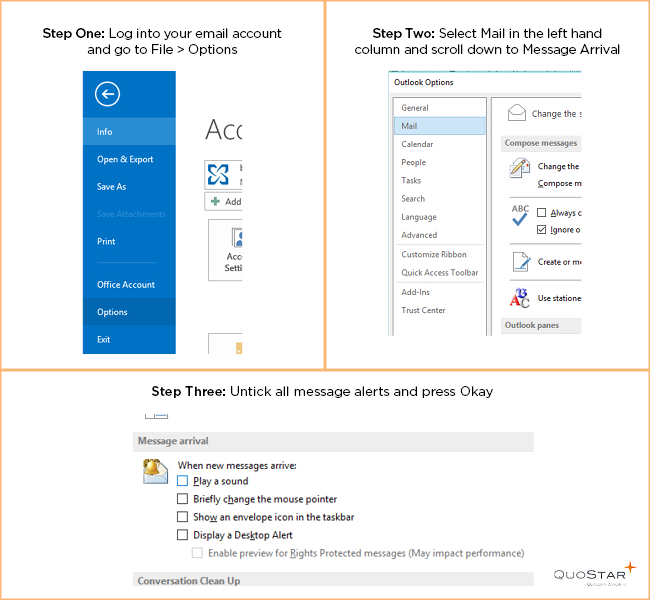
Luckily there’s an easy way to prevent emails from distracting – simply turn off your audio and visual notifications. Log into your email account and go to File > Options > Select Mail in the left-hand column > Scroll down to Message Arrival > Untick all the message alerts.
Worried about missing a specific email? You can set up a “Rule” that will override this setting. For example, you could choose to have any emails from your manager to play a selected sound.
If you’re getting distracted by the thought of new emails then try setting aside specific periods to check your inbox. You could check once when you first arrive at the office, once around lunchtime and once in the afternoon.
If checking three times a day doesn’t work for you then try once per hour. For example, 45 minutes of focused work and 15 minutes of email management. Chances are you’ll find it easier to focus if you have regular, allotted breaks.
4. Try to get to inbox zero every day
There’s nothing worse than logging in and finding your inbox overflowing with hundreds of messages. It can be tempting to just select all and hit delete but you never know what you might miss.
Instead of allowing emails to build up, try to set aside some time at the end of each day to review your inbox. Reply to important communications, file away emails in the relevant folders and unsubscribe to anything irrelevant as you go.
Tackling your email in a more strategic fashion should make it more manageable. Of course, you will get some emails overnight, but in the morning you’ll have significantly fewer unread ones than normal.
5. Try email archiving
Many people will recommend sorting emails into “keep” and “delete” and trashing any which are no longer relevant. Or declare “email bankruptcy”. While this suggestion would probably work for your personal inbox it can be a bit more tricky in a business situation. Emails are important records of business decisions and if your company were to become involved in legal proceedings you may be required to present all related email conversations dating back to as far as six years.
With a cloud-based email archiving solution you have long-term, ultra-secure and forensically compliant storage for your emails without clogging up your inbox. Emails are automatically archived and remain so even if deleted from your inbox. Every email will have a digital fingerprint and time stamp to ensure authenticity. You can even restore emails direct to your inbox if required.
Email is a necessary part of a business, but it doesn’t have to be a necessary evil. With a few simple tricks, you can prevent email from draining all your time and focus on your business instead. Don’t forget to encourage employees to pick up the phone, or speak to you in person, for urgent matters. Not everything needs to be done over email.
Every day hundreds of thousands of scam emails flow into the inboxes of users all across the world. While it’s painfully obvious that some are completely fraudulent, phishing emails – particularly those targeted at businesses – are becoming much more sophisticated, and increasing numbers of users are being tricked into sharing valuable company information.
Unfortunately, there is no one red flag which immediately identifies a scam email, but there are a number of things to watch out for.
How to spot a scam email
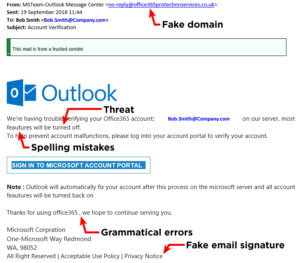
1. Don’t trust the displayed name in the email
A name displayed in the “from” box in Outlook is not a guarantee of the sender
2. Look but don’t click
If you hover your mouse over a link (without clicking) you will see the web address that the link points. If it doesn’t directly reflect that of the sender then be cautious. Also be extra vigilant if any email directs you to a website asking for a login, as this is the main way a criminal will steal valid login credentials.
3. Check for spelling or grammar mistakes
If the email doesn’t sound right when reading it then that’s a flag that it’s not legitimate
4. Look at the salutation
If your contact usually addresses you by your first name, but now they’re writing “Valued Customer”, you should look deeper. Again, any suspicion you have is probably being triggered correctly – trust your instincts.
5. Never give sensitive information
If an email is asking for sensitive information over email or a web page that you wouldn’t be comfortable with anyone else seeing then pick up the phone to a known number and validate it.
6. Beware of “urgency”
If an email sounds urgent and startling then do take some time to think, analyse or ask advice. If someone is threatening to stop a service or is making a demand then you should stop, think about it, and talk to your colleagues.
7. The images and layout in an email tell the truth
It’s common for cyber-criminals to not quite get the look of emails right, in terms of images and layout. You alarm bells should ring if the email doesn’t look quite right. If in doubt, pick up the phone.
8. Check the domain
Many spoof emails use a domain that is close to the legitimate domain. For example, someone could use paypall.com rather than paypal.com to fool a recipient.
9. Be wary of attachments
Attachments in emails can be dangerous if the file type isn’t a standard application file, such as a .doc (word file), xls. (Excel file) or pdf. (PDF file). Be especially wary if the attachment is one of the following file types – “exe”, “bat”, “com”, “cmd”, “cpl”, “js”, “jse”, “msi”, “msp”, “mst”, “paf”, “wsh”, “wsf”, “vbs”, “vbe”, “psc1”, “scr”, “lnk”. Also be extra careful with zip files as they can often hide dangerous files from inferior email scanners and firewalls.
Example of a scam email
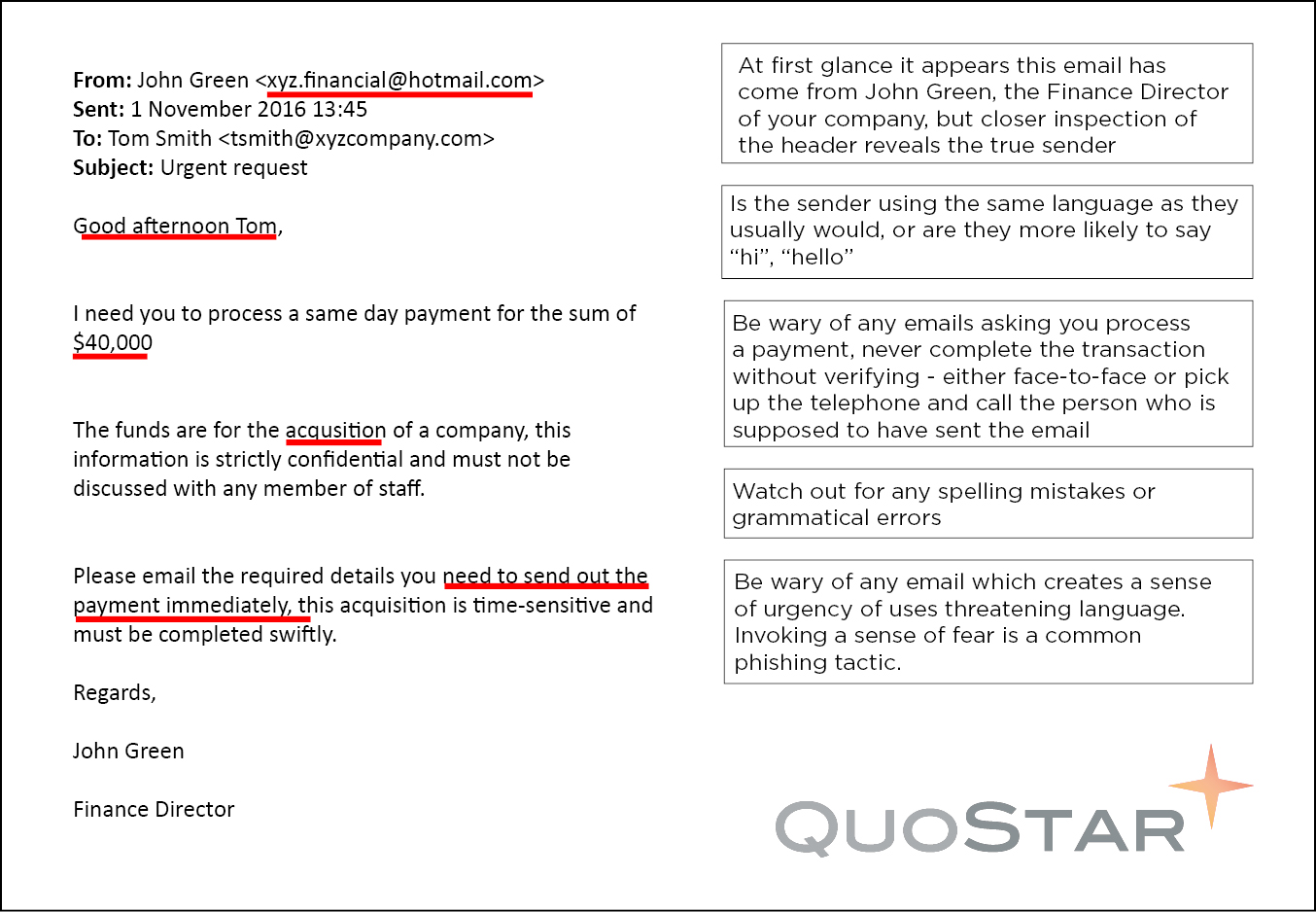
At the end of the day, if an email doesn’t seem quite right then make sure to qualify with the supposed original sender. If your Finance Director asks you to arrange a bank transfer, confirm the request on the phone or in person. It only takes a few minutes and could prevent you from making a costly mistake.
Email archiving brings benefits to every department throughout a business – from finance and legal, through to administration. One department which can benefit from email archiving is HR, as they deal with personal data every day.
Three benefits of email archiving for HR Managers
1. Investigate claims of bullying in the workplace
You may think this doesn’t happen in your workplace, but it’s something you should be able to investigate. Research carried out by the TUC shows that 29% of people have been bullied at work. Email records are important in cases of alleged verbal or physical bullying, as they’re difficult to prove.
An email archiving solution that captures every email provides HR managers with the transparency and visibility required to conduct a fair investigation in the event of a complaint. It’s more reliable than relying on employees to archive their messages on an ad-hoc basis. A solution with user-based security permissions is ideal as HR Managers can investigate complaints without the involvement of the IT department.
2. Monitor for email misuse
A company may find itself in the midst of a legal dispute if employees misuse corporate email. This could range from sharing offensive material to accidentally hitting the “Reply All” button. It is not enough to rely on your employees to use common sense when it comes to email etiquette, and it could result in legal action against your company – as seen in the case of Thales Australia.
One way to ensure employees are aware of your business’s email usage policy is to send a copy of the guidelines via email. Then ask employees to send a reply stating they have read the policy and agree to abide by it. Your email archive will save the reply, so you have a record available should any dispute arise. Using an email archiving solution means you will also have a record of any inappropriate work emails, even if the employees sending and/or receiving them delete the messages from their inbox in between system backups. Emails are time-stamped and digitally fingerprinted at the moment of storage and retrieval so you can guarantee accurate data. Which is essential if these emails are being presented as evidence in a tribunal.
3. Ensure regulatory compliance
You must keep former employees’ records for the duration of employment and for six years after you terminate employment. This includes items like training records, appraisals, contracts, annual leave, sickness records and disciplinary warnings (even if these have since expired). You have to keep these because an Employment Tribunal, County Court or High Court claim is possible for up to six years after employment ends. So the business could be at risk for failing to produce these records. Also keep anything that relates to the employee, which an Employment Tribunal may require as evidence, for this retention period.
Corporate emails are important records of business decisions, communications and information; and, just like paper documents, you must secure and store them properly. This is where an email archiving solution can assist, but many companies may believe they already store records correctly – by backing up their mailboxes on a regular basis.
There is often confusion between email archiving and email backup, with some believing they perform the same – or very similar functions. In reality, they are different solutions, which businesses should both use.
What is Email Backup?
In simple terms, a backup is designed as a short-term insurance policy to facilitate disaster recovery. A classic backup application takes images of active data periodically in order to provide a method of recovering records that have been deleted or destroyed.
Backups are usually only retained for a short period – a few days or weeks – as more recent backup images replace previous versions. It is important to understand that emails can be deleted in between backups and would thus not be retained. Data is usually kept in a proprietary format which can cause problems for long-term retention.
What is Email Archiving?
In contrast, email archiving is designed to provide businesses with an ultra-secure repository for email records that need to be stored for a long period of time. This may be necessary in order to meet certain regulatory obligations. Email archiving provides businesses with a full record of communications, and additional security features like time-stamping and digital fingerprinting ensure that the email has not been tampered with or edited in any way – essential when providing emails as evidence to courts.
It is also far easier to find and retrieve records from an archiving solution compared to a backup. Emails may be requested by an external auditor or can be the result of an internal investigation. Instead of asking your IT department to dig through volumes of saved data snapshots and format it to comply with the request, they can use the search facilities to locate the necessary records in their original and exact format.
Which solution should you choose?
In the short run, it may seem less expensive to back up your email data to a tape or local server. However, the volume of email data increases every day which results in greater storage requirements. In the long run, the cost of storing and protecting that data can far exceed the cost of implementing archiving.
However, this is not to say that an archiving solution should replace your backups. Both solutions fulfil important functions and should be used in tandem. It’s important to remember that it’s a legal obligation to provide copies of emails if asked by authorities or regulators. This is something that virtually all backup solutions cannot do. In order to choose the most effective and suitable solutions, companies should first distinguish between their backup and archiving needs. Then explore the appropriate storage solutions to meet these needs.
Email retention policies are all about decreasing the risk to your company. But for a truly successful policy, you need to strike the balance between a retention period which is too long and keeps useless mail around and one which is too short and loses mail that was important.
Your policy needs to take into account any applicable legal or industry regulations whilst not going overboard trying to store every email indefinitely. If your company does not yet have an email retention policy then it’s certainly worth drafting one, and here are five best tips to get you started.
How do I create an email retention policy?
1. Start with the regulatory minimums
Every business will be subject to different regulations, so the first thing you should do when creating your policy is to review the regulations your company is subject to and the relevant document retention requirements involved in each one. Some regulatory bodies you may need to consider include:
- The Data Retention Regulations 2009
- Freedom of Information Act
- Financial Services Act
- Sarbanes-Oxley Act (for US-related firms)
- The Data Protection Act 1998
If the retention period is unknown then six years is often the common safe denominator. This is because it’s possible to bring a “breach of contract” up to six years later. If your business is concerned about particular records then you should seek legal advice.
2. Segment your data by type of use
Once you have the regulatory minimums you will notice that the recommended periods vary widely. With this in mind, you may wish to segment emails by type, use or department to prevent having to store all content for the maximum retention period.
For specific documents like PAYE records, maternity pay or statutory pay it is up to employers to assess retention periods based on business needs. If an employment tribunal may require the document as evidence then a retention period of six years makes sense. If the document could be needed for HMRC reviews, then a minimum retention period of three years after the end of the tax year in which the payments were made would be necessary.
3. Draft a real policy
Creating a policy, and getting it approved by senior management and legal professionals, will give you the ability and authority to implement all the IT, security and process controls you need to enforces your email retention requirements. Your policy should include the following sections
- Purpose of the policy
- Retention time, including any segments you are using to define the retention periods. Durations are often listed as years or may be permanent
- Difference between paper and electronic documents – although ideally there should be none
- What constitutes destruction (e.g. shredding, deleting, overwriting, degaussing of media
You do not have to include specific technologies and processes, but it is a good idea to refer to capabilities and requirements (e.g. offsite archival). You should also omit areas you will not or can not support, such as the types of segmentation you are unable to determine or support. If you haven’t seen a full retention policy before there are plenty of examples online for you to reference.
4. Review the preferred solutions
Once you have the main points of your policy established, you can estimate your minimum requirements for a solution based on the number of users, the expected volume of email and the expected rate of growth. With this information, you may be able to loosely price out a solution, but you may also wish to obtain indicative quotes from suppliers. You should also prepare for any changes to the email retention policy which may affect your pricing e.g. the minimum retention period increases from 18 months to three years.
5. Involve legal in the policy process
If it is the IT department’s responsibility to draft the email retention policy, then it is important to involve legal. Whether that’s an internal legal team or an external law firm. The main reason for this is so they can review the viability of the policy and if it will meet your regulatory obligations.
Allowing legal to view the policy at this stage means you can present a unified front to the board. It also allows you to evaluate the options you have laid out, and remove any of the amendments legal have made that will drastically increase the price.
To conclude…
Given the number of different regulatory bodies and how they affect organisations, every business is likely to have an individual email retention policy. Following these best practice tips will help you to create a policy that is effective, sensible and which you can enforce.
Cloud email archiving is the process of storing a log of all email communications on a cloud storage platform. This enables businesses to have a secure, long term way to store emails for either legal, regulatory or documentation reasons. The main benefits of a cloud email archiving solution are that it reduces the costs of storage hardware and that it enables access to the emails from almost anywhere.
The IDC says 60% of business-critical information is stored – sometimes exclusively – in email communications. This highlights the need for a solution that allows businesses to quickly and securely search, store and retrieve this information. Enter cloud email archiving.
By removing the need to purchase and install any additional hardware or software, cloud email archiving offers a way to lower the TCO (Total Cost Ownership) and lower storage requirements without a significant compromise in security or performance. The flexibility of the cloud also means businesses can scale their solution up and down as their needs change, so you only need to pay for what you actually use.
Cloud Email Archiving Diagram
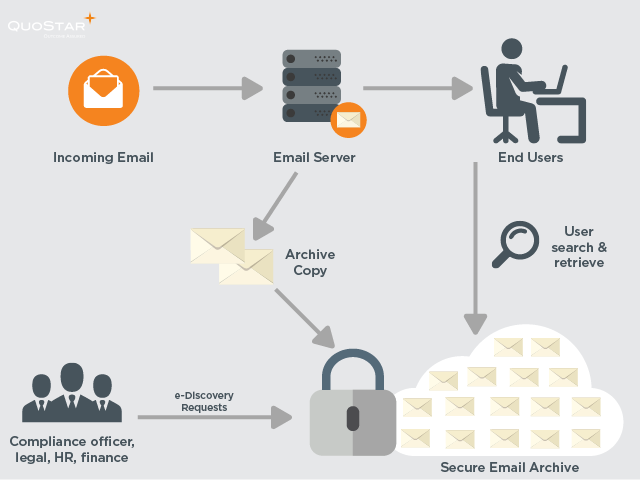
What are the risks of cloud email archiving?
One of the main concerns decision-makers have about implementing cloud services is the security of their data. Many decision-makers fear that the service provider may access their sensitive corporate data. Or that someone may intercept the data on its journey between the customer and the data centre where it lives.
In reality, cloud email archiving solutions are as robust, if not more so, than in-house archiving deployments. Several layers of security measures are used to protect customer information. For example, QuoStar Mail Archive comes with business continuity and disaster recovery built-in as standard so you never have to be without email, even if you lose your email server. Our ISO 20000 and ISO 27001 certifications also ensure the best security and a continually improving service.
To conclude
Cloud email archiving is a suitable solution for businesses of all sizes, types and complexities. It offers many benefits, including financial, security and flexibility. Plus it also provides businesses with access to massive storage capabilities.
Businesses can now easily store large amounts of data – in accordance with their corporate policies and regulatory obligations – without the usual cost and difficulties associated with doing so. With the right email archiving solution businesses can ensure their corporate data is secure and easy to search and retrieve.
There are typically three ways in which businesses can archive their email; save absolutely everything, rely on users to archive emails or utilise an email archiving solution.
With 269,000,000,000 (yes, that’s billion!) emails being sent and received every day, storing every single one is not really feasible. And with 200 billion of those being SPAM, storing each one is unnecessary, only serving to increase the cost and length of the e-discovery processes.
Neither is it reliable to depend on users to archive their own emails. If they forget or were unaware what they needed to archive, your business has to pay the price if the email is needed for litigation or audit purposes. An email archiving solution, on the other hand, automatically archives, stores and preserves emails for you.
How can your business benefit from email archiving?
1. Reduced storage requirements
Archiving solutions typically use two different techniques to reduce the amount of storage required, neither of which will affect end-users. Advanced compression technologies compress each email and its attachments before archiving, saving 50% or more in overall storage requirements. De-duplication, also known as single instance storage, ensures that the archiving solution only stores one copy of each message or attachment.
2. Prevents users from losing data
Users can easily delete important emails, accidentally or maliciously, and the majority often delete emails between backups, and at times the entire inbox upon leaving the company, which means your business is at risk of losing important data. An email archiving solution can eliminate these risks, by automatically storing and preserving all emails.

3. Increased server performance
Moving emails out of a live environment will help to greatly improve the performance of your email server. Emails can be deleted from the mail server, according to rules-based processes, once they have been archived and stored.
4. Simplified backup and restore
Reducing the email server’s data load allows it to be backed up faster and more simply. Users can also restore emails from the archive to their inbox with a single click, freeing up your IT engineers from having to go through the time-consuming process of recovering them from a backup.
5. Eliminates mailbox quotas
An email archiving solution removes the need to use mailbox quotas as a way to limit the use of a mail server’s storage capacity.
6. Accelerates search capabilities
Most archiving solutions will provide a basic search and retrieval function for data that has been stored and retained. Some solutions will go further and allow users to search by email address, to/from address, attachment name, words within documents, plus more, drastically cutting down the time it takes to locate an email.
7. Accounts for all users
With an archiving solution, you don’t have to rely on users adhering to email retention guidelines. All emails will be automatically stored, archived and preserved.
8. Eliminates PST files
Individual PST files are prone to data corruption or loss, have a huge impact on storage and can be difficult to search through, due to their size and number. With an email archiving solution you can import all historical PST files into the solution, which you can then search with ease.
9. Helps ensure compliance
Many sectors have specific rules and regulations regarding data retention, and an email archiving solutions help ensure you remain compliant. All business must be able to pull back emails on demand for the purpose of litigation or auditing.
10. Lowers costs
Email archiving solutions will typically work effectively on cheap storage, whereas most email server systems require faster, more expensive disks and technologies. The majority of companies will see their data usage grow every year, which will equate to increased storage costs and increased storage management costs.
11. Removes human error
User-driven retention relies on users managing retention with predetermined tags and rules, for specified time periods. This method of retention is prone to user error because you rely on users to consistently adhere to and follow the guidelines. Even with constant policing, it would be easy for a user to “forget” the guidelines, or intentionally ignore them.
12. Typically tamper-proof
While users can search and retrieve emails from the archive, most solutions are tamper-proof – an essential feature for compliance. Not even the IT department will be able to alter or remove emails from the archive. The solution should also have a tamper-proof log which records who reads what in the archive and when they read it. All emails should also be digitally signed to allow them to be used as evidence in a court of law.
There are many types and forms of email archiving solutions available. Some will go beyond the benefits listed here but others may not be as effective. It’s important to carefully research available solutions, both internal or cloud-based, so you can find the right one.
An email archiving solution is critical for your business, and not just so you can comply with regulations. A huge amount of business-critical information is on the IT systems. Some of it may exist solely in email so it’s vital that you don’t lose this.