Our Head of Security, and CISO Service lead, David is recognised as one of the Top 10 influencers by Thompson Reuters, and a Top 50 global expert by Kingston Technology. He is also one of the Top 30 most influential thought-leaders and thinkers on social media in risk management, compliance, and regtech in the UK.
In his role as Head of Security at QuoStar, David leads the CISO Service. The CISO service provides businesses with the cyber-security skills and experience necessary to manage the multitude of threats and rapidly changing risk landscape of today, on a flexible and cost-efficient basis. David take’s a moment to share his views on it all.
1.How did you get started in the security field and ultimately become a CISO?
David: I was around when some of the first Viruses went mainstream. Back then I worked for one of the only companies that made Multi Factor Authentication systems in the 90’s. It was “leading edge” at the time.
I built and ran one of the largest commercial remote access platforms using Multi Factor Authentication. Then I ran Infosec for some FTSE 100 companies, one of which was the largest private trading network in the world – trading 3.5 trillion dollars a day. Another was managing Global Security Services Operations Centres (24/7) across 4 continents, where most of the customers were FTSE 250.
2. What do you enjoy most about working as a CISO Service resource/consultant?
David: Meeting challenges of audit, due diligence, and breach management.
Audit is getting more involved and complex and due diligence is often 300-400 questions and an “interview” with the compliance department of potential customers.
Breaches is about managing with around 10% knowledge of the situation and making decisions in a very short time for the best outcomes – while ensuring buy in from the board. They always seem to happen on Friday evening!
3. As Head of Security, what challenges or issues do you regularly see in small and mid-market businesses? Why do you think the same issues keep occurring?
David: 1. Robust management of access and privilege management. 2. Managing risk consistently. 3. Not aligning Cyber Security with Data protection requirements – as they overlap at a core level.
If you have control of the information assets servers and cloud, information security is much easier to manage. It enables savings in resource and effort if this happens and can demonstrate to the business control and improvement.
4. How do you think the security landscape has changed in the last five to ten years?
David: As a CISO Service lead, I believe it is manging the hybrid of internal servers and cloud – and managing the challenge of access control. The company boundary is very fluid, especially where ‘what’s company and what’s personal’ is concerned.
One of the best frameworks is ISO27001. It is good for demonstrating accountability and decision making. It also aligns with SOC2 and parts of HIPAA quite well.
5. What do you think will be the emerging risks businesses need to consider in the next 1-2 years?
David: It used to be technology first, then followed by making technology safe and compliant. Now technology needs to be safe and compliant first, and performance orientated second – along the lines of what has happened in the automotive, aerospace, building and food industries.
The risks potentially surround the technology itself not having enough security management capability, or that if it does it can be resource intensive. There’s also the globalisation of threat actors and the capability of managing multiple global data protection regulations.
More recently the US Biden government issued a memo to US Businesses in summary June 2, Stating the 5 best practices – one being Multi Factor Authentication. Other important aspects are multi-pronged backup Updates, Incident Response, external testing and network segmentation.
6. Has the Covid pandemic exacerbated security concerns or introduced new ones for businesses to deal with?
David: Probably, due to homeworking and fast transformations of moving office servers to the cloud, as well as an increase in Ransomware attacks, an increase in Data Protection legislation globally and the increase in corporate security concerns due diligence.
It has been an increasing challenge for a Head of Security. We have seen an increase in demand from due diligence enquiries, especially for more detailed homeworking policies and guidelines. So, the lines have blurred as to what is home device or a work device. The “physical office” is now the home office, and mandating rules now have to be guidelines that are appropriate – as well as using more layers of defence to protect staff and corporate assets.
7. Do you think businesses focus too much on the technical/technology element of security (e.g. AI solutions)? What other areas do they need to consider?
David: Potentially yes, without an end-to-end strategy, it makes security technology “tactics” unlikely to see a ROI, Return on Investment.
As Head of Security, I see the human element of security is also overlooked quite often. Especially when you consider that almost half of all security breaches are caused by human error. This is even more disconcerting when you consider that only 60% of employees will report a security breach too.
We are actually hosting a free webinar on that subject on 29th July 2021 at 1pm, so if you’d like to know more register for free.
8. How important is cyber-security education? What are the challenges for a Head of Security conveying the risk/educating business? Who in the business needs to receive education/training and how often?
Education is very important, as is having the appropriate training for each role ideally aligned to the companies risks – so that maximum benefits can be realised e.g. developers would require different training from HR staff, as the risk they are managing are different.
Of course, there will always be a need for baseline cyber and data protection training. You can find out more about what Security Awareness Training there is available for employers and employees in our article here.
9. Do you feel there is a security skills/talent shortage? What advice would you give to businesses to combat this?
David: I’m not entirely sure. If there is a shortage, there is definitely a misunderstanding of what skills are required.
Personally, I would align the risks and the strategy, then decide what skills are required to make it happen. It may be that companies would benefit from outside help – to formulate the strategy, and always have access to a range of skill levels onboard to achieve skills resilience.
The other issues that many companies seem to come up against are 24/7 and global, so having just one capable Security resource will not be enough to cover these time periods.
10. As Head of Security, what advice would you give to businesses who want to reduce risk and increase their security posture?
David: Manage Risk regularly with key stakeholders.
Ideally do not remove a risk or lower a risk without evidence, from at least the following e.g. a Policy, Procedure, Penetration test, Internal Audit, External Audit or risk committee approval. This will demonstrate accountability and assist in managing data protection, to enable a defensible position in the security posture.
Ensure a multi-layer approach to security. Utilise things like Access control, least privilege, Approved applications, strong email defences, layered endpoint security, centralised control of endpoints and access, plus multiple point backups.
11. If there was one security investment you could recommend to businesses what would it be and why?
David:
One piece of tech most companies aren’t using
To keep companies ahead, Secure Access Service Edge will help with Cyber security and Data Protection. The ROI is great! It releases staff time, and the payback can be in months.
One Framework
You can manage risk and accountability using ISO27001 framework. If you are not going to be certified, ISO27001 also helps align with NIST, SOC-2 and can help align some components of Data protection. It can clearly demonstrate accountability.
Training that is focused to the role in the business is most appropriate, using the “Incident” metrics to tailor training and technology requirements.
One practice
Have a data/Cyber champion in every business function so you’re able to manage threats, risk and increase incident reporting capability to enable “real-time” issue management.
We hope you found David’s current take on Cyber-Security insightful. During his career David has worked across multiple sectors, including financial services, government, utilities and FinTech, working with a variety of clients – from start-up level and SME up to FTSE 100. He previously held the role of Global Head of IT Security at BT and Radianz (formally Reuters). He’s also been responsible for managing the security infrastructure and delivery of ISO 27001 for multi-billion/trillion-dollar environments. He is also an active CISO consultant on our CISO service offering.
What are the essential cyber-security measures every business needs?
In today’s digital era, advancements in technology are happening very rapidly. Therefore our defence systems against very real cyber-security threats must keep pace. If the correct measures aren’t taken, your business might be more at risk than you think. Here are 9 essential cyber-security measures your business can take.
Are you relying on the same security basics you were a few years ago?
It’s easy for time to pass unnoticed while all these advancements happen around us. Before you know it, you’re relying on the same old security basics to protect your business as you were a few years ago – firewalls, antivirus and intrusion detection software. Most people update their mobile phone software more frequently than that. So here are our 9 recommendations on how to keep your company more secure.
Why is it so important?
The truth is, we all feel impervious to cyber-crime and security breaches. It’s just something that happens to other people – until one day it’s not. Even if a direct financial attack is not a concern for a business because that’s locked down, many people are unaware of the intrinsic value of the data their business holds in today’s world.
Hackers aren’t just after your bank accounts.
Cyber-crime is now an industry that produces over £1 trillion in revenue for cyber-criminals. Ransomware can be used to encrypt a company’s files and hold them for ransom. Network penetration can enable mass data theft and crypto-jacking to harvest crypto-currencies by stealing your machine’s processing power. Money can even be gained by using social engineering to persuade employees to transfer cash to a fake bank account.
9 steps to combatting cyber-threats
- A Unified Threat Management (UTM) system
A UTM system is a combination of security appliances and acts as your gateway to the internet. - A SPAM filter
A Spam Filter tops potentially malicious files from entering your network via email. - Antivirus/anti-malware software
Antivirus and Anti-malware are applications that protect your servers, laptops and other devices from malware. - A patch management system
A Patch Management System manages the installation of software updates to close security holes. - 2-Factor authentication
2-Factor Authentication gives you a second level of security, preventing unauthorised sign-ins. - Device encryption
Device Encryption makes any data stored on the machine useless to criminals and keeps your data secret. - A regular data backup
Regular data backups. You should keep a copy of your business data at a secure off-site location in case the original is lost. - Content filtering
Content filtering prevents access to dangerous or illegal websites which reduces the risk of infection. - A disaster recovery plan
A Disaster Recovery Plan sets out how you will recover from an unplanned event such as a fire or cyber-attack.
Regulatory fines and costly lawsuits sting victims of cyber-crime too.
Keeping businesses cyber-secure is even more important since the implementation of the General Data Protection Regulation (GDPR – tailored by the Data Protection Act 2018). Businesses are responsible for their data leaks or breaches if the correct security protections/protocols have not been put in place. Hefty regulatory fines can be levied, and costly lawsuits can follow for the victims of a cyber-attack or security breach.
All businesses should ideally be looking into taking more than just the bare minimum steps to keeping the company cyber-secure, but it’s at least these 9 steps that start the journey in the right direction. The next step beyond the basics is to become Cyber Essential certified.
Cyber Essentials is a Government-backed Accreditation
Cyber Essentials is a government-backed accreditation that acts as a way to understand where your security succeeds and where it needs improvement. It’s similar to a cyber-security audit and allows you to see what your next steps in improving security will be.
Cyber Essentials still covers fairly basic security concepts, such as having the ability to remotely wipe devices, application whitelisting, daily virus scans and the disabling of OS utilities. All of which are simple things that you should already have in place. But it’s well worth going through the accreditation process if you haven’t already – it can improve your company’s image as well as open you up to working with more cyber-conscious clients.
While WhatsApp is a consumer-grade application, many people are using it for business purposes. It’s free and it’s easy to use – most people are probably already using it – so it seems like the ideal communication tool, particularly now many employees are working remotely.
But is WhatsApp really suitable for business communication?
Privacy Policy Updates
WhatsApp was acquired by Facebook in 2014. At the time, CEO Jan Koum stressed how deeply he valued the ‘principle of private communication’. However, just two years later, in 2016, both apps announced they would be ‘coordinating more’– but did give users the option to opt-out of sharing their personal data with Facebook.
This time around, there is no opt-out.
Users who want to continue using WhatsApp after May 15th 2021, have to agree to the updates made to its terms and privacy policy. This means being prepared to share their personal information such as names, profile pictures, status updates, phone numbers, contacts lists, and IP addresses, as well as data about their mobile device, with Facebook and its wider companies. Users who don’t accept the new terms will be blocked from using the app. The new policy, which applies to all users outside of Facebook’s European Region (including the UK), also means that simply deleting the app from the device will not prevent WhatsApp from retaining a users’ private data.
Since the privacy policy changes were announced, WhatsApp has now said that it will not be sharing personal data from people who previously opted out of sharing their information with Facebook. According to The Register, this setting will be apparently be honoured going forward next month, even if you agree to the new policy. For all other users though, there is no opt-out.
A WhatsApp spokesperson also said this update ‘primarily centres around sending messages to businesses to get answers and support’, claiming there will be no change in data-sharing for non-business chats and account information. However, there has been much criticism and concern about the update online.
Update: 12th May 2021
Originally, WhatsApp planned to roll out its privacy policy update on February 8th 2021. However, due to huge public backlash and confusion, they opted to delay until mid-May. Through a series of updates, WhatsApp attempted to clarify its position, reiterating that the update is mainly meant for businesses using its messaging platform. But nonetheless, WhatsApp stated that the change would not impact “how people communicate with friends or family” on the platform. The company also specified in a blog post that it would continue to provide end-to-end encryption for private messages, and it didn’t keep logs of its users’ messaging and calling.
However, despite the clarification around data sharing, there are still plenty of reasons why businesses should stop using WhatsApp for business-related communication
GDPR Compliance and Liability
WhatsApp makes it abundantly clear that the app is designed for personal use in their Terms of Service.
“Legal And Acceptable Use. You must access and use our Services only for legal, authorized, and acceptable purposes. You will not use (or assist others in using) our Services in ways that: … or (f) involve any non-personal use of our Services unless otherwise authorized by us.”
After installing WhatsApp on your device, you’ll receive a pop-up asking for your permission for the app to access your contact. It requests that you ‘Upload your contacts to WhatsApp’s servers to help you quickly get in touch with your friends and help us provide a better experience”. Agreeing to this means that all your phone contacts are accessible in the app. The problem is, it doesn’t distinguish between personal contacts and business ones. Your contacts haven’t given permission for a third party to access their personal data, which could be a potential breach of GDPR.
WhatsApp has been clear that is for personal use. Users must agree to these terms and conditions before they can access the service and WhatsApp can access the users’ contacts. Therefore, the responsibility for GDPR lies with the user, not the app.
Individuals who use WhatsApp for any business communications are in breach of the terms of service. This limits WhatsApp liability for GDPR because they have given the user all the responsibility for seeking the permission of their contacts.
Security Risks of WhatsApp
Using WhatsApp for business communications is fraught with security risks too. While the app famously boasts security due to its end-to-end encryption, there have been plenty of reported hacks and flaws.
Just last October, security researchers revealed that links to thousands of WhatsApp chats were accessible online. Although there was a quiet change to stop the links from being indexed by Google, the information was still readily available on other search engines. The group’s title, image, description and owner’s phone number were all readily accessible, you didn’t even need to actively join the group.
WhatsApp communications are also notoriously difficult for companies to monitor. It may be possible if they are taking place on a corporate-owned device, but even then, there are multiple hoops to jump through. Companies could require the employee to surrender the device, but to access the content itself, there would need to be an IT policy that states WhatsApp as an acceptable communication channel for business purposes. Although, this policy would be in breach of WhatsApp’s acceptable usage policy. The IT policy should be crystal clear about the firm’s right to access and for what purposes (ensuring these are proportionate), so the employee has no expectation of privacy.
Things get even more complex if the employee owns the device and WhatsApp has been installed outside of a mobile device management (MDM) container installed as part of a BYOD policy. The same policy that applies to the corporate-owned device could be extended to employee-owned ones as well. However, given the device is owned by the employee and used predominantly for personal use, it is doubtful whether a forced surrender and access could be seen a legally proportionate.
If there’s no BYOD policy in place? Access is near impossible. As a personal device, the employee would have much higher expectations of privacy and there would need to be an extremely compelling reason, akin to a criminal offence, for an employer to try and obtain access.
What should you use instead of WhatsApp?
While you could write WhatsApp into your IT policies as an acceptable communication channel for business communications, you would knowingly be in breach of the app’s acceptable usage policy.
Plus, even with that in place, there is still a myriad of security, privacy, monitoring and accessibility concerns linked to the app’s business usages. That’s before you even begin to factor in cultural problems potentially caused by the informal nature of the app. Employees could post personal messages to work chats by mistake, accidentally share their live location, or information could get lost between multiple group chats.
Instead, it’s much better to opt for a business-grade secure communication solution. Many of these solutions function in the same way as consumer-grade apps, giving users a familiar interface so they can get started immediately, but with much stronger security. Solutions are available across multiple devices and will protect your voice, video and text data in transit and at rest, preventing accidental leakage or malicious attack.
In a modern business, communication and collaboration are becoming easier than ever. We can work remotely, we can access documents on our smartphones and check in with our colleagues whilst on the go.
While the increase in this type of working culture is positive. The rise of social media, instant messaging and email – along with the influx of portable devices and removable media into the office space means it’s easier than ever for data to leak out of your business.
Your data – be it financial, client, employees or intellectual property – is a valuable asset. So it’s only right that you protect it.
But with confidential data living on many devices (servers, databases, desktops, laptops, USB drives, mobiles), and moving through many channels, it’s difficult to know where to start. In this article we will outline some of the solutions available to help with the problem of data loss. And look at how you can begin your data leak prevention project.
What is data leak prevention (DLP)?
DLP is a strategy for making sure that sensitive information does not leave the corporate network. It describes any solution or process which identifies and tracks the journey of sensitive data. Or that enforces policies to prevent unauthorised or accidental disclosure.
Many businesses decide to undertake a DLP project to protect their IP or client data. But the task’s complexity and the resources required to complete and maintain it often results in the project never reaching completion.
But with the number of Internet-connected devices skyrocketing and remote or flexible working being so huge since the Covid-19 pandemic, managing and protecting your confidential information is vital. And you will only be able to do this with a DLP strategy in place.
How can a data leak occur?
There are three categories of data leakage:
- In Transit – Data is intercepted whilst travelling, e.g. via email, webchat, web traffic etc.
- At Rest – Data is captured from areas such as file shares, databases, desktops or laptops
- In Use – Data is captured from screenshots, clipboards, printers, USB drives and other removable storage.
As a business, you need to break down each category. Create a list of everywhere you store data and assign them to one of the three categories. Then classify the data in each location (e.g. level of sensitivity and risk) and write this down as well. Only when you understand what data you have and what risks you face, can you start to think about controls.
How can I keep my sensitive data secure?
1. Portable encryption
You should be encrypting any sensitive data which leaves your network. To do this, you need software systems in place since you cannot rely on employees alone. It only takes a lost USB stick, laptop or phone to deliver a severe blow to a business.
2. Endpoint protection
Data endpoints are the machines your employees use, e.g. desktops, laptops or mobiles. It’s on these devices that intellectual property and sensitive data resides or passes through.
Endpoint solutions allow administrators to control what devices are in use. They also let them see when they’ve been used, who by and the information which was accessed or downloaded.
Businesses should also have security policies in place governing the use of devices. Since employees store sensitive information like emails or documents on their smartphones and tablets. Your security policy must cover areas like password complexity, downloads and screen locks.
3. Email content control
As users often send confidential information and documents via email, it has a high potential for a data leak. Using content filtering allows deep content inspection technology to scan for potential threats. Email text, images and attachments can all be scanned this way to flag up potential leaks.
Content filtering can also alert administrators of insider threats. Informing them if users try to send restricted material outside the business.
4. Intelligent firewalls
Alongside email, IM and Internet use also present a risk to your data. Firewalls can protect individual computers and whole networks from security threats. But they can also take automatic action against potential data leaks, unauthorised access or malicious behaviour. This is achieved by notifying the administrator or by blocking the action.
5. Device control
It is now expected that employees will have a smartphone on them at work. For DLP, this means it’s much easier for employees to take away confidential data.
To limit this, you need to have security policies in place governing the use of devices. Your policy must cover things like password complexity, download and application guidelines, and screen timeouts. Without a policy like this, sensitive data will be at risk once it enters an employee’s device.
6. Assess security permissions
Many businesses give employees far more access than they need. Taking a Zero-Trust approach to access permissions helps address this. Zero trust means people only have access to what they will need on a day-to-day basis.
This approach allows you to limit the scale of leaks and prevents employees from accessing sensitive data. You should review your current security permissions and see who has access to what. Then create access policies that limit employees’ network privileges to only what they need for their job.
Your system should also issue alerts if employees act out of the ordinary. For instance, if they start accessing large numbers of documents. Or if a user tries to access restricted documents. These are often signs of a script running or a compromised account.
7. Control print
Multi-function printers (MFPs) are typically unmonitored and so have high data leak potential. Requiring users to sign in before use can reduce this, as they will only have access to certain functions. This also prevents leaving documents on the printer, since the document only prints once the user signs in.
8. Secure back-ups
Backing up important information is a fundamental part of business. But backups can be vulnerable too and are often troves of sensitive data.
As with the original files, your should encrypt your backups. It’s also important to ensure backup servers are not publicly visible such as through the Internet. This makes it harder for attackers to attempt to gain illicit access.
9. Image text analysis
It’s not only documents and text which you need to protect, images can be sensitive data as well. The prevalence of camera-enabled devices, like smartphones, in the workplace has made copying images simple. DLP solutions have the ability to analyse text within images, preventing data exposure.
10. Educate users
Businesses often assume their employees know what information is confidential and what can’t be shared. But data leaks aren’t always malicious and an employee may not even realise their behaviour is putting the company at risk.
It’s useful to educate your users on the dangers of data leakage. You should include it as part of your onboarding process at a minimum. And should carry out sessions on a regular basis to ensure everyone is aware of the dangers and up-to-date on company policy.
A good security policy will be well-defined and easy to understand. Without this, people won’t adopt it since accountability and employee’s roles will not be clear.
The GDPR and data protection
A further consideration is the EU General Data Protection Regulation (GDPR). Although the UK has voted to leave the EU, the new regulation may still apply to your company. So you should review your data protection policies and technology to ensure you are compliant.
The GDPR focuses more on what the data is about, not where the data lives. So even if you operate outside of the EU, the new regulations could still apply. GDPR rules that if your business offers services to the EU market or holds data about EU citizens. You will need to be compliant.
When it comes to data, your business should be proactive about its protection. Keep your security solutions up to date, and don’t be afraid to reach out to a consultant for advice.
The story
At 27 minutes past 2 on a Monday afternoon, the phone on my desk rang. Picking it up I was greeted by Faye Langford (a name I was unfamiliar with) asking if she could speak to the company’s CEO, Robert Rutherford. She said she was calling from one of our suppliers (which has been left intentionally unnamed) about an earlier email regarding problems with a credit card.
As Rob was out of the office, I asked if there was anyone else who could help. I was informed that Rob was the only person on the account and so I told Faye that I would pass on the message. She wished me a good day and that was the end of our conversation.
I emailed Rob the details of the call and was content that the issue would be resolved now it was in the appropriate hands.
This all seemed quite ordinary but here are two things which change that:
- There are two people at this supplier who would normally call us regarding card information. Faye Langford is not one of them.
- There are over 15,000 employees who work at this supplier. Faye Langford is not one of them.
So, what had just happened?
The scam
What had happened was an attempt at voice phishing – also known as vishing. When you think of phishing, you probably think of emails but unfortunately, phishing can occur on any channel. Phone calls, SMS or social media are all platforms which scammers can use to fraudulently acquire your details.
But there are some things which make this attempt particularly alarming.
- They already knew Rob’s full name and that he was the company’s CEO
- They knew that we use this supplier and are familiar with the name
- They didn’t probe further when asked if there was anyone else at the company they regularly spoke to
While the information in point one is widely available – on LinkedIn and the company website – it serves as a reminder that scammers will use personal details to make their attacks more targeted and realistic. Had Faye asked to speak to “the CEO”, I would have delved much deeper into what the purpose of the call was. But since she was on first-name terms and was purportedly calling from a known supplier I was more inclined to trust her.
The second point is alarming because it’s narrowly accurate. Since the supplier is well known and works with many companies, this may have simply been a fluke. Alternatively, this may be an emerging worst-case scenario. It’s possible that the supplier has at some point suffered a data-breach and had client information leaked. This would explain how they knew we worked with that supplier and may have been the source of Rob’s details as well.
As it turns out, a few days preceding the call from Faye, the supplier had suffered a data breach. This breach included client’s names, job titles, and partial payment information including cardholder name and card type. This makes it hard to doubt the two events are unrelated.
The third and final point is the most alarming whilst also being seemingly insignificant. When Faye called, she wanted to speak with Rob and was clear that no one else could help when told he was unavailable. This indicates that the scam wasn’t just a scattergun approach but targeted at Rob specifically. Considering that cardholder name was part of the data leaked in the breach mentioned previously, this may be why.
How do vishing scams work?
Based on the articles covering the breach, the information given during the call and other attempts we’ve seen before, the scam would have likely gone like this:
The supplier’s data is breached and acquired by cyber-criminals. This may be sold on a dark-web marketplace to the scammer or the scammer might have been the one to directly take the data.
The scammer creates a fake email pretending to be from the supplier and sends it to the target company stating they need to resubmit card details due to ‘an issue’. This email may include a website link or telephone number to ‘update’ the card details – both of which will be fake.
(I should note that we never actually discovered an email. It’s possible that it was blocked by our email security system due to coming from a known malicious address or linking to a known malicious URL. Alternatively, the email may be entirely fabricated and only used to imply there’s ongoing communication and build trust in the call.)
The scammer now calls the organisation and requests to speak to the target regarding the email about card information. Once they reach the intended target they would likely say that there’s an issue with billing and until the card details are resubmitted, all orders will be frozen and no additional payments can be made.
If the target is worried by this and not suspicious of the request, they will likely be happy to hand over their card details to resolve the issue. The scammer would then check the details are real and maybe say something like “Excellent, I can see the payments are going through now.”, before hanging up.
How can you protect your business from vishing?
Undertake user training
You’ve probably heard this reiterated a hundred times before, but one thing often left unmentioned is that you must ensure your training program is grounded in the scope of the business.
The more abstract training is from employee’s day to day roles, the less engaged they will be and the less they’ll remember. A simulated vishing call against employees whilst in the workplace is not only realistic but will likely leave a lasting impression – making it incredibly valuable.
Don’t rely too heavily on caller ID
Caller ID allows you to put a name to a phone number and identify who’s calling. This sounds like a useful tool in preventing scammers masquerading as someone they’re not. But caller ID can be easily spoofed to show what the scammer wants to show.
There are many online services which offer caller ID spoofing – making it easy for scammers to take advantage of the trust a caller ID can give. This doesn’t mean caller ID is completely useless though as it can be helpful in filtering out nuisance calls, but you should not blindly trust the system.
Don’t respond to requests for details
It’s easy to say this, but if it were easy to do, vishing wouldn’t exist. To keep your details secure, you must get yourself and your employees into the mindset that unless the request is coming from an official channel which the caller can prove is genuine, don’t divulge company details.
Establishing and enforcing acceptable channels of communication for clients can make this much simpler. If you establish in company policy that certain details may never be communicated via certain channels (i.e. never disclose a mobile number over email), it’ll be far easier to stop scammers who are trying to siphon information out of the business.
Take the time to check
If there’s a suspicious call about an urgent bank transfer or new card details, get approval on whether it’s genuine off the phone and ideally face-to-face with who usually deals with the issue (e.g. the finance director). If the caller is genuine, they won’t mind you taking the time to check and if they aren’t, checking is a good way to avoid a disaster.
It’s worth building this approval process into policies so that people know who to go to for each request. Having the process in company policy also shows that asking about the authenticity of a suspicious request isn’t something for employees to be worried about doing.
Employ zero-trust
This policy sounds severe, but zero-trust simply means employees who don’t need to know something, aren’t told it. If you store credit card details in a secure digital wallet which everyone has access to, it only takes one successful vishing call for those details to be compromised.
If only the finance department has access to those details though, it’s much harder for a scammer to get lucky off an unaware employee who was trying to be helpful.
Establish and communicate a list of acceptable requesters
Like with establishing acceptable channels, you should ideally have a list of names for which it is acceptable to give details to. If you’re employing zero-trust, this list only needs to be known amongst those who have access to the details; otherwise, you’ll need to communicate it to the entire company.
… To summarise
Before this experience with vishing, I had only experienced it once before and it had been a rather poor attempt (a very robotic voice asking about the ‘accident’ I had been involved in). I had been fairly certain that this was the way vishing would stay – easy to spot, scattergun and done by text-to-speech. But this latest call has unfortunately proved me wrong.
Not only was it done by an actual real human, but it was pointed at a very specific individual. This is a trend which mirrors the evolution of other cyber-attacks and the increased weight cyber-criminals are placing on social engineering in their toolset. Whilst this threat is old and not uncommon in high-end security breaches, it seems it’s now also coming to the masses.
If you’re uncertain about whether phishing, vishing or any other type of cyber-crime is happening on the scope and scale it’s reported at, I hope this experience opens your eyes to the reality of what’s happening. It certainly did for me.
Lurking deep beneath your surface IT infrastructure is a malignant force. Its creeping tendrils extend into every department of the business and like a rot it spreads.
Whilst it started out innocent, as it grew more prevalent it’s evil nature emerged. Twisting roots buried deeper into the IT environment, corrupting business processes. Tendrils probed out, undermining defences whilst creating unseen vulnerabilities. And a maw guzzled and swallowed all the data it was fed.
But the worst part of all about this malevolent infestation is this. It wasn’t an attacker who planted this thing in your network, no. It was you.
And you continue to let it grow, feeding it and adding to it, all whilst unaware of the peril you have created…
Okay, whilst that description was a little dramatic, shadow IT poses an undeniable risk to your business. Gartner predicted that 1 in 3 security breaches will be the result of shadow IT applications by 2020. And Research from Cisco indicated CIOs underestimate the amount of shadow application running on the network by a factor of 14. That is to say, the CIO thought the business was running 51 cloud services when in reality it was using 730!
These stats highlight how many businesses still don’t have a grasp on the extent of their shadow IT. The risks and controls have been around for years, yet many businesses wait until they get burned to take action.
What is shadow IT?
Shadow IT is hardware or software (often cloud-based) used by staff without knowledge or approval from the IT team.
Shadow IT can present itself in many ways, a few examples being:
- Staff sharing files between themselves, suppliers and customers. Often with a cloud file store such as OneDrive, Dropbox or Google Drive.
- A member of the sales team using an online CRM solution to work on a campaign.
- An account manager using a personal Skype account to conference with clients.
- An employee using an online tool from their previous job, instead of the software their current employer uses.
In each example, it’s obvious that these systems will be outside of the control of the IT department. This is a concern because it increases the business’ attack surface and adds many fun and exciting ways in which your sensitive data could leak.
Shadow IT plays on the idea of “if you can’t see it, you can’t control it”. As a result, it creates a lot of invisible risks and security gaps which the IT team is unable to address.
Of course, shadow IT may be bringing in benefits to a business. If an employee is more comfortable with their tools, they’ll work more effectively. But allowing it to run wild introduces gaping security holes and puts you at higher risk.
Why does shadow IT occur?
Shadow IT arose with the boom in cloud-based technologies and applications. This application explosion allowed employees to gain access to IT solutions through a web interface. And with so much variety, employees could buy an entire suite of tools with little no involvement from the IT department.
The popularity of having sudden access to a plethora of applications was compounded by the fact that in the past, IT projects would have to stop or grind their way through the IT department before becoming usable. Whilst this wasn’t done with malice, the delay it caused frustrated power users who wanted rapid solutions to their issues.
In short, the demand for change was louder and faster than the IT team’s resources, and even their awareness. Technology had come to the masses and they wanted to use that technology. Now.
But blaming everything on the IT department isn’t fair and nor is it accurate. Another fundamental cause of shadow IT is misalignment within the business. Something which involves many departments and generally the board.
A lack of control on the IT estate tends to make identifying a single reason for shadow IT impossible. This means the cause for shadow IT can vary from business to business.
How can I manage shadow IT?
Whilst the idea of prohibiting the use of any applications outside of an acceptable list seems like it would work fantastically, it doesn’t.
Not only will it annoy employees and disrupt their workflows, but people will likely find a way around the filtering or will pester the IT team to add certain applications to the whitelist. Circumventing the point of the system in the first place and only resulting in a net negative.
Instead, the business needs to address the root cause of its shadow IT by installing policy controls and technical controls to reign it in. Here are 7 simple steps to give you an idea of where to start.
1. Review what’s going on
The first step is to use your internal monitoring and control solutions to analyse who is going where and doing what. It’s also worth auditing laptops and desktops if you allow users to install applications on their own devices (not advisable!).
2. Evaluate and prioritise risk
Go through your reports and work out which shadow IT elements pose the greatest risk. Staff sharing sensitive information or accessing the dark web through .tor browsers should both be big red flags.
Whilst doing this, you may also find out you are breaking regulatory obligations without evening knowing it. For instance, by storing files in regions that are unacceptable.
3. Lockdown
Shut down anything that is dangerous or breaking regulation immediately. If it’s illegal or breaks company policy then block it and take appropriate action at a management or HR level.
4. Give an amnesty
Once you’ve dealt with the immediate dangers and know what’s going on give everyone the chance to stop using the unapproved shadow IT applications.
Give them a week or two to alert you why certain applications are necessary and you can then manage the exceptions. After the week is up shut everything unapproved down.
5. Manage relationships
As you work through this process, take care to manage the external perception of the board and IT. People often use shadow IT to better fulfil their roles. So you should be trying to understand why they are using it and how you can fulfil their needs.
You may even find that some shadow applications are of benefit elsewhere in the business and adopting them could be a net positive. You don’t want to turn the business against the IT team as everyone then suffers.
6. Create policies
It’s unlikely that regular employees are aware of the danger of shadow IT and why they shouldn’t use it. Clear policies with training and regular reminders should help minimise risks.
7. Continually manage
You should always be monitoring and evaluating what’s going on in your network. People forget what they’re told, and the odd employee does go rogue. The technologies are out there and are nothing new. So there’s no excuse for not monitoring and blocking employees from doing things that could harm your business.
Email archiving brings benefits to every department throughout a business – from finance and legal, through to administration. One department which can benefit from email archiving is HR, as they deal with personal data every day.
Three benefits of email archiving for HR Managers
1. Investigate claims of bullying in the workplace
You may think this doesn’t happen in your workplace, but it’s something you should be able to investigate. Research carried out by the TUC shows that 29% of people have been bullied at work. Email records are important in cases of alleged verbal or physical bullying, as they’re difficult to prove.
An email archiving solution that captures every email provides HR managers with the transparency and visibility required to conduct a fair investigation in the event of a complaint. It’s more reliable than relying on employees to archive their messages on an ad-hoc basis. A solution with user-based security permissions is ideal as HR Managers can investigate complaints without the involvement of the IT department.
2. Monitor for email misuse
A company may find itself in the midst of a legal dispute if employees misuse corporate email. This could range from sharing offensive material to accidentally hitting the “Reply All” button. It is not enough to rely on your employees to use common sense when it comes to email etiquette, and it could result in legal action against your company – as seen in the case of Thales Australia.
One way to ensure employees are aware of your business’s email usage policy is to send a copy of the guidelines via email. Then ask employees to send a reply stating they have read the policy and agree to abide by it. Your email archive will save the reply, so you have a record available should any dispute arise. Using an email archiving solution means you will also have a record of any inappropriate work emails, even if the employees sending and/or receiving them delete the messages from their inbox in between system backups. Emails are time-stamped and digitally fingerprinted at the moment of storage and retrieval so you can guarantee accurate data. Which is essential if these emails are being presented as evidence in a tribunal.
3. Ensure regulatory compliance
You must keep former employees’ records for the duration of employment and for six years after you terminate employment. This includes items like training records, appraisals, contracts, annual leave, sickness records and disciplinary warnings (even if these have since expired). You have to keep these because an Employment Tribunal, County Court or High Court claim is possible for up to six years after employment ends. So the business could be at risk for failing to produce these records. Also keep anything that relates to the employee, which an Employment Tribunal may require as evidence, for this retention period.
Documents are a business asset. If an asset is lost, stolen or damaged, it becomes a risk. Both for the business and for their client.
This means having control systems in place to understand these risks is critical. And having the controls to counter them is equally as important.
It sounds simple. But after a decade of working with businesses, it’s clear that few of them have suitable controls in place. To address this, we’ve created 10 points to guide you through the process of creating your information classification policy.
1. Keeping it simple
When looking at security in any way, it’s important to keep it as simple as possible. This is particularly true when it’s something so regular as dealing with documents.
To make it simple, businesses need to invest in technology. In this case, there are three main technologies worth investing in:
- Document / Content management
- Data leak prevention
- Rights management solutions
A document getting into the wrong hands is going to cause your business, or a client’s business, damage. That is a fact. So aiming to implement all three is the best way to get a comprehensive solution.
2. Mapping your classifications
Before you get into classifying documents it’s important to ignore technology. Technology comes after you have decided the policies and processes you wish to follow.
What this means is that you need to map documents or types of documents into distinct groups. To do this, you should look at two key areas: the sensitivity of the document and their intended audience. This information will make up the foundation of your Information Classification Policy.
Many businesses already have classifications in place. But they’re often created, implemented and forgotten – quickly becoming unusable without weeks or months of additional work. You need to create an Information Classification Policy and not hide it away. It needs to be clear and easy for everyone to work with and conform to with little effort.
3. Building the Information Classification System
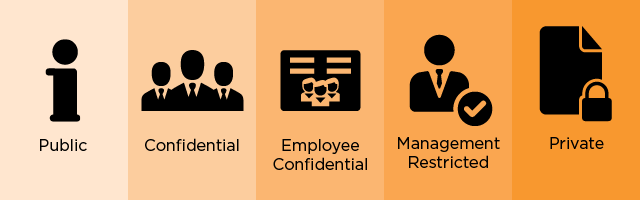
The foundation of any Information Classification Policy is categorising information. Here are a few example document classifications that will fit most business requirements:
- Public: Documents that are not sensitive and there is no issue with release to the general public i.e. on a website
- Confidential: Documents only to be viewed internally or with third parties that have signed a non-disclosure agreement
- Employee Confidential: Documents only to be viewed by employees at the company
- Management Restricted: Documents only to be viewed by the senior management at the company
- Private: Documents which contain personal information (useful for managing GDPR compliance)
In general, you don’t want to go over 10 classifications because classification should be as simple as possible. If you find that you have too many classifications, consider only looking at sensitivity or only looking at intended audience to begin with then filling in any gaps.
4. Assembling the Information Classification Team
A policy needs board-level support to ensure the business buys into and uses it. Once you have this, you should form a team which includes key departments in the business to enforce the policy.
This team may include people from technical, HR, legal and any other departments that are suitable for your industry. An appropriate team will be able to protect a business from security breaches whilst letting people access the information they need. And whilst it is important, the technical solution should be the last point to consider.
5. Designing the Information Classification Policy
Once you have your team assembled, you need to start going through your documents. In most organisations, it can be hard to know where to start.
To solve this, you should group documents at a high level. Looking at the impact that a data breach of that type could cause. Focus on the most sensitive document types first. And once that’s locked down, you can move through the less sensitive list.
When going through this process there are a few tips you can follow.
For company documents, it’s advisable to put your company name first. This helps them stand out from any other classification, i.e. from a client or a partner business.
It’s also useful to colour code classifications to help distinguish documents by eye. This helps you identify a sensitive document that’s left on a screen, printer or vacant desk. The beauty of colour classification is that it aids you in taking action internally or externally. It’s simple to prove that the defendant knew the information was restricted.
It’s important that you make it easy for staff to label and classify documents. If it takes more than three clicks to label a document, staff will find ways to circumvent the system. People naturally take the path of least resistance. So if your system is obtuse, employees will find ways to bypass it.
6. Enforcing control with automation
Once you’ve designed the Information Classification System, it’s finally time to look at the technology. Automation is very helpful to ensure enforcement. You shouldn’t rely on people alone as things will drop through the cracks.
It’s important that any technology links back into the core authentication system within a business. This will typically be Active Directory – the system you use to log in to your PC at the office.
Doing this simplifies things as you can use existing user groups to give access to certain classifications. There’s likely to already be an Active Directory group called “Board Members” for example, which you can use straight away.
Of course, grouping people doesn’t guarantee a user will know who they can and can’t send specific documents to. Nor will it prevent them from sending a document to a recipient by mistake.
This is why a business should be using a Rights Management system. Rights Management ensures that the systems know who has permission to access the document. So even if someone does send a restricted document, the recipient won’t be able to view it.
7. Educating employees
One of the largest reasons for data leakage is employees. Make sure to train them on how to use systems and refresh them periodically.
Also educate them on any security risks to the business – known, current or potential. They need to understand why following policies is important and how not following them can impact the business and therefore them.
8. Controlling leavers
So many organisations do not manage ex-employees. It’s important to disable their accounts once they leave the company. Even if they left on good terms, it’s best not to take a risk.
Loose accounts complicate the system at best and act as a open hole for attackers at worst. Hackers or insiders can hijack old accounts and make use of the access privileges. So you need to shut down accounts or strip them of all access rights to reduce the risk to your data.
9. Continually improving
It’s best if you adhere to common processes and document them somewhere accessible. To do this, you need robust information classification and risk policies that integrate with a wider standard. A good example to use as a framework is the ISO 27001 standard.
Doing this ensures that you assess and improve how you are controlling your risks within the business. Keeping you protected from an evolving threat landscape.
10. Widening the focus
It would be ridiculous to only focus on document security whilst ignoring the other risks to your business. So understanding all the risks your business faces and assigning suitable controls is something you must do.
Again, the ISO 27001 standard is a good framework to use for managing your information security on a wider basis. But this shouldn’t stop you going ahead and dealing with document security first. Getting this done will make things easier in the long term.
Summary
Businesses must control their risks, as failing to do so has catastrophic consequences. The key is to start simple and then improve. You don’t have to adopt everything at once.
A good starting point is to understand the sort of data you have and then classifying it. A good percentage of your business information could be used to extort or embarrass you. Or even worse, a client.
Once you’ve got your classifications, tie them into document templates. Then automate management and workflow automatically with technology. When done right, businesses can dramatically improve their security since it’s embedded onto the asset. Rights Management can then control who can edit, copy, paste, print, email, transfer or view it at a later date.
Once in place, this can be overlaid with network controls such as Data Leak Prevention. This watches documents flow in and out of the business and can isolate, sandbox or alert relevant people that a breach may occur.
To take it further, systems at the perimeter, such as gateway encryption solutions, can identify sensitive information. Encrypting it to ensure it won’t pass over the open Internet in clear text.
The list can go on but it’s important you start at the beginning by creating an Information Classification System. You need to understand what you have and what the risks and potential controls are first though.
Any device where data is downloaded or stored is at risk of being accessed by a third party once it is no longer in your possession. Devices at risk range from the obvious hard disks, right through to printers.
The basic principle is: if data is written it can be retrieved unless it’s encrypted. Therefore, if you’re in an industry where your clients’ data is sensitive (which is to say, every industry), if you can encrypt the data you should always do it. Of course, you need to factor in performance overheads in relation to encryption but that is becoming less of an issue now with the entry of technologies such as solid-state disks and self-encrypting storage arrays. Encrypting data effectively removes a lot of the concerns around the disposal and/or loss of a device.
If you do have to dispose of a device then it is usually best to have it done by a third party specialist data destruction firm. However, you need to be aware that by choosing to outsource this function, you are not outsourcing all responsibility. If a client’s data were to be stolen from one of your disposed machines, it’s your brand that will be tarnished, therefore you have to do your due diligence. Assess the data destruction firm and assess your risks. Do not simply settle for a van turning up to remove the worry.
Once you identify the risks you should have them signed off at partner level and agree on a strategy to apply suitable control to minimise them. If you can follow these steps you can be pretty sure that your clients’ data and your firm’s reputation will remain safe.
Don’t think that PCs are the only source of data that can unintentionally (or maliciously) disclosed to a third party though. You should also have security and disposal policies covering the following:
- PCs, laptops, tablets
- Mobile phones
- Printers
- USB storage devices
- CDs/DVDs
- Servers
- Hard disks
- Backup tapes
- Cloud storage
Again, all of these items can be encrypted and, arguably, they all should be if your data could cause your firm or a client embarrassment.
Risk of extortion
Never think that your information is not of interest to a third party. A large proportion of data and security breaches are now focused on blackmail and extortion. Hackers hack for money now, not simply for fun. A hacker doesn’t have to come in over the wire, getting hold of a physical device littered with information will give them extortion material and valuable clues on how to breach network defences at a later date.
Your key considerations
So, what are the key things to consider in relation to ensuring data is destroyed after its useful life? In this article, ‘destruction’ refers to physical destruction (shredding) and ‘wiping’ to cleaning the data off securely, to retain some resale value to the firm or a third party.
1. Control access
As you can imagine, it’s possible that, if you leave a pile of hard disks or USB keys in an uncontrolled area, once could go missing. And if this happened it would be open to all risks. When you have set aside equipment for disposal then secure it away from general access.
2. Control / document assets
Make sure your asset lists are up to date so when you wish to ensure any data is destroyed you don’t miss anything. If you aren’t controlling your assets then you aren’t truly controlling the risks. When you do dispose of an asset, ensure the information is logged, including the device, serial code, how it was sanitised, by whom, when, where it went, etc. If you go to a third party it should provide you with a certification of destruction.
3. Destroy the data
If you just format or delete the data on a device it’s relatively simple to pull it back. If you want to ensure the data is irretrievable then you can use specialist tools to do so. You can start by looking at tools such as Kroll Ontrack and Blancco if you want to do it yourself. If you want to go belts and braces, encrypt the device storing the data and then run the secure erase tools. You then, of course, need to factor in the time required to undertake this work. It all comes down to how sensitive your data is.
4. Destroy the device
In some circumstances, the data is so sensitive that the entire device should be destroyed, shredded in fact. Generally, you would outsource this, but you can also buy the specialist equipment to do it yourself. Typically memory and hard disks are shredded, and other parts of the device sold on to retrieve precious metals. There are strict environmental guidelines on disposal of equipment so be sure to familiarise yourself with the current regulatory requirements if you do it yourself.
5. Destroy it quickly
Once you have identified equipment to be disposed of or wiped, then do it quickly. The longer devices hang around, the more chance they will fall out of control or go missing. You would typically expect to have a periodic destruction cycle or pick-up if using a third party.
6. Have a process
Ensure you have a documented process for the destruction of data and devices as required. If you don’t have a rigid structure, things can and will slip through. Generally, legal firms can’t risk that happening so controls and processes must be put in place and followed. Failure to follow procedures must have tough disciplinary repercussions.
7. Check third parties
If you are outsourcing the destruction of data and devices to a third party then ensure that you are careful in your choice. There have been press reports of devices turning up on sites like eBay with very sensitive data on, even on a printer’s internal flash disks. So, when choosing a service provider, you should be looking for companies with ISO 27001 and ISO 14001 certification as a bare minimum. Also, it helps if they are certified to destroy MOD equipment, e.g. CESG and MOD approved. The higher-end secure destructions firms will also have the equipment they can bring to your premises or premises you can visit to witness the destruction of your data devices.
8. Communicate and review
Once you have a process and policies in place to relation to wiping and destruction of data and devices then ensure that it’s communicated and clearly understood. Make sure all relevant areas of the company understand their roles. Also once created don’t just forget about the policies and processes, review them at least annually. Your assets will change, as will the risks. Ensure that you review them regularly and know what they are
Security is changing
As we look back over this tiny area of IT security, the case for ISO 27001 is becoming more and more important in law firms. The risk of a security breach of any kind can have serious implications more so now than ever before. ISO 27001 will give a firm a framework to identify all risks and assign appropriate controls to mitigate them. It will also give your firm a continual improvement methodology that will deliver gains year on year. It should also be noted that many clients are now demanding ISO 27001 certification as a standard before instruction.
As a final note, just do remember that your data is of interest to many people. Don’t take risks, or at least don’t take them without informed sign-off from your firm’s partners.
How can employees’ internet usage put your business at risk?
1. Security risks
An employee browsing potentially dangerous websites without control can open your business to an array of security risks, such as viruses, trojans, spyware – the list goes on. This is because non-work related websites are a major feed of dangerous exploits into the network. These obviously risk to the individual PC but we’ve also all seen the news articles about private companies and the public sector being down for days when a nasty virus gets into the network. I’ve seen this myself a few years ago where the whole IT team and the CIO of a company were flying around the world trying to eradicate a virus that was flooding the network and killing communications.
Your risk also grows as uncontrolled internet access also allows employees to send information in and out of your organisation without control. This can be intentional via webmail or web messenger applications, such as MSN Messenger, Yahoo messenger or Skype. Or it can be unintentionally through spyware, phishing or other vulnerabilities.
I see data leakage prevention as one of the biggest reasons to control internet access. I’ve lost count of the number of times I’ve been alerted of a customer’s employee taking a sales database or confidential documents before leaving a company. It is difficult to erase any risk but you can make it difficult. This area really falls out of the topic of this blog – if data leakage is a real concern due to the sensitive nature of your data, or your customers’ data then look into data leakage prevention (DLP) products.
2. Legal liability
If you have copyrighted information, such as software, music, videos, even photo’s on your business network, your business could be legally liable for it. Even if an employee downloaded it onto the network without your knowledge or permission, the business, basically the directors could be legally liable.
Uncontrolled internet access does, unfortunately, leave the door open to a whole host of legal issues. Creating an ‘Acceptable Use’ policy for your IT will help. An effective EIM system will take that further and go a long way to controlling the issue.
3. Waste of bandwidth
Your internet connections are typically the main artery for your business, the main communication line between your business, its customers, and its suppliers. If your employees are downloading non-work related files, listening to music or watching the news then you’ll be paying for that. What do you do when people say that internet browsing is slow? You typically put your hand in your pocket to ‘upgrade the line’.
I can tell you that in at least 70% of cases that I come across when people tell me they need to upgrade connectivity (internet or WAN connections) they actually don’t. They just need to route, control and shape the traffic on their networks more efficiently.
4. Reduced productivity
Your employees’ browsing the internet during work time costs your business money. The average employee spends 15 minutes of time browsing the internet during working time (excluding breaks) for non-business related purposes. This may not seem much but that’s 10 hours a day for a 40 computer-based employee company.
You may say that 15 minutes a day, on top of breaks and lunchtimes, is acceptable, and that’s fine. However that’s an average, and I’ve pulled reports showing some users wasting an hour or more a day on non-work-related internet activity.
If you just say that your employees are all on the minimum wage then it’s costing well over £1,000 per week just on browsing time alone for a 40 user organisation, without taking into account loss of productivity thus loss of potential earnings. The potential for a return on your investment in an employee internet management system should be clear from the start.
It’s not about being Big Brother and locking everything down. Why not quota your employees’ internet access for some non-work-related sites or maybe just allow them access during lunch? This can be managed with virtually all Employee Internet Management systems. If you don’t want people using work machines for non-work related tasks then I suggest that you allow access to dedicated ‘internet workstations’ that staff can use to perhaps to book a holiday or to check their bank balance. These workstations can be given their own internet connection or they can be secured from the main company network – most firewalls/networks can do this.
What about social media?
Facebook, Instagram and Twitter? Are these really of any use to an organisation? There will always be exceptions to the rule, but generally, I don’t see why anyone needs access during work hours. You probably wouldn’t be too happy about the whole company sitting on their desk phones chatting to their mates in the day, so why should they do the same through your IT systems?
I was asked if LinkedIn was a security risk the other day, and I guess the question more or less applies to all social media. It does tend to fall under the control of the IT security department, in terms of EIM, as it ‘can be’ classed a productivity killer. It is often bundled into the social media categories with Facebook, Twitter, etc. Is it a risk itself to security? Not directly. You could, however, argue the social engineering card, but that could be done in other ways and you are straying into paranoia territory. There are always exceptions but generally, it’s safe in my opinion.
It all sounds pretty negative but it’s not something to panic about. I do however believe it’s worth thinking about the issues and looking at some sort of control. There are a vast array of Employee Internet Management systems on the market, some more effective, some cheaper and some more expensive than others. The ROI is usually pretty easy to measure and all vendors should offer a free trial to help you gauge the issues within your environment. I should note that I’ve seen Employee Internet Management systems pay for themselves within month 1.
Here’s a list of some EIM vendors
Many vendors now also offer cloud-based services, so you don’t have to purchase hardware and software to install on your own network. Again, your business and its operations will determine if cloud is the right solution. Typically, you’ll probably lose some level of functionality/control with the vendor run cloud-based services over internal hardware/software solutions.
If you want to look at implementing some controls then speak to your IT provider or seek expert advice. All the solutions vary and although most solutions will control Internet access some solutions will be better than others. Fitting the right solution depends on your business and its operations.
And remember it’s not all about the technology. Changing employee’s internet access is a contentious issue and could lead to some unhappy people if not managed correctly. I’d suggest that you explain that the main driver for control is IT security – because it is.
